Security Copilot meets Azure Logic Apps
Introduction
In recent years, the number of security incidents has been on the rise – and Security Operations Centers (SOC) are struggling to keep pace. For new analysts, this means they need more practice and time to investigate and resolve each case. To address these challenges, modern SOCs are turning to automation and AI.
And while there’s been no shortage of talk around this topic, the real question remains: “What does a real-life use case for my SOC actually look like?” That’s exactly what I’m going to show you with the following Logic App workflow.
But first, a disclaimer: what you’re going to see is the current “endgame” of what AI and automation can deliver in a SOC environment. I’ve pushed the limits on purpose to illustrate what’s already technically possible today, knowing that, in practice, this setup might be too costly or complex to implement as is. So, this workflow isn’t meant to be copied 1:1. It’s about demonstrating what the future of SOC automation could look like.
AI & Automation in the SOC: Logic App meets Copilot for Security
Automated workflows and AI-powered analysis offer major benefits because they take over repetitive tasks, standardize routine procedures, and save valuable time. For example, a Logic App can be triggered automatically whenever a new incident is created. As soon as Sentinel detects an issue, the Logic App retrieves all related entities: IP addresses, user accounts, endpoints, processes, file hashes, URLs, and domains – essentially the key data points for every incident.
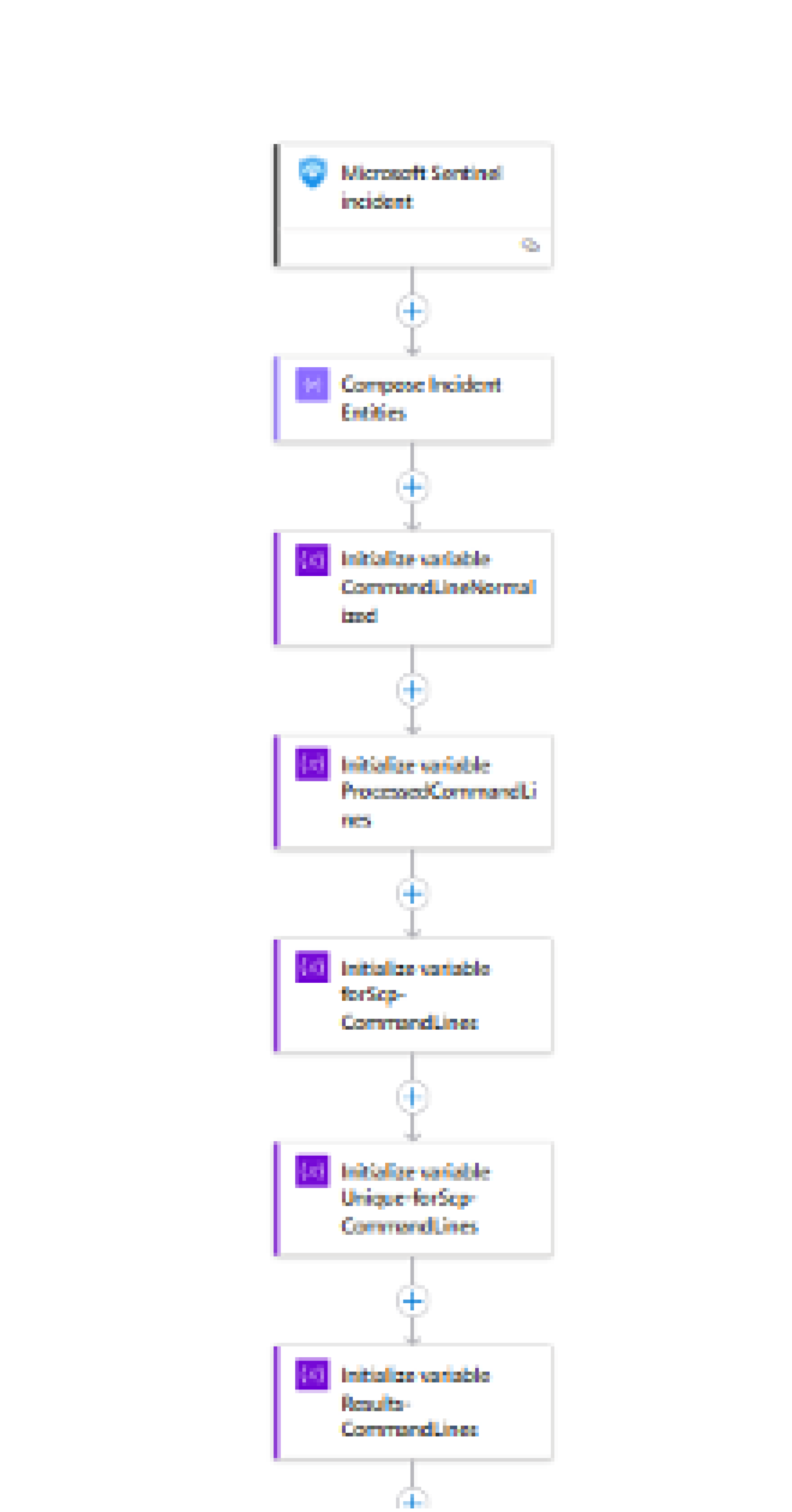
After categorizing the entities, the app initiates AI-based queries via Security Copilot – depending on the configured settings:
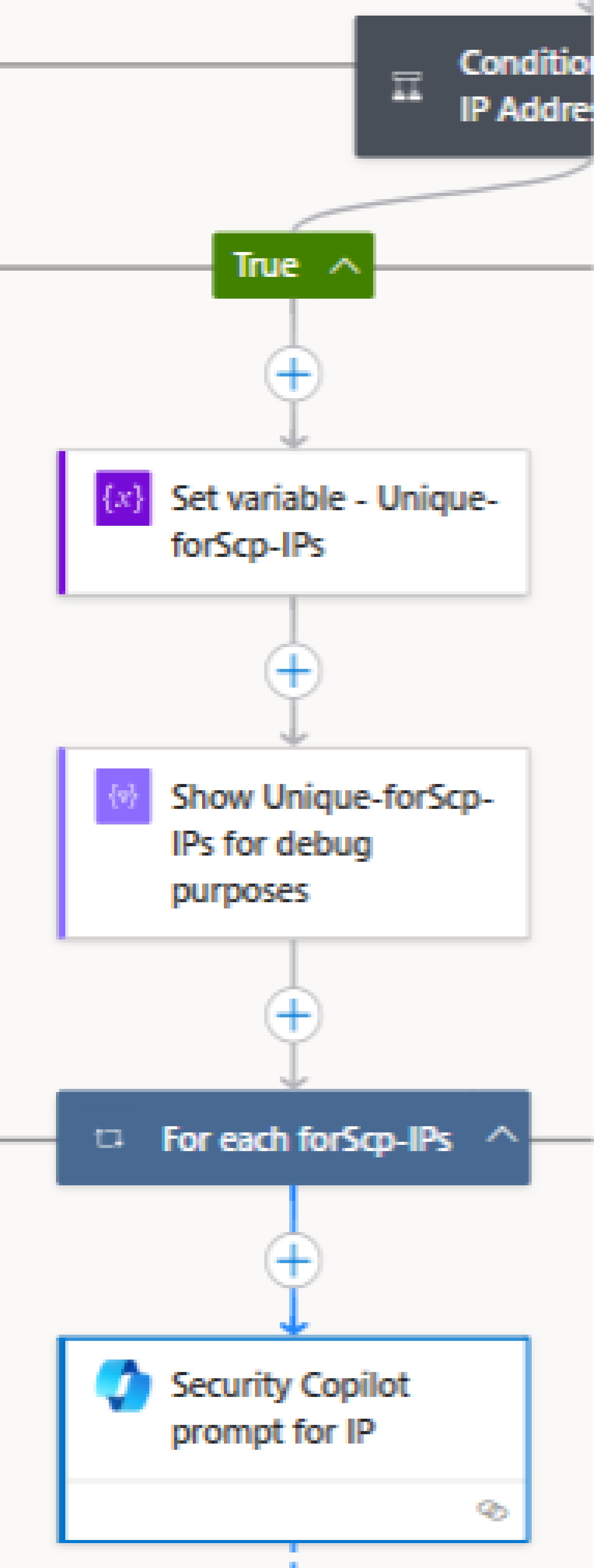
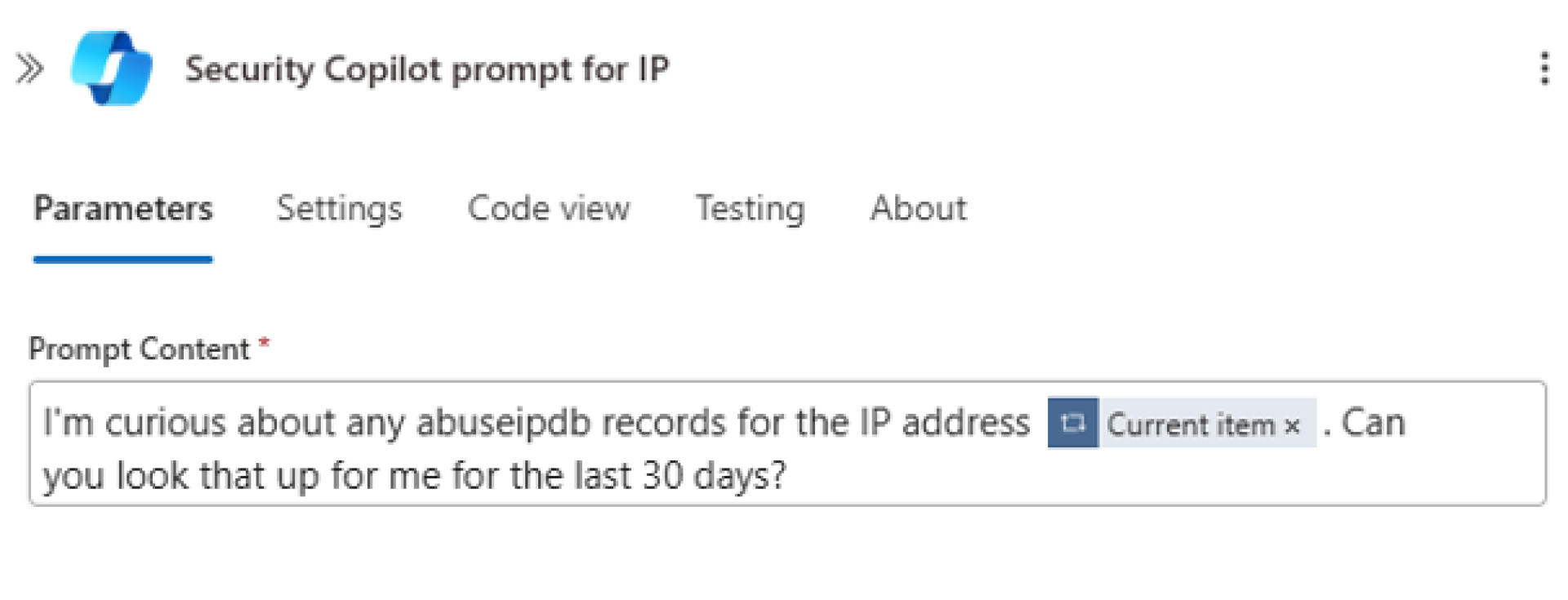
- AbuseIPDB (Threat Intelligence)
Security Copilot is asked to check the AbuseIPDB database for any reported abuse of each IP over the last 30 days (e.g., spam, DDoS, malware distribution).
