Unlocking Secure Access: Exploring Entra Global Secure Access
Goodbye VPN, hello Microsoft SSE
In an era where remote work is increasingly common, ensuring secure and seamless access to corporate resources has become more important than ever. As organizations adjust to the realities of hybrid workplaces and spread-out teams, the priority is to maintain tight security alongside high productivity levels.
Enter Entra Global Secure Access, a comprehensive solution designed to address these challenges and empower organizations with secure, flexible, and user-centric access to critical resources.
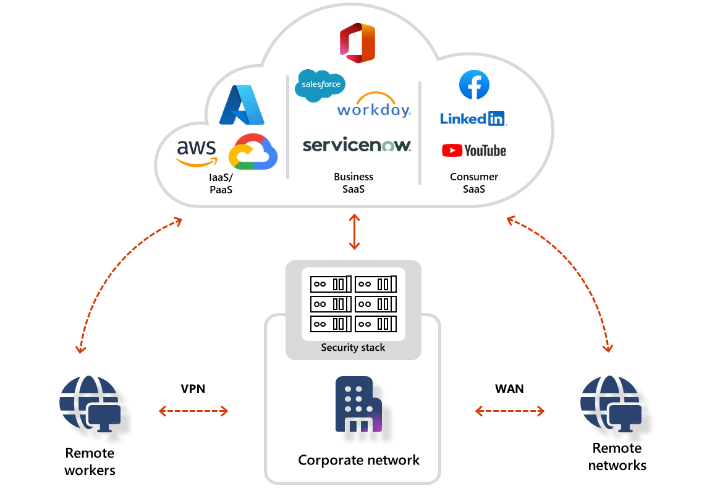
What is Entra Global Secure Access?
Entra Global Secure Access is a cloud-delivered secure access service edge (SASE) solution that combines network security, zero trust access, and secure web gateway capabilities into a unified platform.
