Tackling Legacy AD Groups with Microsoft Entra ID Governance
When organizations start using Microsoft Entra ID Governance, they often hit a roadblock: thousands of old AD groups that have been around for years. These groups are deeply embedded in internal systems, making a quick switch to the cloud nearly impossible.
The Problem with Legacy AD Groups
- Not directly manageable in Entra ID Governance
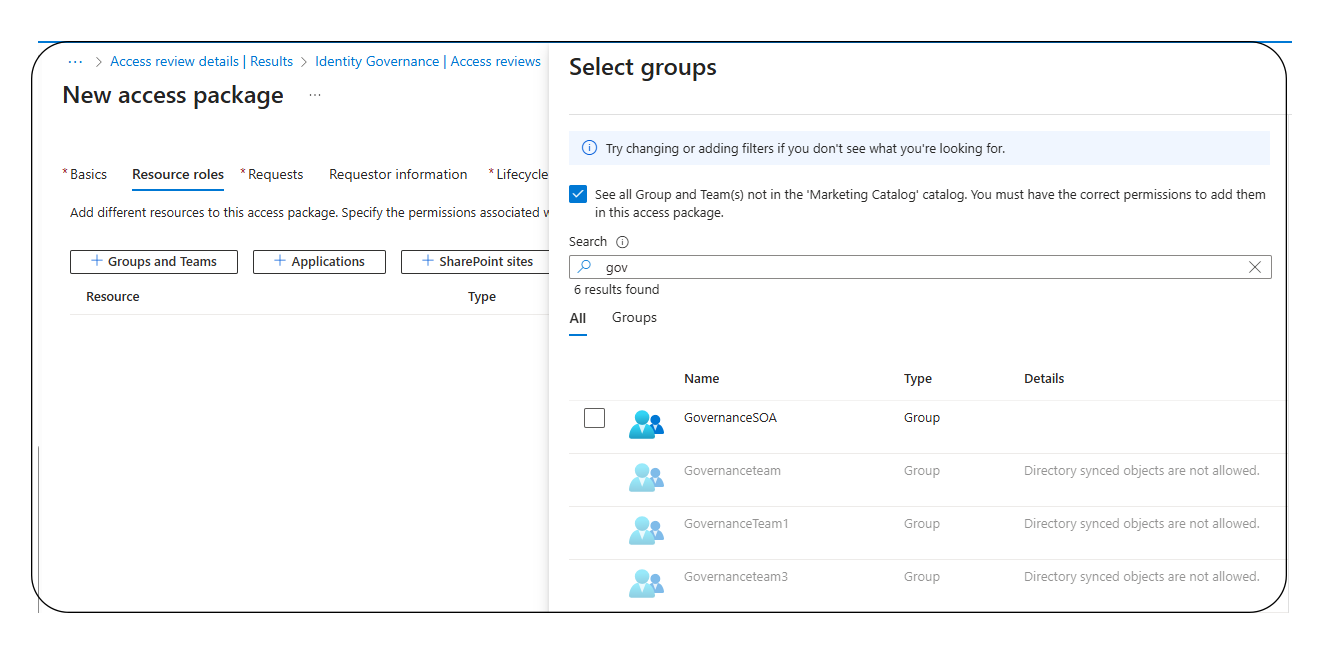
Legacy AD groups cannot be directly added to access packages within Entra ID. This limits your ability to efficiently delegate and manage permissions. - Ineffective Access Reviews
Access reviews performed on AD groups are limited. Users remain members of the AD groups even if their access is denied during the review, making the process ineffective.