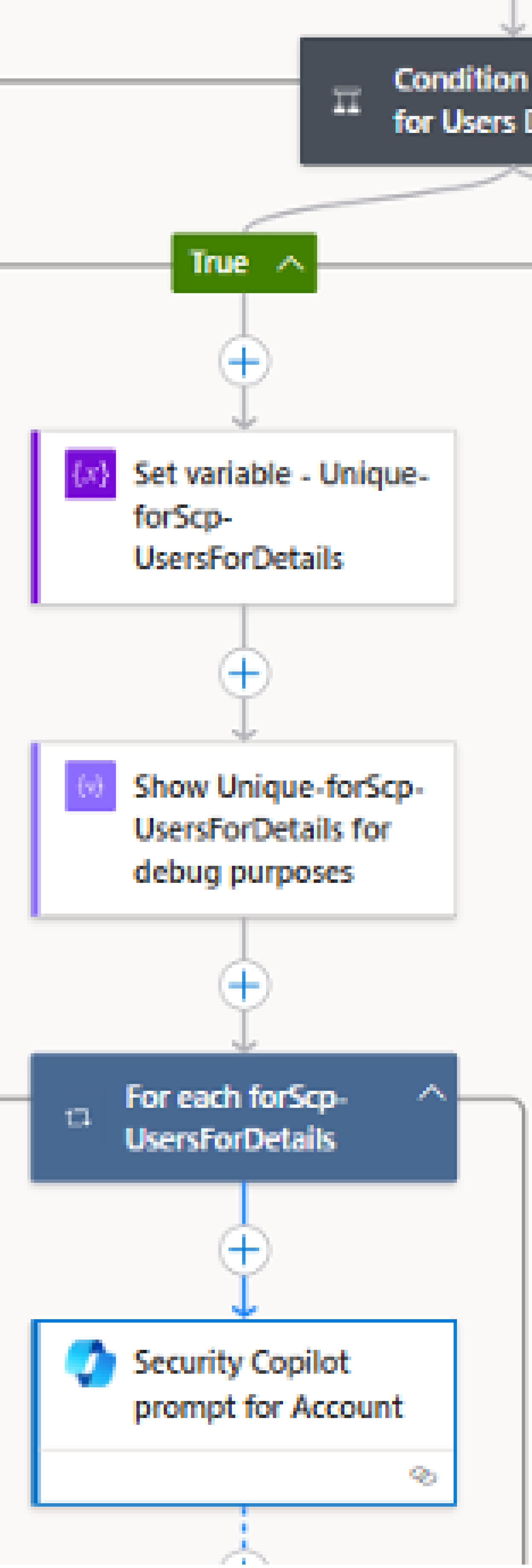
User Account Analysis (Microsoft Entra)
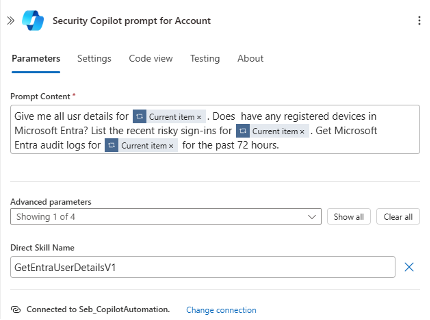
- User Details
The AI skill “GetEntraUserDetailsV1” checks whether the specified account has any registered devices, group memberships, or recent sign-ins.
- User Risk
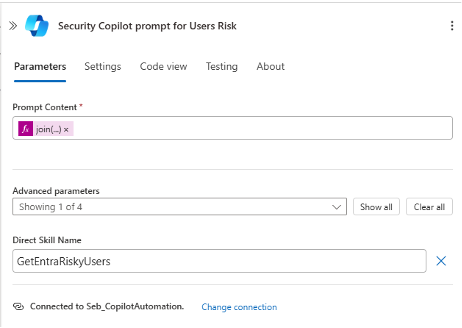
The “GetEntraRiskyUsers” skill evaluates whether the account is classified as high risk (e.g., unusual sign-in locations or multiple failed login attempts).
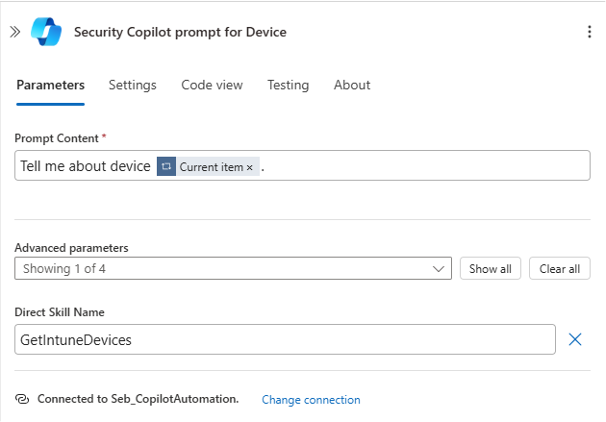
Endpoint (Intune) Analysis
The Logic App calls the Intune skill “GetIntuneDevices” to check compliance status, last check-in time, and any known vulnerabilities of each device.