By converging these essential security functions, Entra Global Secure Access provides organizations with a holistic approach to secure access management, offering comprehensive protection against a wide range of cyber threats while ensuring optimal user experience and productivity.
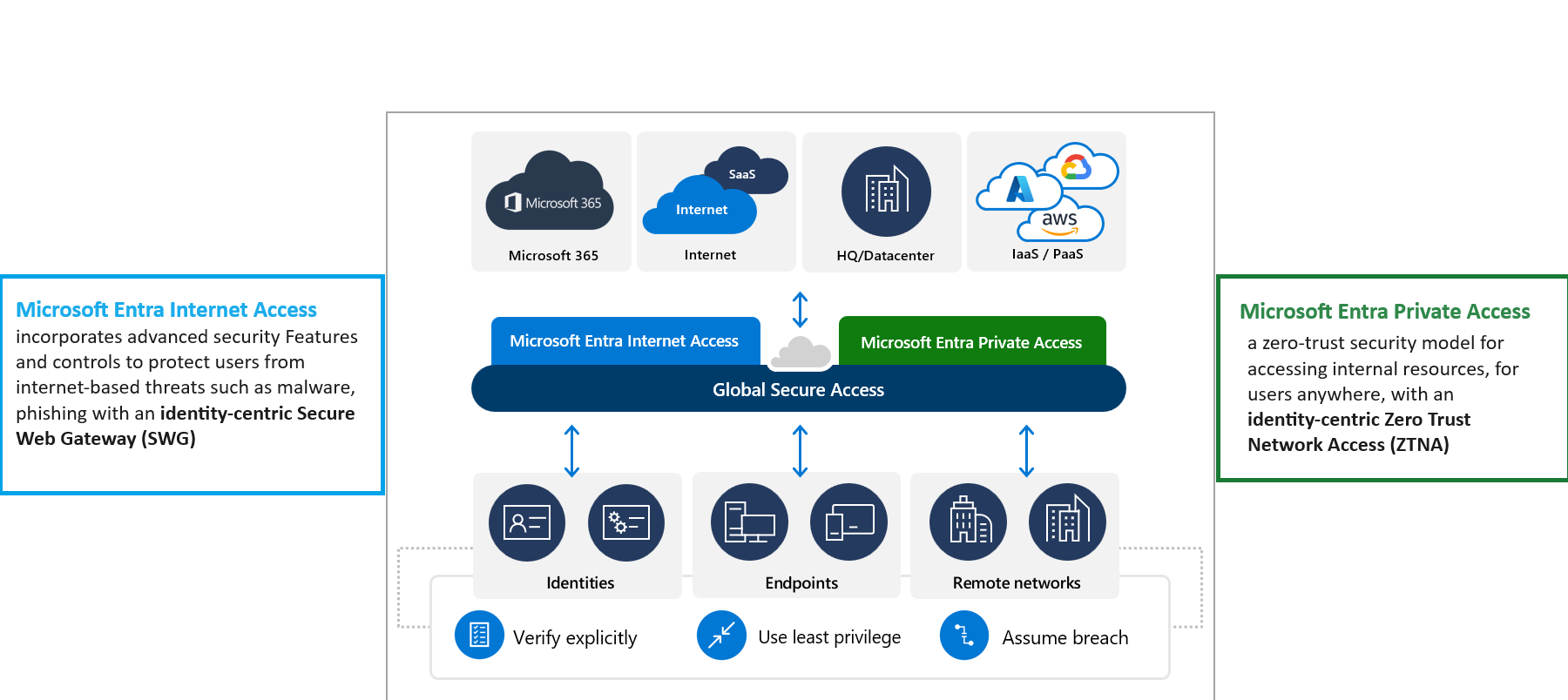
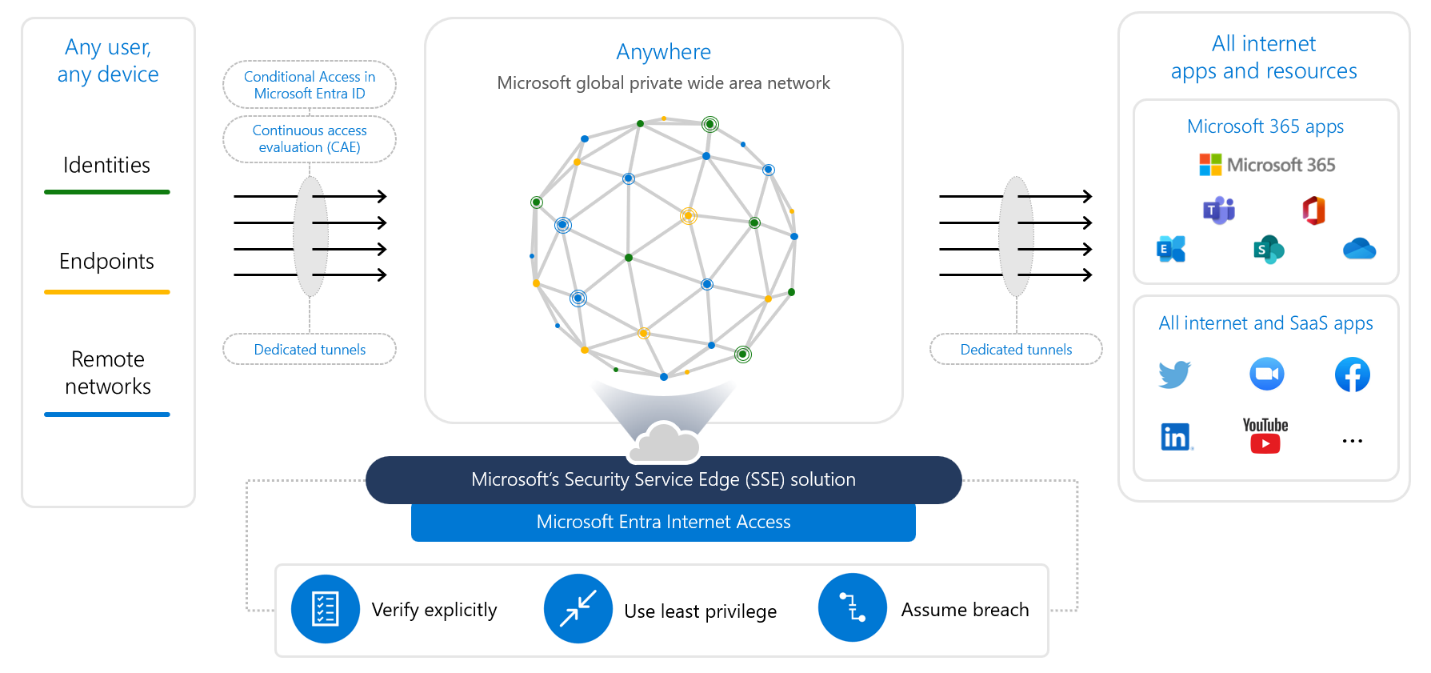
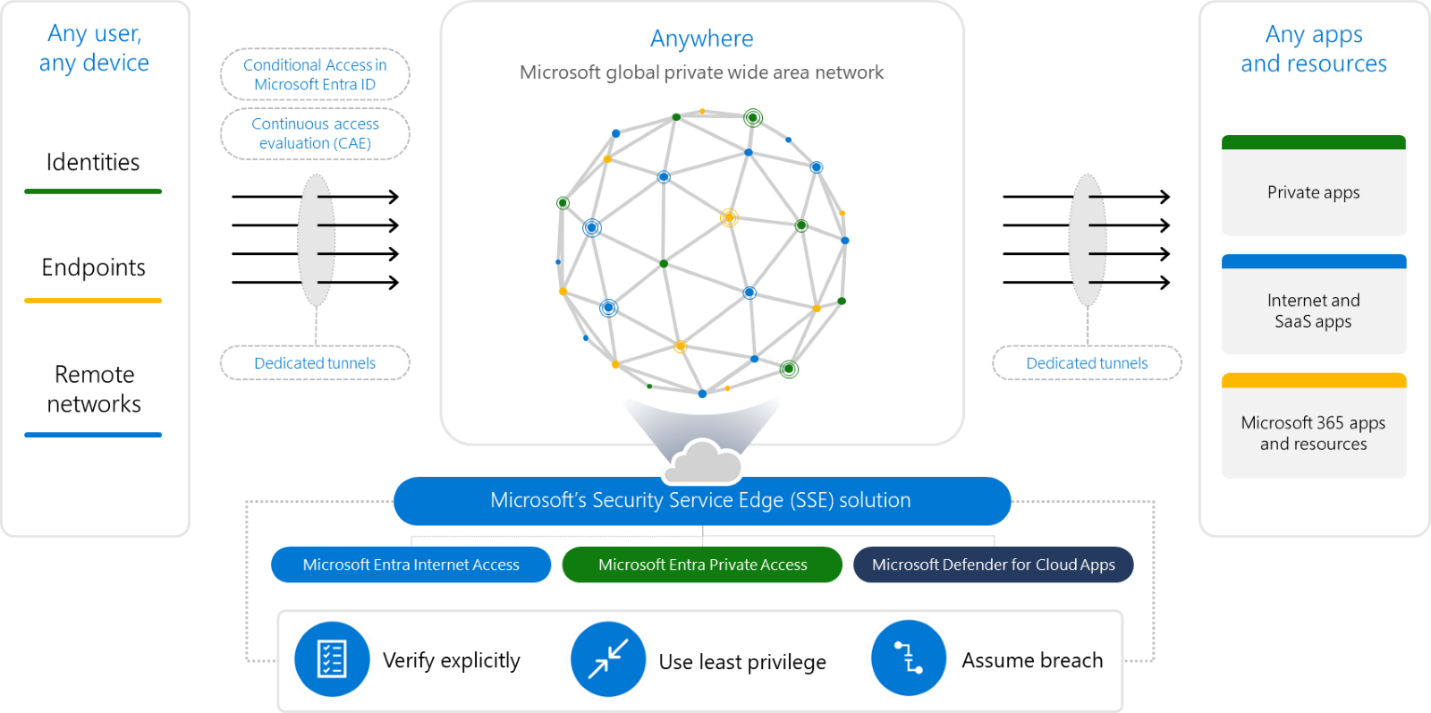
Microsoft Entra Internet Access
Microsoft Entra Internet Access serves as a Secure Web Gateway (SWG) focused on identity for SaaS applications and web traffic, offering protection from harmful online traffic, content that's either dangerous or doesn't meet compliance standards, and various internet-based threats. For instance, it enables the restriction of access to external sites for users or devices considered high-risk or non-compliant, with the exception of pages for self-service password resetting.