Transitioning Gradually to Cloud Management
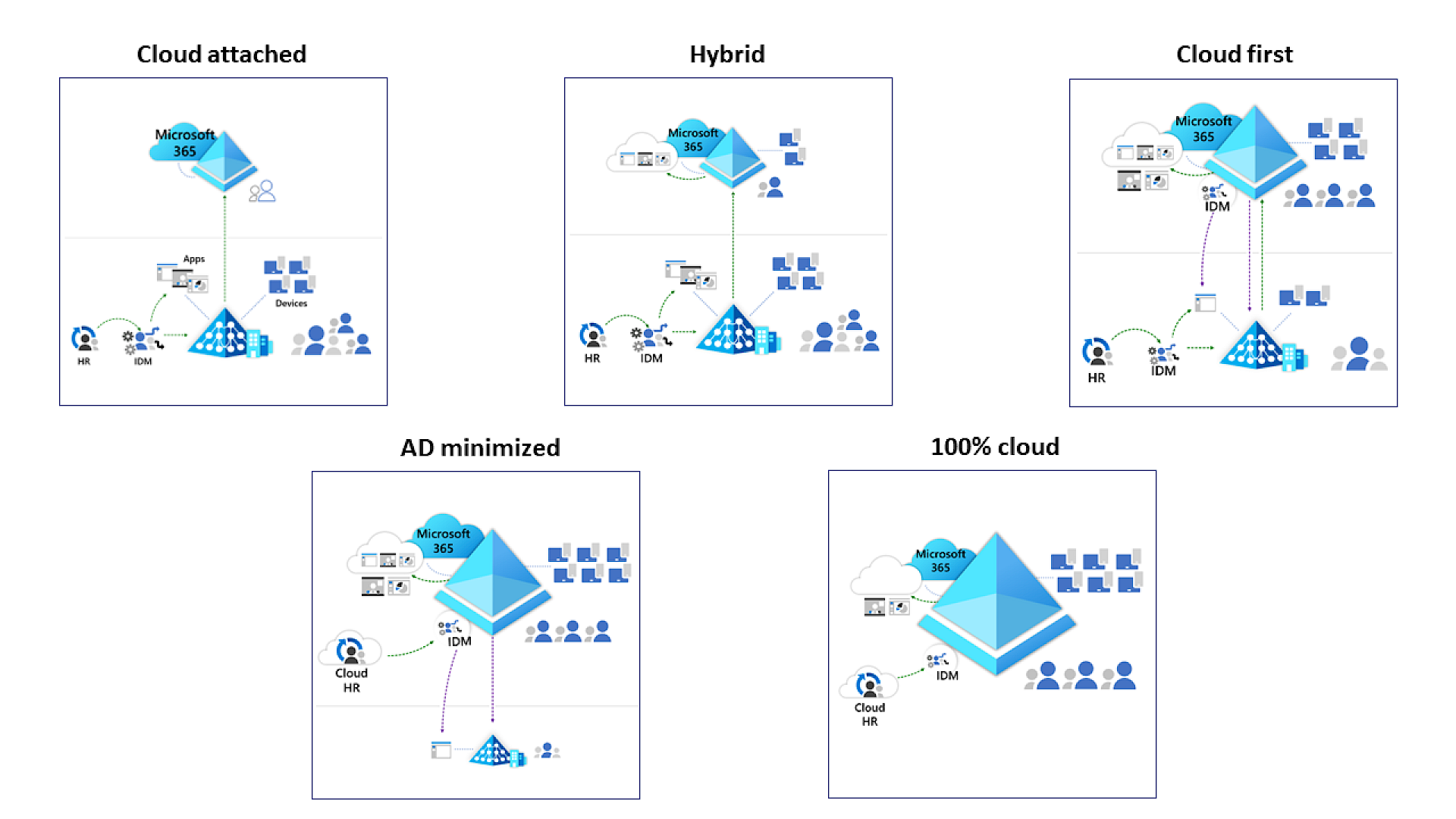
Microsoft encourages a cloud-first strategy, but they know most organizations can’t flip a switch overnight. To support this gradual shift, Microsoft outlined five stages of cloud transformation to align with various customer scenarios and business goals.
An essential component of this transformation is Active Directory Domain Services (AD DS) minimization, which involves progressively shrinking your on-premises infrastructure as your cloud presence grows. Only essential AD objects remain locally.
