What is Microsoft Entra Suite?
What is Microsoft Entra Suite?
The Microsoft Entra Suite is a comprehensive identity and access management solution designed to help organizations secure access to their digital resources, manage identities, and enforce Zero Trust principles. It includes a range of features and products tailored to meet various security and compliance needs. Here’s a breakdown of the main components:
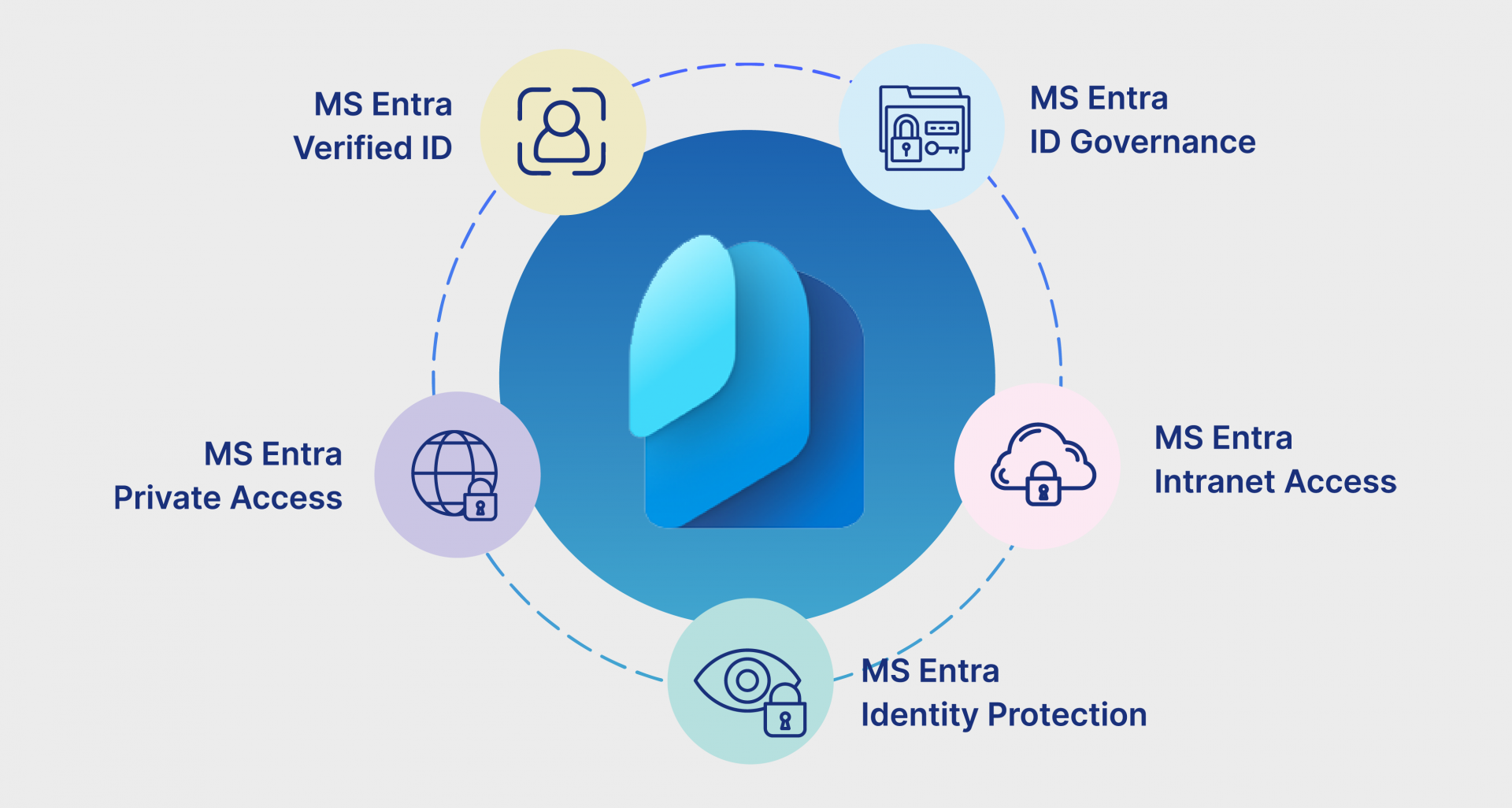
- Microsoft Entra ID P1 and P2: These licenses are available as standalone products or as part of Microsoft 365 E3 and E5.