Additionally, it enhances Conditional Access policies by incorporating network-related conditions. This means, for example, that to access certain resources, a user must be connected to a network that meets specific compliance criteria, thereby preventing the misuse of stolen session tokens by enforcing additional access controls.
Microsoft Entra Private Access
Microsoft Entra Private Access is a Zero Trust Network Access (ZTNA) solution that is identity-focused, utilizing the same connectors for applications but providing additional features to streamline and enhance the security of access to any private resource, including specific ports and protocols.
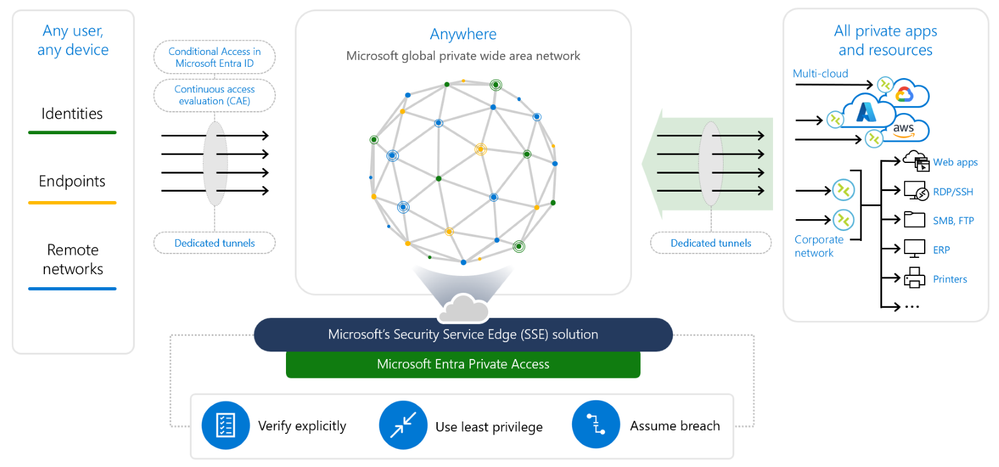
This solution allows users to effortlessly connect to private applications from anywhere—whether they're at the office or working remotely—and it's compatible with applications hosted in both local data centers and any public cloud environment. There's no need for modifications to these applications or resources to implement an extra layer of security. Features such as multi-factor authentication (MFA), checks for device compliance, identity protection, governance, and single sign-on for TCP/UDP-based applications like SSH, RDP, SAP, and SMB file shares, among others, are easily integrated.
Moreover, with attribute-based Conditional Access policies, creating straightforward policies becomes possible, allowing for more precise targeting of application groups based on their sensitivity levels within the organization.
Through comprehensive integration with Conditional Access and Continuous Access Evaluation, it's possible to facilitate secure and uninterrupted access using modern authentication methods ahead of traditional authentication protocols like Kerberos or NTLM, without the need to modify existing legacy applications.
Gain secure access to any application or resource, from any location, through an identity-focused security service edge (SSE) solution.
Microsoft's SSE solution is formed by the combination of Internet Access and Private Access, alongside our SaaS-security-oriented CASB, Microsoft Defender for Cloud Apps. This integrated solution is part of Microsoft's extensive security portfolio, promoting an open ecosystem for partners and compatibility with your current network and security frameworks.
Both Internet Access and Private Access utilize a unified agent that supports various operating systems, ensuring consistent connectivity across different devices and networks. This setup allows for the implementation of unified Conditional Access policies that account for identity, device, application, and now network conditions for any application or website. This is achievable regardless of the Identity Provider (IdP) used by the application and without the necessity to modify these applications.
Prerequisites
Administrators who interact with Global Secure Access preview features must have the Global Secure Access Administrator role. Some features might also require other roles. To follow the Zero Trust princeple of least privelege, consider using Privileged Identity Management (PIM) to activate just-in-time privileged role assignments.
The preview requires a Microsoft Entra ID P1 license. To use the Microsoft 365 traffic forwarding profile, a Microsoft 365 E3 license is recommended. After general availability, Microsoft Entra Private Access and Microsoft Entra Internet Access might require different licenses.