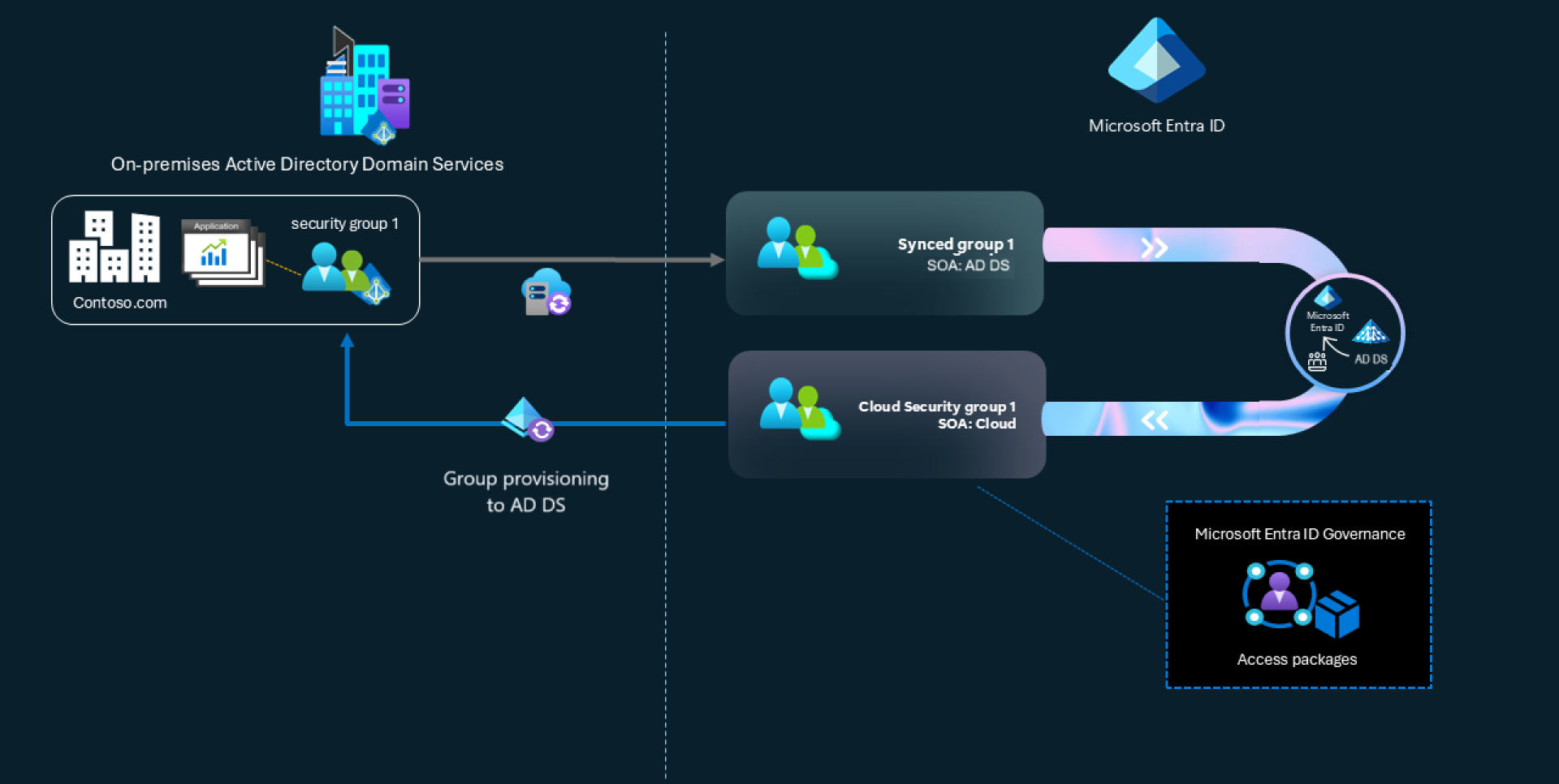
Introducing Group SOA Conversion
To address these challenges, Microsoft introduced Group Source of Authority (SOA) Conversion. It lets you change the "master" location of a group from on-premises AD to Entra ID. Once a group is converted, you can manage it directly in the cloud without having to rebuild everything from scratch.
This gives you the best of both worlds: cloud features like automated access and reviews, a cleaner local AD, and the option to sync back changes if you still need them on-prem.