· P1: Provides essential identity and access management features, including conditional access and basic security reports.
· P2: Includes advanced capabilities such as Identity Protection, Privileged Identity Management (PIM), and access reviews, offering a higher level of security and compliance - Microsoft Entra ID Governance: This license is necessary for advanced identity governance features such as entitlement management, lifecycle workflows, and advanced access reviews. It is designed to automate and manage identity-related processes and ensure compliance.
- Microsoft Entra Internet Access: This license secures access to all internet and SaaS applications, offering adaptive access controls, threat protection, and compliance monitoring. It can be purchased independently or as part of the Entra Suite.
- Microsoft Entra Private Access: Provides Zero Trust Network Access (ZTNA) for private applications and resources. Available as a standalone product or within the Entra Suite.
- Microsoft Entra Verified ID: Enables verification and issuance of digital identities, included with any Microsoft Entra ID subscription. Advanced features like Face Check are included in the Entra Suite or can be purchased separately.
- Microsoft Entra Identity Protection: Available with the Microsoft Entra ID P2 license, this provides risk-based policies, detailed security reports, and automated responses to detected risks. The Entra Suite includes all Identity Protection features, offering a comprehensive security solution for identity management.
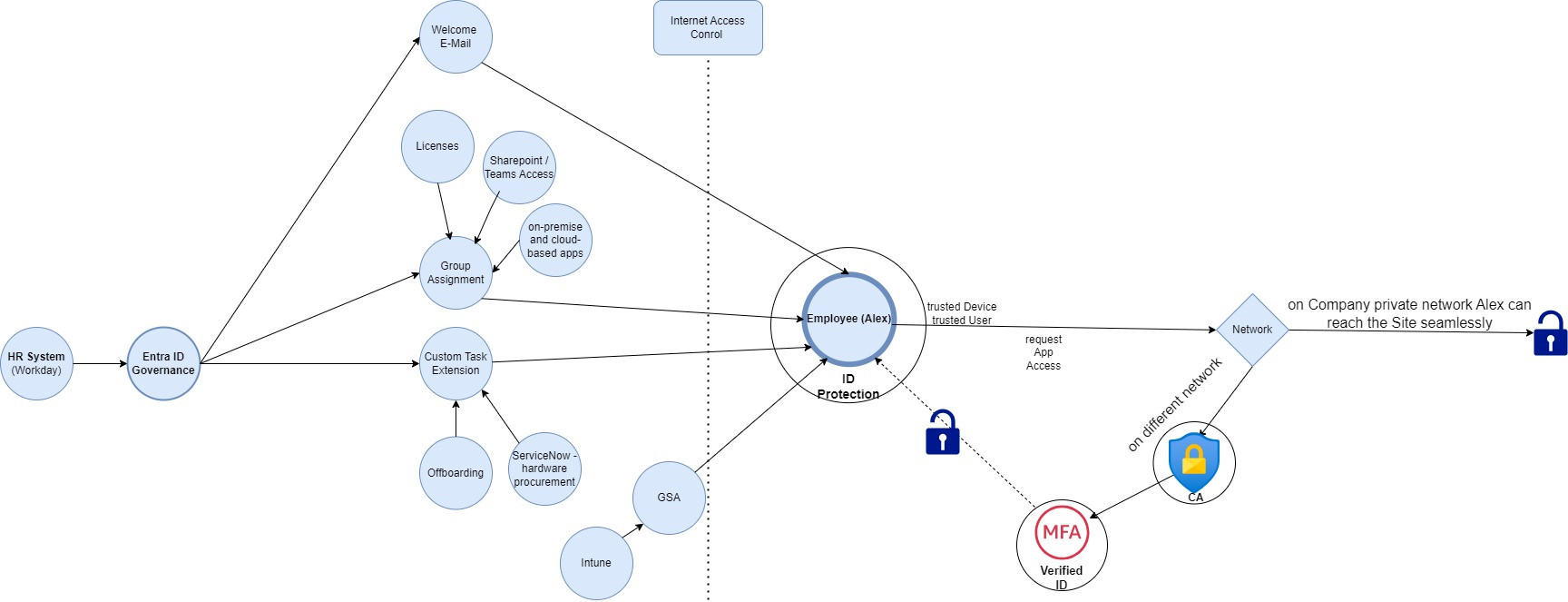
Let's illustrate how Microsoft Entra ID Governance and other tools work together in everyday connected scenarios.