Configuration Schema
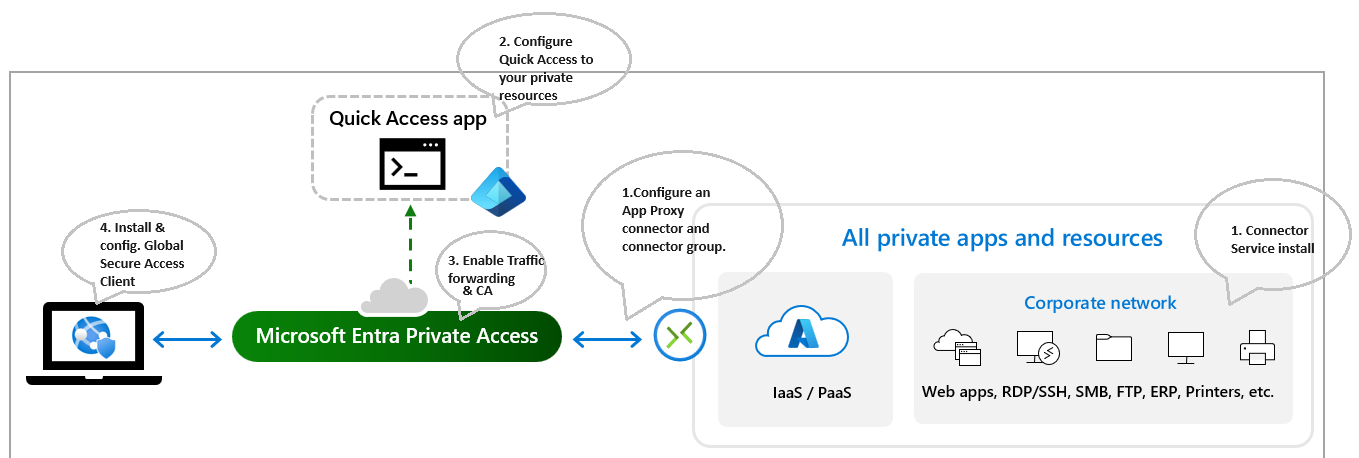
- To enhance security and streamline access, begin by setting up an App Proxy connector and organizing them into connector groups.
- Next, simplify entry to your private resources with Quick Access configuration.
- Proceed to activate the Private Access traffic forwarding profile, complemented by crafting a tailored Conditional Access Policy.
- Finally, ensure secure and seamless connectivity for your users by installing and configuring the Global Secure Access Client on their devices.