How to Convert a Group with SOA Conversion
Converting a group to cloud-managed is quick and easy in just a few seconds, and you're done. You don’t need any special tools just use Microsoft Graph Explorer and the right permissions (e.g. Group Administrator).
Here’s how it works
Verify Current Group Source:
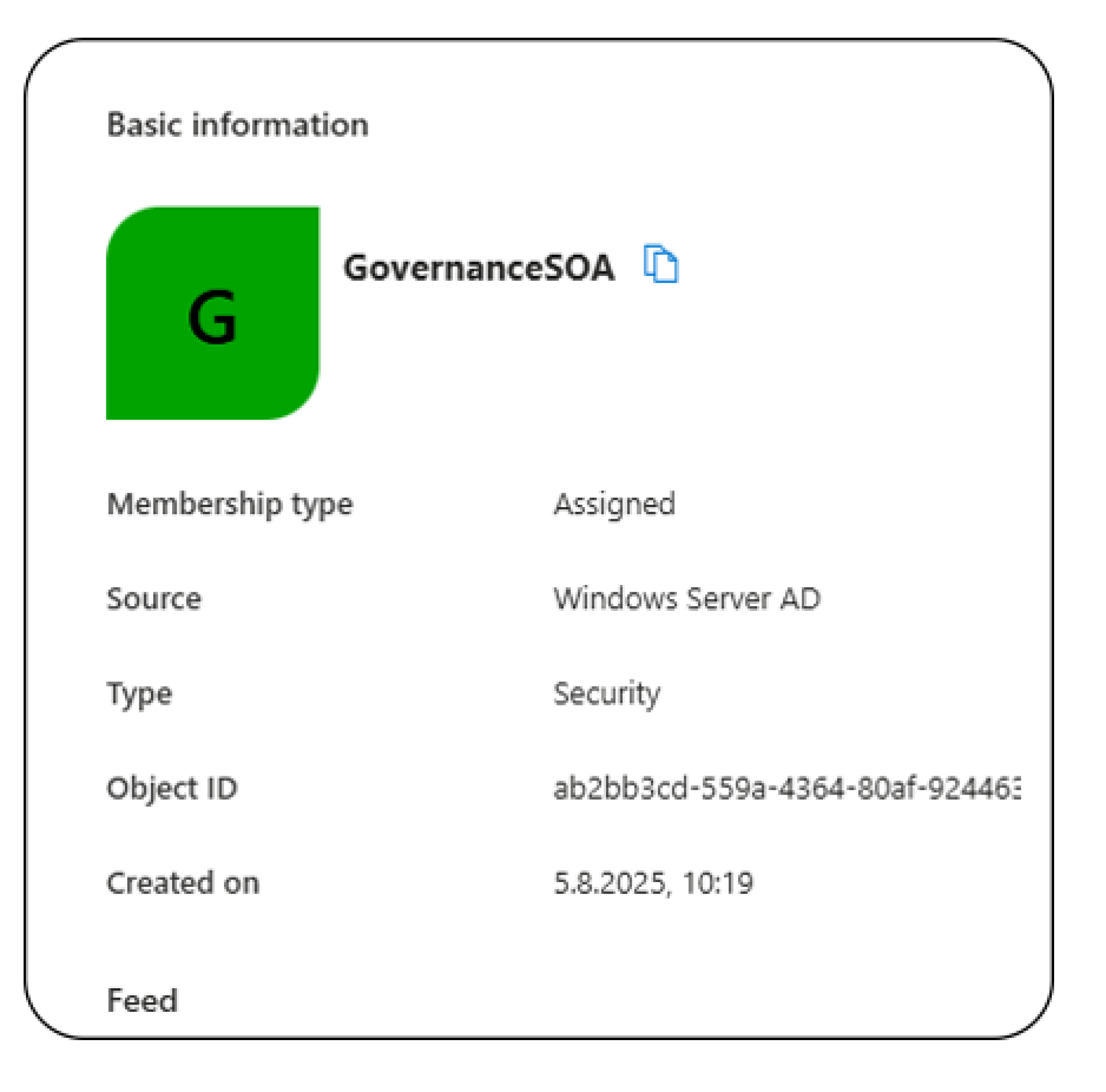
First, check if the group is already cloud-managed
GET https://graph.microsoft.com/beta/groups/{ID}/onPremisesSyncBehavior?$select=isCloudManagedThe response shows "isCloudManaged": false, the group is currently AD-sourced.