User Onboarding Process
Initial Setup
When a new employee, Alex, is hired, their information is entered into the HR system, Workday. This triggers an automated process within the Microsoft Entra Governance:
- Attribute Mapping and Provisioning:
Alex's user profile in Microsoft Entra automatically receives attributes from Workday, including the hire date and department information. However, simply having an account in the directory service is not enough; Alex needs access to specific resources to perform his job. Automated Lifecycle Workflow:
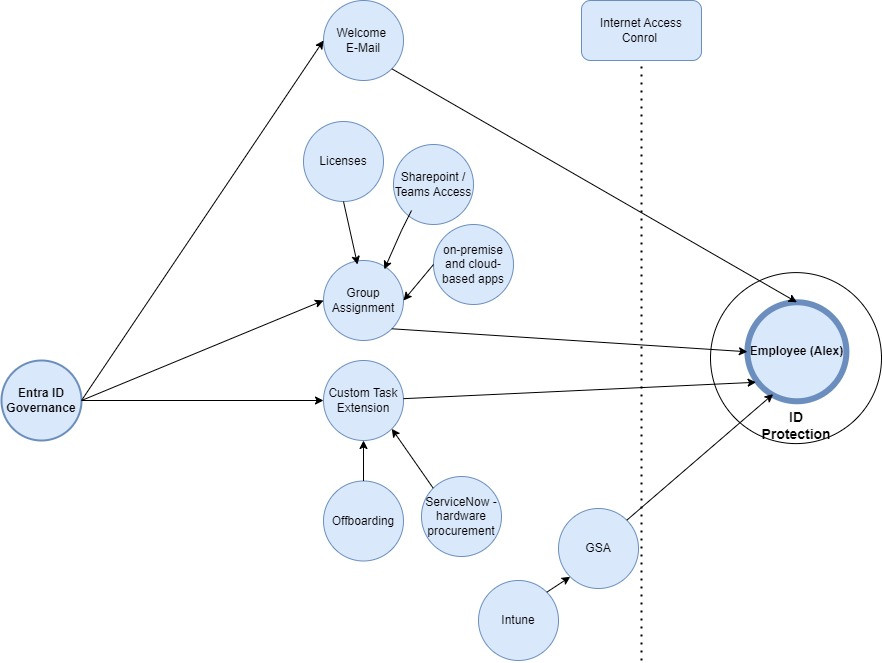
A custom workflow is triggered based on Alex's attributes, such as department and location. The workflow includes the following steps:
- Welcome Email: Alex receives a welcome email with instructions and resources.
- Group Assignment and Software Licenses: Alex is automatically added to relevant groups, granting access to necessary software licenses and applications, both on-premises and cloud-based.
- SharePoint and Internet Access: Permissions are granted to specific SharePoint sites, and controls are set for internet endpoint access.
- Hardware Procurement: An integration with the ticketing system initiates a request for the necessary computer hardware for Alex's role.
This automated workflow ensures that Alex has all the resources needed from day one, saving time and reducing administrative overhead.