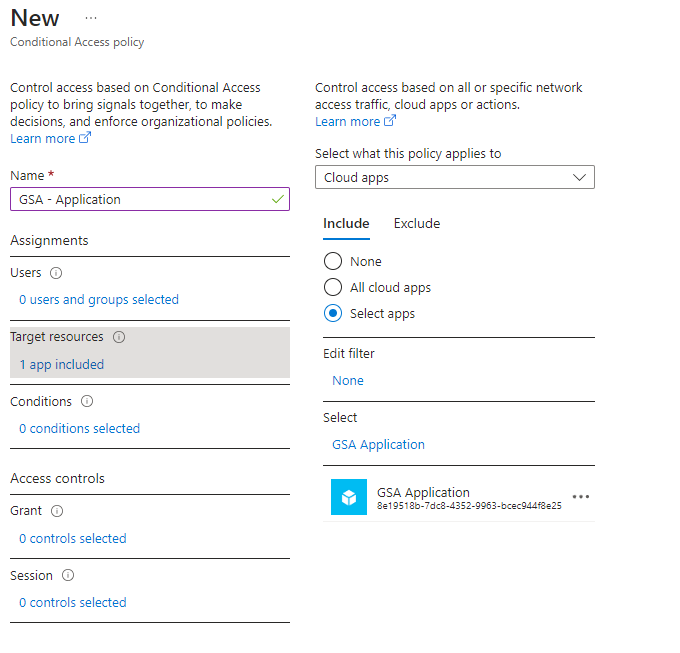
Some new Conditional Access Policies that you can create:
You can now require MFA for on-premise applications
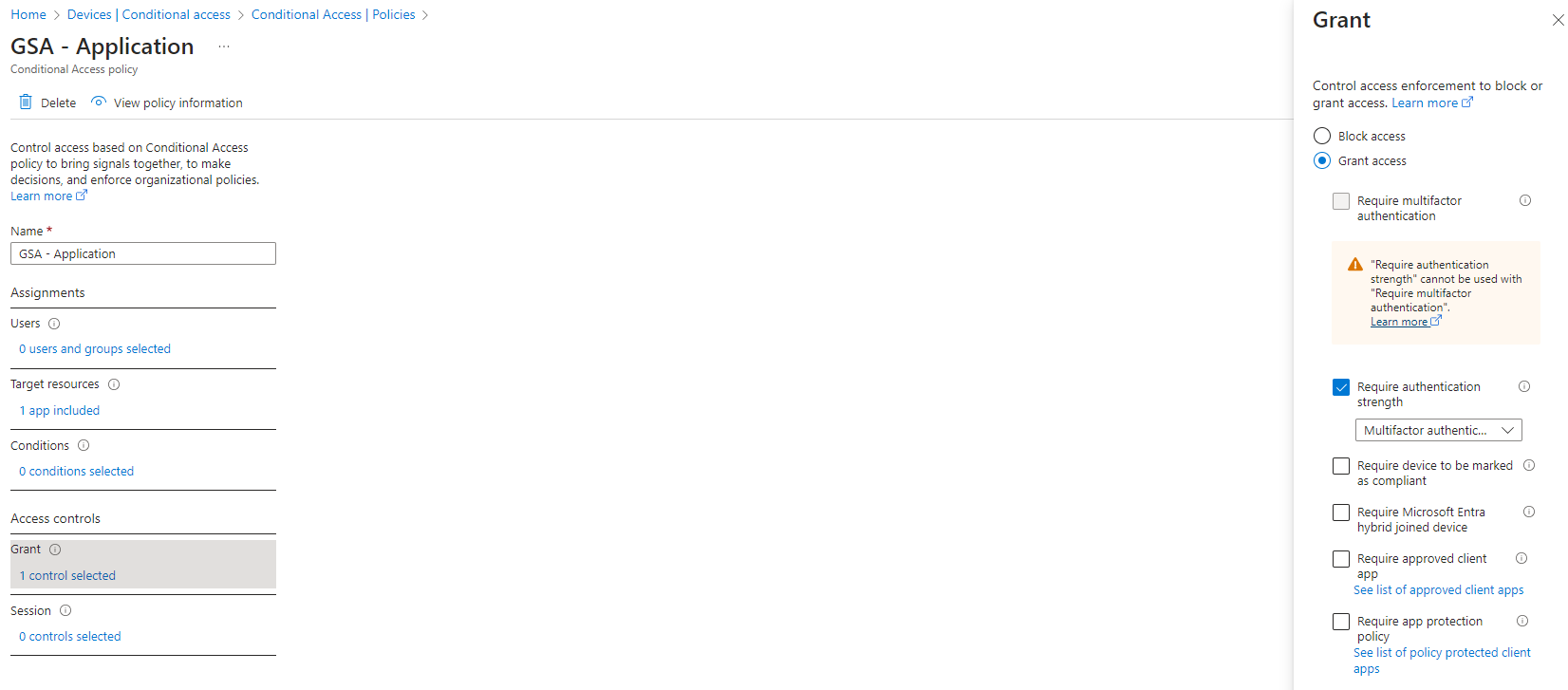
Additionally, you can implement explicit user and device trust validation
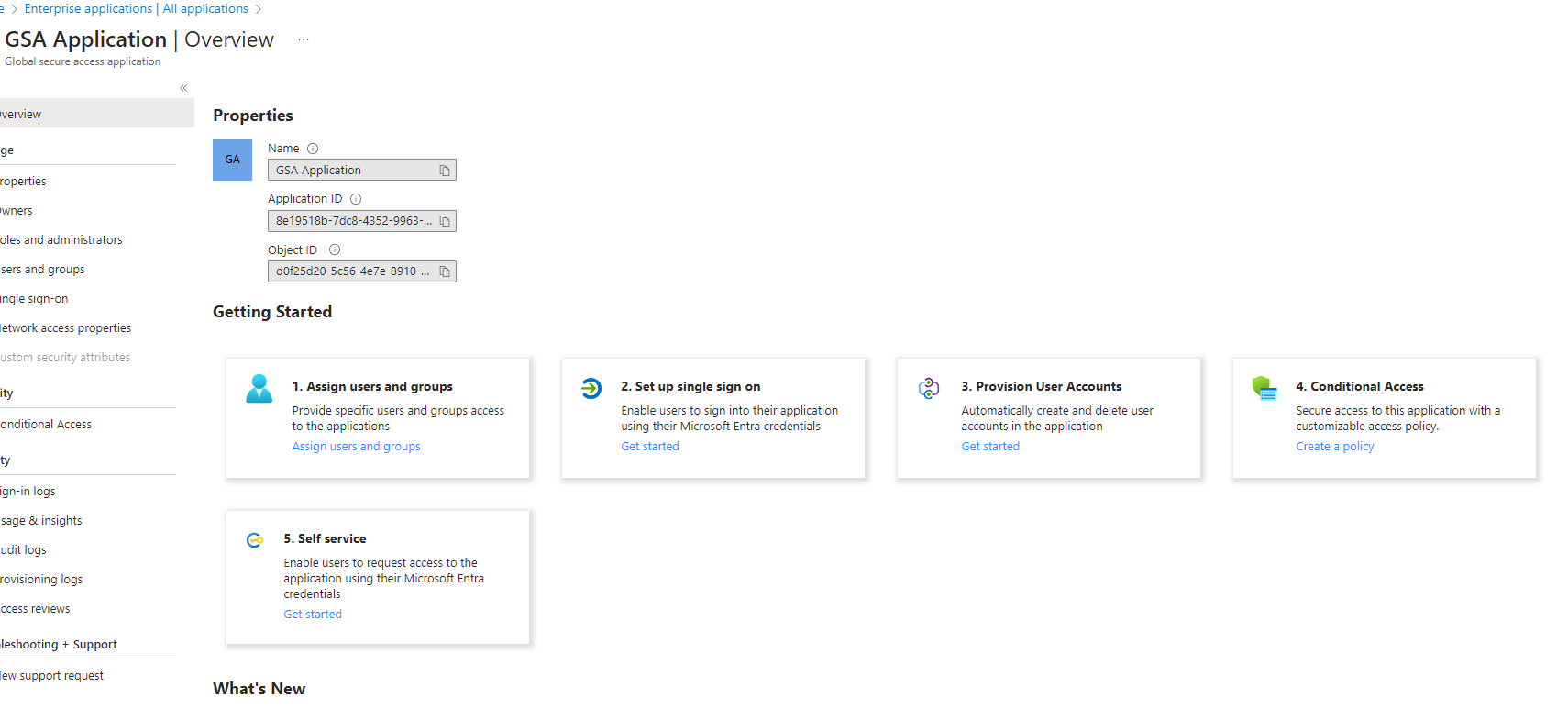
VPN typically allows access to all ports on the entire network and here you can specify an IP address, IP range or fully qualified domain name.