Convert to Cloud-Managed Group
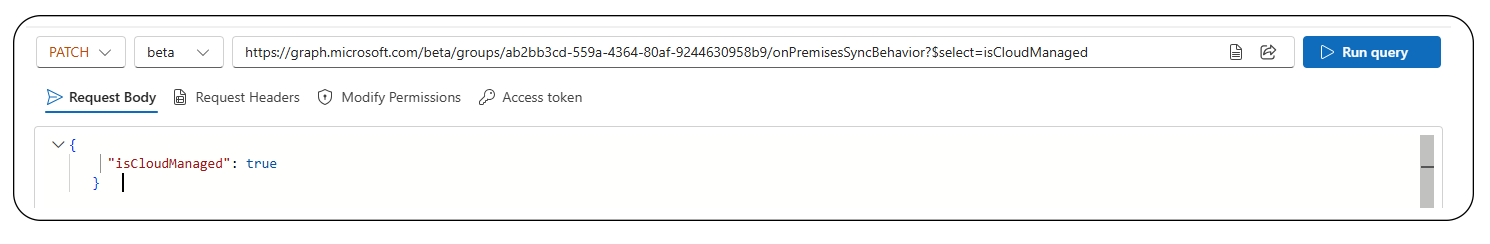
To convert the group, run this PATCH request
PATCH https://graph.microsoft.com/beta/groups/{ID}/onPremisesSyncBehavior
{
"isCloudManaged": true
}
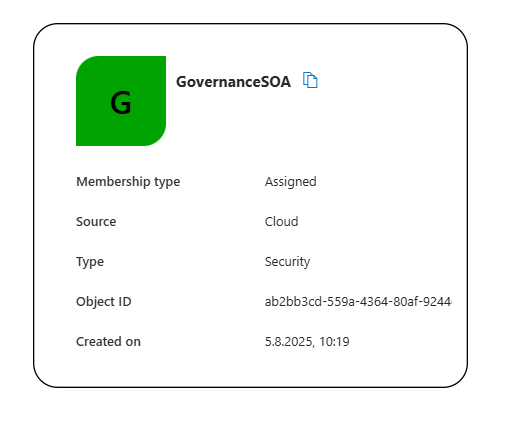
That’s it, your group is now managed in Microsoft Entra ID.
You can immediately start using it in access packages, automate approvals, run access reviews, and manage lifecycle policies fully in the cloud.
For more details, see the official docs: Update onPremisesSyncBehavior.
There are of course some limitations
- No Sync of Local Changes: Changes directly in local AD won’t sync to Entra ID after conversion.
- Nested Group Conversion: Nested groups require separate conversions starting from the lowest-level group.
- Dual-Writing is Unsupported: Changes made in Entra ID won’t sync back through nested AD groups.
- Universal Group Requirement: Groups must be of the "Universal" type before conversion.
- Extension Attributes (1–15) Unsupported: These custom attributes are not available after conversion.
- Mail-enabled Groups: Management restricted to Exchange Online after conversion.
- Distribution Lists: Only convert after migrating mailboxes fully to Exchange Online.
- Self-Service Management: Ensure ownership is clearly defined on-premises before converting SOA.
Conclusion: Taking the First Step Toward Modern Identity Governance
If your organization is still relying heavily on legacy AD groups, Group SOA Conversion offers a practical way to modernize without tearing down your existing infrastructure. It’s especially valuable for hybrid environments that want to start leveraging Entra ID Governance features such as access packages, reviews, and lifecycle automation without waiting for a full cloud migration.
By identifying groups that no longer need to be managed in AD, and converting them to cloud-managed groups, you can begin the journey toward simplified, secure, and scalable identity governance one group at a time.