Integrating Business Continuity Management and Security Operations Centers: A Holistic Approach to Cybersecurity
Introduction
In an era where cyber threats are not just a possibility but a certainty, organizations must be prepared for the inevitable. While Security Operations Centers (SOC) focus on real-time threat detection and response, Business Continuity Management (BCM) ensures that an organization can continue its critical functions during and after a disaster. The two are not mutually exclusive; rather, they are two sides of the same coin in the realm of cybersecurity.

A Top-Down Approach
The first step in achieving a secure and compliant organization is to understand what is crucial for the company's mission. Once that is clear, best practices should be followed. There's no need to reinvent the wheel; the application of common best practices and frameworks can speed up the process significantly. Therefore, implementing your own SOC or creating crisis management processes from scratch is not done in months, but years. Learn from what our customers have already achieved.
- Alignment with Company Mission: Ensures that all security measures directly contribute to the company's objectives.
- Efficiency: Outsourcing to experts allows for a more efficient allocation of resources.
- Comprehensive Coverage: A top-down approach ensures that all stakeholders and relevant areas, including SOC and ransomware recovery, are considered as part of the broader BCM strategy.
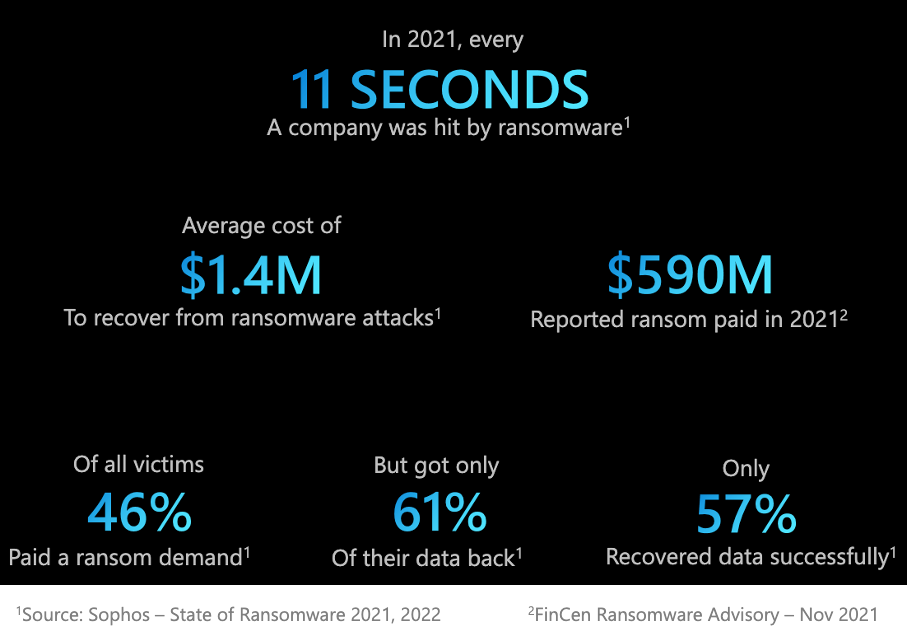
The Stark Reality: Statistics You Can't Ignore
These statistics underscore the urgency of integrating SOC and BCM. Ransomware recovery is not just a SOC activity; it's a BCM concern as well.
BCM is Everybody's Business
BCM is not an IT topic, nor just infosec. The following groups show you why it is important to involve the whole company into the crisis management, and what part IT and SOC play in this scenario.
The Stakeholders
• C-Suite Executives: Responsible for setting the company's mission and ensuring that BCM aligns with it.
• SOC: Detects and responds to ransomware attacks.
• IT Department: Manages the technical aspects, including data backup and recovery.
• Legal Team: Ensures compliance with regulations.
• Employees: Must be trained to follow best practices in cybersecurity to prevent data breaches.
Realistic Scenarios
The following examples show differences and overlaps in SOC and BCM.
Creating a Response Plan
Scenario: A zero-day exploit is discovered affecting your primary CRM software.
• SOC Action: Immediate isolation of affected systems and identification of the intrusion source.
• BCM Action: Switching to a backup CRM system while the primary system is being patched.
Related Capabilities:
• Remote access
• Zero Trust
• Security posture
• Data backup
Preventing Attackers from Getting In
Scenario: Constant brute-force attacks on your network.
• SOC Action: Implementation of rate limiting and IP blocking.
• BCM Action: Ensuring that a backup network is ready to take over in case of a successful breach.
Related Capabilities:
• SIEM + XDR for prevention, detection, and response
• Cross-workload security
Protecting Critical Data from Compromise
Scenario: Insider threat leaking sensitive customer data.
• SOC Action: Real-time monitoring to detect unusual data access patterns.
• BCM Action: Immediate revocation of access rights and switching to a backup data source.
Related Capabilities:
• Internal process/access management
• Data backup and business continuity
Preparing for Natural Disasters
Scenario: A flood damages your primary data center, rendering your infrastructure inoperable.
• SOC Action: Depending on the SOCs responsibilities, notifying stakeholders.
• BCM Action: Activation of the disaster recovery plan, switching to a geographically separate backup site to maintain operations, and initiating recovery procedures for the primary site.
Related Capabilities:
• Geographically separate data centers
• Disaster recovery plans
• Emergency communication channels
• Redundant power and networking
Best Practices
Important actions from a IT and SOC side, to ensure that BCM is only a second option:
Creating a Response Plan
Adopt an internal culture of Zero Trust and assumed breach. Implement a system of data recovery/backup and secure access.
Preventing Attackers from Getting In
Harden the security perimeter by leveraging best-in-class security workloads. Deploy comprehensive prevention, detection, and response capabilities.
Protecting Critical Data from Compromise
Minimize the potential for lateral movement and privilege escalation should an attacker gain an entry point.
Tools and Technologies
Which tools can be involved in the above-mentioned best practices?
• Microsoft XDR and Sentinel: For advanced threat detection and response.
• Azure Backup and Recovery: For robust data backup solutions.
• Microsoft Teams: For real-time communication among SOC and BCM teams.
You find more about these solutions right here.
Breaking Down Silos
One of the key challenges in integrating SOC with BCM is the existence of silos within organizations. These silos can hinder effective communication and coordination. The following picture shows why integrated solutions efficiently help to correlate data and enable the SOC, as well as support a quick recovery in BCM cases

Conclusion: The Imperative of Integration for a Resilient Tomorrow
In the realm of cybersecurity, the adage 'No plan, no recovery' rings truer than ever. As we navigate an increasingly complex digital landscape fraught with evolving threats, the integration of Security Operations Centers (SOC) and Business Continuity Management (BCM) is not just a best practice—it's a business imperative.
Do's and Don'ts
| Do's | Don'ts |
|
|
The Future is Now
As we stand on the precipice of a new era in cybersecurity, Crisis Management emerges as the overarching theme that will envelop both SOC and BCM. In this interconnected world, ransomware attacks are not isolated incidents but warning bells, and table-top exercises are not mere drills but essential rehearsals for the inevitable. The question is not if a crisis will occur, but when—and how prepared you will be.
Final Thoughts
So, as you ponder the future of your organization, remember this: The choices you make today in integrating SOC and BCM will echo in the resilience of your cybersecurity infrastructure tomorrow. Choose wisely, act decisively, and build a future where security is not just a department but a company-wide ethos.