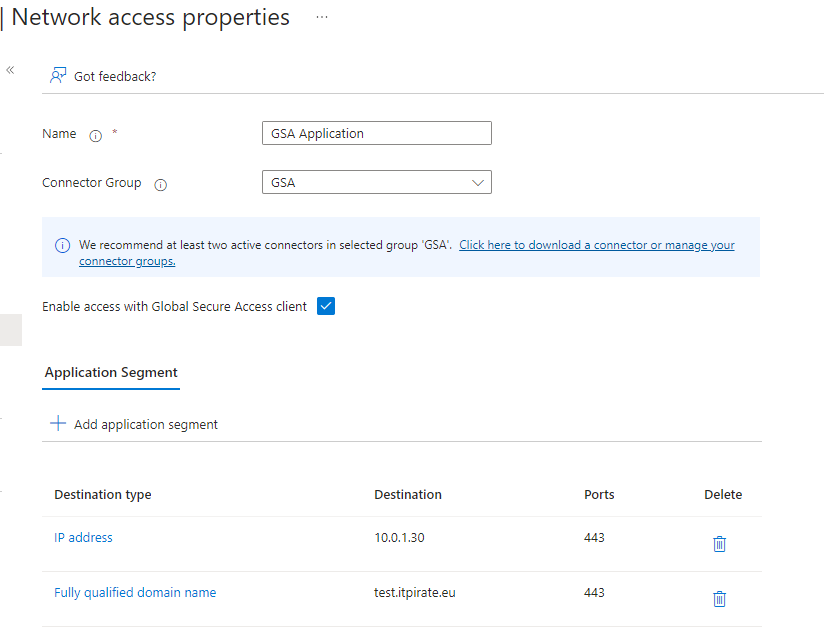
Control access based on all or specific network access traffic
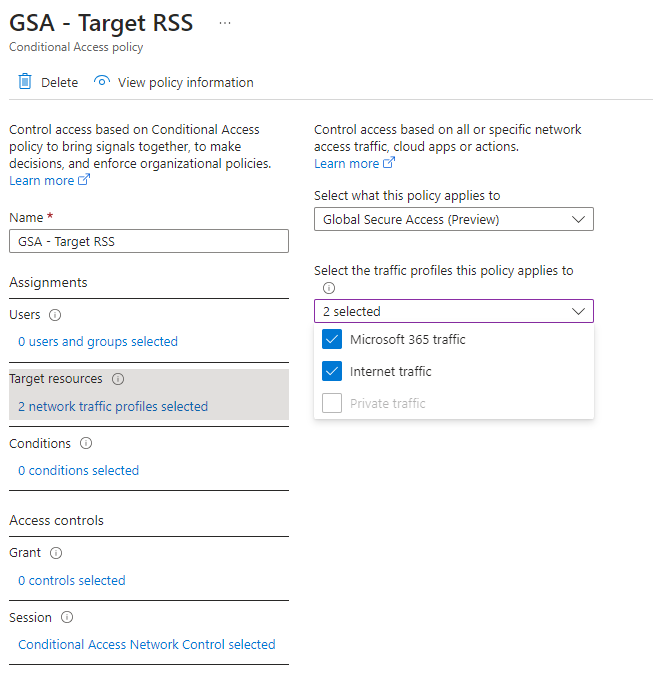
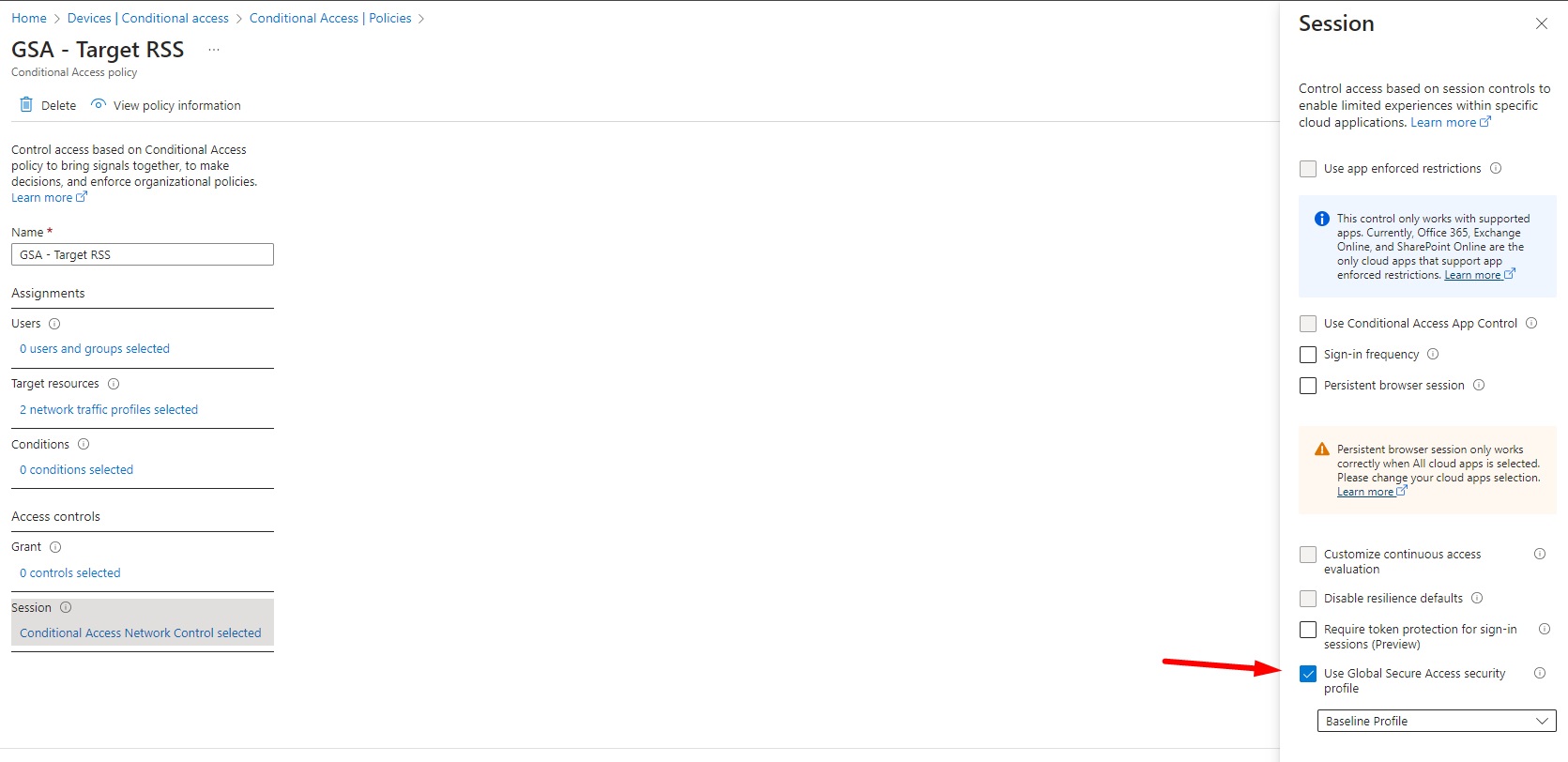
You have security profiles in Global Secure Access that you can attach to Conditional Access to make them user and context aware
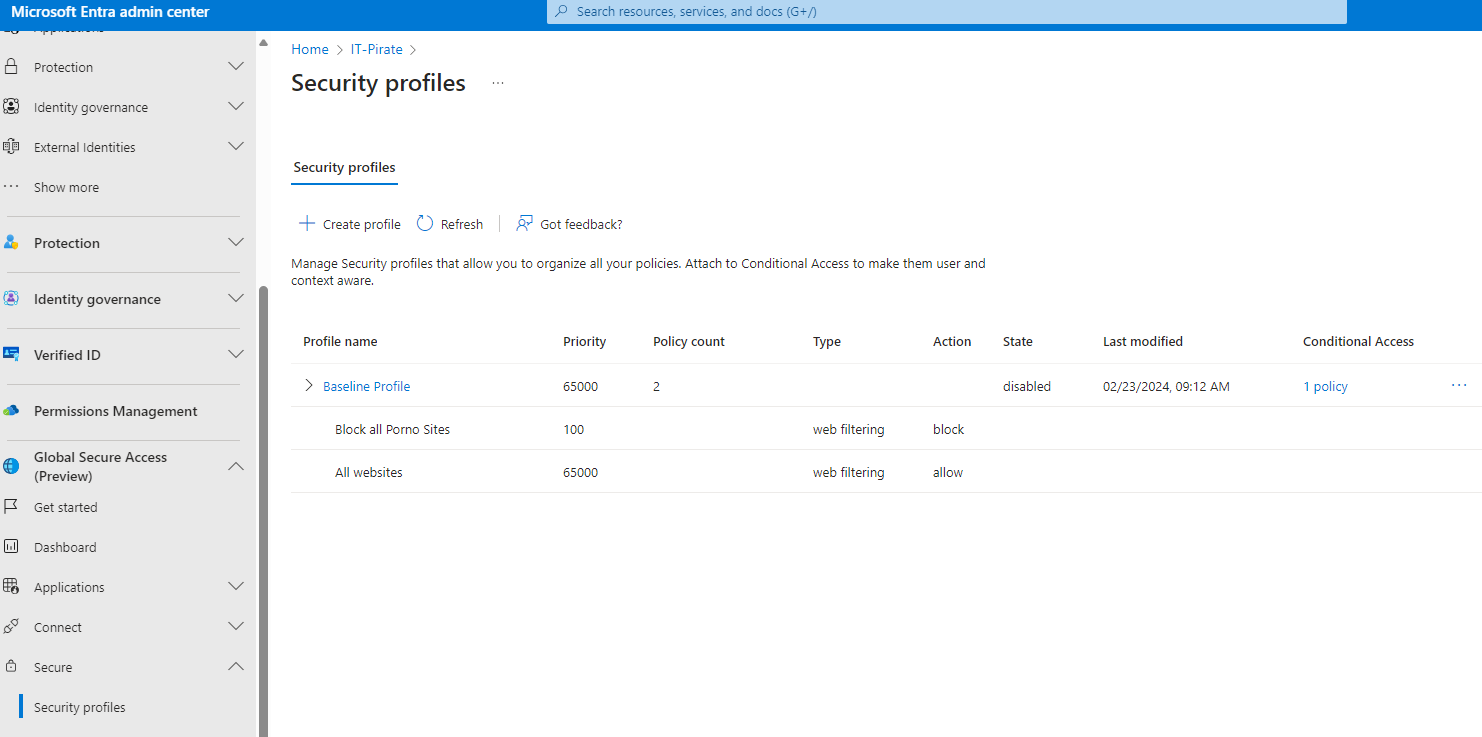
Moving from a third-party solutions to Global Secure Access (GSA), Microsoft's Security Service Edge (SSE) solution, may be beneficial for organizations for several reasons:
Integrated Ecosystem: Microsoft's SSE, including solutions like Microsoft Entra Private Access and Microsoft Defender for Cloud Apps, is part of a broader, integrated security ecosystem. This integration can provide seamless interoperability within the Microsoft environment, including Windows, Office 365, Azure, and more. For organizations heavily invested in Microsoft's ecosystem, this can mean better compatibility, simpler management, and enhanced security insights.