Access Control and Security
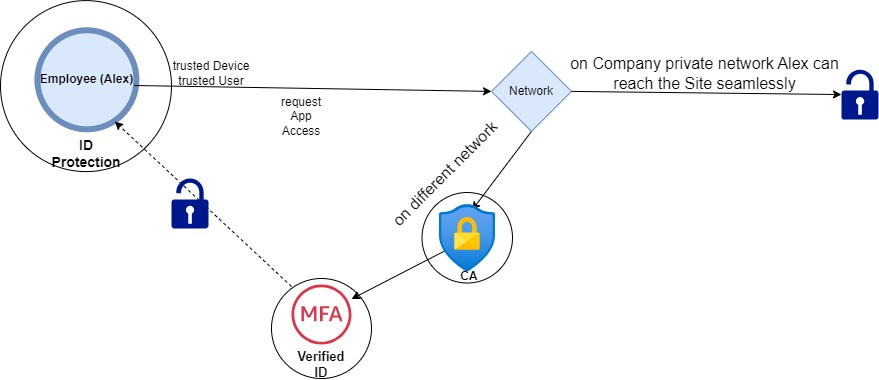
Access to On-Premises Resources
- Trusted Network Access:
When Alex tries to access an on-premises application from the office network, the Global Secure Access client on his device recognizes it as a trusted environment. Alex seamlessly reaches the application because his device, identity, and network location are all trusted. - Untrusted Network Access:
If Alex switches to an untrusted network, like a public Wi-Fi, and tries to access the same application, Conditional Access policies detect the change. The increased risk triggers a requirement for Alex to re-authenticate, using passwordless authentication, to confirm his identity before granting access.
Access to Additional Resources
Domain-Joined Virtual Machines and File Shares:
Alex can also access other on-premises resources, such as domain-joined virtual machines and file shares. Even if he uses a non-domain-joined device, these resources remain accessible without needing a VPN, thanks to Entra's secure access management.
Internet Access Control
1. Web Content Filtering:
- Tech Innovators' admin sets up web content filtering policies to control internet access. For example, social networking sites like X are blocked, while professional networking sites like LinkedIn are allowed.
- These policies are tied to Conditional Access controls and ID Governance, ensuring that access rights dynamically adjust based on Alex’s role and risk level.
2. Dynamic Risk-Based Policies:
- If Alex's account shows signs of being compromised, such as suspicious API calls or unusual activity patterns, it gets flagged with a high user risk. Conditional Access and web filtering policies then restrict Alex’s access to sensitive sites until his account is deemed secure again.
Integration with ID Protection
- User and Sign-In Risk Detection:
Machine learning algorithms within Microsoft Entra ID Protection continuously monitor Alex’s account for unusual sign-in patterns and potential compromise. If any anomalies are detected, automated actions are taken to mitigate the risk, such as requiring additional authentication steps. - Token Protection:
Tokens issued to Alex are bound to his specific device, ensuring that if they are stolen, they cannot be used on another device. This adds an extra layer of security, protecting sensitive resources from unauthorized access.
Compliance and Audit
- Detailed Logging and Reporting:
All actions, including access requests, approvals, and usage patterns, are logged. This comprehensive logging supports compliance with regulatory requirements and facilitates internal audits. - Automated Compliance Checks:
Regular checks are conducted to ensure that all access rights and activities comply with industry regulations and company policies. Any discrepancies are flagged and addressed promptly.
While Microsoft Entra Suite is an investment, it offers substantial benefits that make it a worthwhile consideration for large enterprises, financial services, healthcare providers, government agencies, educational institutions, and technology companies. Its advanced security features, compliance capabilities, and integration with existing systems provide a robust solution for organizations with high security and regulatory needs. For these entities, the cost is justified by the significant enhancements in security, efficiency, and compliance.
I don't want to bore you with long texts, so I'll be writing separate blog articles about each product in the Entra Suite. Stay tuned for some insightful and fun reads!