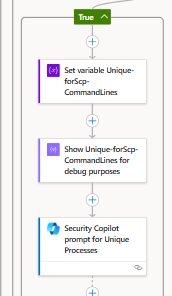
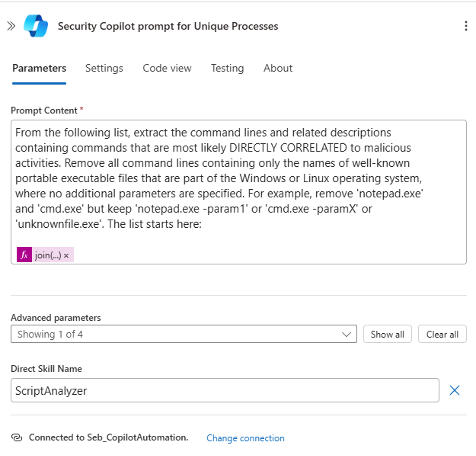
Process/Command Line Analysis
All command line fragments collected by Sentinel are sent to the “ScriptAnalyzer” AI skill, but only commands that go beyond standard Windows or Linux executions are analyzed (e.g., “cmd.exe /C …” or nonstandard binaries). Security Copilot then identifies which processes are likely part of malicious activity.
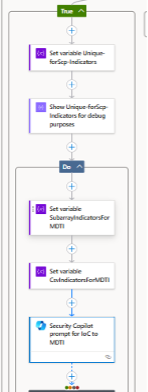
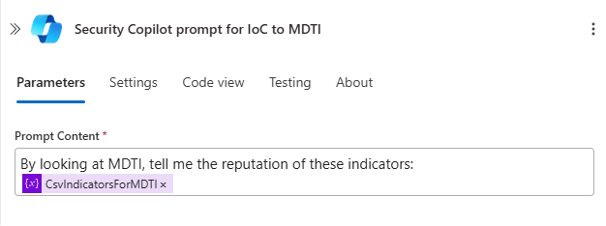
File Hash, URL & Domain Reputation (MDTI)
Indicators of Compromise (IoCs) such as file hashes, URLs, or domains are sent in batches of ten to MDTI’s “GetReputationsForIndicators” skill to retrieve reputation data and threat context (e.g., C2 servers, malware distribution). For very large indicator lists, the Logic App can automatically aggregate interim results so that the final summary is not cut off prematurely due to input length limits.
Final Results
All responses from the AI queries are collected into structured result arrays and checked for relevant findings. The Logic App then creates a comprehensive incident report that includes the title, description, severity, tactics, IP analyses, account details, risk assessments, device information, process analysis results, and IoC summaries.
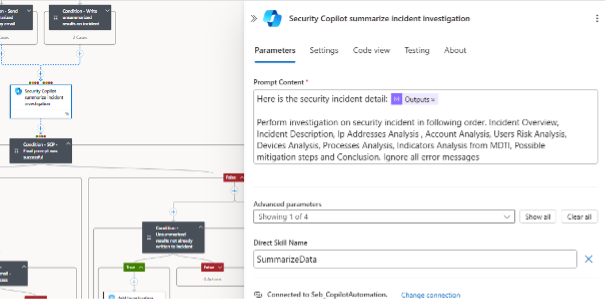
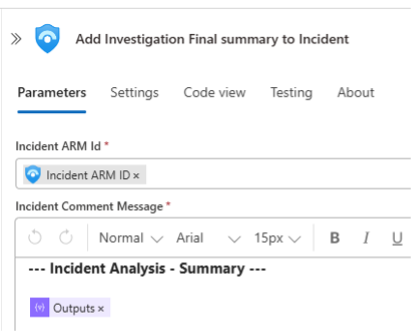
This summary is added as a final comment to the Sentinel incident, giving analysts a clearly structured overview within minutes.
Conclusion
With automation and AI in place, SOC teams can speed up their routine tasks like IP reputation checks, device status queries, or command-line analyses and get to the core of an incident faster – instead of wasting time on manual data collection. The Logic App is an example of how an automated playbook in Microsoft Sentinel can be built: it gathers and filters entities, retrieves context-rich intelligence from threat-intelligence services, performs AI-driven risk analyses, and presents all findings in a clearly structured report. With this approach, threat response becomes faster, and analysts can spend their time on deeper investigation and complex incidents.
If you’re curious what this could look like in your environment: I’m happy to help design a practical, tailored workflow based on your needs and use cases.
Feel free to reach out – I’d love to hear from you!