Unified Management: Microsoft's approach to security offers a unified management experience through platforms like Microsoft 365 Defender and Azure Security Center. This can simplify the administration of security policies, reporting, and threat intelligence across your digital estate, compared to managing multiple vendors' solutions.
Comprehensive Security: Beyond just access and networking, Microsoft's security solutions cover a wide range of needs, including identity and access management, threat protection, information protection, and security management. This comprehensive coverage can offer a more holistic security posture.
Conditional Access and Compliance: Microsoft's security solutions excel in providing detailed conditional access controls and compliance management capabilities, leveraging Azure Active Directory. These features allow organizations to fine-tune access policies based on user, device, application, and risk level, offering a more granular control over security than some competitors might.
Innovation and Investment: Microsoft continuously invests in and innovates its security offerings, integrating advanced technologies like artificial intelligence and machine learning for threat detection and response. This commitment to innovation can provide organizations with a cutting-edge security posture.
Cost and Licensing Advantages: For organizations already invested in Microsoft's ecosystem, consolidating security solutions with Microsoft could offer cost benefits through bundled licensing agreements like Microsoft 365 E5, which includes advanced security features.
Global Compliance and Data Sovereignty: Microsoft's global infrastructure and commitment to compliance with regional and industry-specific regulations can be crucial for organizations needing to meet strict data sovereignty and privacy requirements.
Scenario:
ABC Corp has an on-premise legacy application that stores critical customer information and financial data. John, a sales manager at ABC Corp, frequently needs to access this application to retrieve customer records and update sales data. However, due to security concerns and the need to enforce consistent access policies, ABC Corp decides to leverage Microsoft Security Service Edge (SSE) to secure access to the on-premise application.
Key Features Utilized:
Zero Trust Network Access (ZTNA): ABC Corp implements zero trust principles through ZTNA to ensure secure access to the on-premise application. John's access request is subject to identity verification, device health checks, and contextual analysis to determine the appropriate level of access based on his role, location, and other factors.
Secure Web Gateway (SWG): While accessing the on-premise application, John's web traffic is routed through the SWG component of Microsoft SSE. The SWG inspects inbound and outbound traffic, enforces content filtering policies, and detects any attempts to access malicious websites or download suspicious files.
Cloud Access Security Broker (CASB): To monitor and control data access within the on-premise application, ABC Corp utilizes the CASB capabilities of Microsoft SSE. The CASB analyzes user activity, detects data exfiltration attempts, and enforces policies to prevent unauthorized access or leakage of sensitive information.
Unified Policy Enforcement: ABC Corp centrally defines and enforces security policies through Microsoft SSE, ensuring consistent protection across all users, devices, and applications, including the on-premise application. Policies are tailored to the specific requirements of the application and are regularly updated to address emerging threats.
Threat Protection Integration: Microsoft SSE integrates with threat protection solutions to enhance ABC Corp's defenses against cyber threats targeting the on-premise application. Telemetry data from endpoints, networks, and cloud services is analyzed in real-time to detect and respond to security incidents promptly, minimizing the risk of data breaches or unauthorized access.
Example Use Case
John needs to access the on-premise application to retrieve customer records for a sales presentation while working remotely from a client site. Before granting access, John's identity is verified through multi-factor authentication (MFA), and his device undergoes a health check to ensure compliance with security policies.
Once authenticated, John's access request is routed through the ZTNA infrastructure, where it undergoes further scrutiny based on contextual factors such as his role, location, and the sensitivity of the data he's trying to access. The CASB monitors John's activity within the on-premise application, detecting any attempts to access restricted data or perform unauthorized actions.
Meanwhile, the SWG filters John's web traffic to prevent him from accessing malicious websites or downloading potentially harmful content while accessing the on-premise application.
Through the comprehensive security capabilities of Microsoft SSE, ABC Corp ensures that John can securely access the on-premise application from any location while maintaining the confidentiality, integrity, and availability of sensitive corporate data.
In summary, by leveraging key features of Microsoft Security Service Edge (SSE), ABC Corp strengthens its cybersecurity posture, enables secure access to on-premise applications, and mitigates the risks associated with modern workplace environments.
Conclusion
Microsoft Global Secure Access (GSA) represents a pivotal advancement in secure and seamless connectivity for organizations navigating the complexities of modern IT environments. By integrating essential components such as App Proxy connectors, Quick Access configurations, and the Global Secure Access Client, Microsoft GSA offers a comprehensive solution that not only simplifies access to private resources but also fortifies security across cloud and network traffic. The ability to customize Conditional Access policies further enhances this security, allowing organizations to tailor access controls to their unique requirements. With the implementation of GSA, businesses can achieve a balance between enabling flexible, remote work scenarios and maintaining stringent security standards, ensuring that their digital assets are protected in an ever-evolving threat landscape. This holistic approach to secure access underlines Microsoft's commitment to providing robust, user-friendly solutions that support the dynamic needs of modern enterprises.


