Effective vulnerability management - response flow training
Proactive vulnerability management is the key to a resilient organisation. With Microsoft Defender Vulnerability Management, Microsoft offers a powerful tool for identifying potential vulnerabilities at an early stage, prioritising them and remedying them in a targeted manner. The process used by Vulnerability Management can be broken down as follows:
Discovery
Microsoft Defender continuously detects devices and software in the environment:
• Automatic inventory of all devices and installed software.
• Integration with Microsoft Defender for Endpoint for endpoint telemetry.
• Identification of vulnerabilities in real time by analysing:
• Operating system versions
• Installed applications
• Configuration deviations
Assessment
As soon as devices and software are recorded, Microsoft Defender evaluates their security status:
• Comparison with threat databases (e.g. CVEs).
• Risk assessment based on:
• Severity of the vulnerability (CVSS score)
• Exploit availability (whether active attacks are already known)
• Device context (e.g. whether the device is particularly critical)
• Prioritisation of risks with the help of threat intelligence from Microsoft Security Graph.
Recommendations and prioritisation
The system provides specific recommendations for rectification:
• Patch suggestions or configuration changes.
• Prioritised list according to:
• Active utilisation
• Criticality of the assets
• Vulnerabilities with known malware campaigns
Remediation
Management and implementation of measures:
• Integration with Microsoft Intune, Endpoint Manager or Configuration Manager (SCCM/MECM) for automatic patch deployment.
• Ability to assign remediation tasks directly to IT administrators.
• Track remediation status in dashboards.
However, in order to react quickly and effectively in an emergency, you need more than just the tool - you need practice. This is exactly where our training comes in.
Goal: Identify weak points → prioritise → rectify
The aim of the training is to understand how and where information can be found by Microsoft Defender. Microsoft creates recommendations based on the current CVEs (Common Vulnerabilities and Exposures), which are automatically prioritised. The prioritisation can be adjusted as desired.
Exercise: CVE + asset + context
The focus is on a realistic exercise in which a critical CVE is identified. The focus is not only on the vulnerability itself, but also on the context and how it is handled:
• Which asset is affected?
• How high is the risk if this vulnerability is exploited?
• What measures can be taken to deal with the vulnerability?
Step 1: Access to the Security Centre
Objective: Gain access to the Defender Portal and an overview of the environment
1. Log in at security.microsoft.com.
2. Navigate to Endpoints → Vulnerability management.
3. Take a look at the dashboard: device overview, software inventory and vulnerability status.
____________________________________________________________________________________________________________________
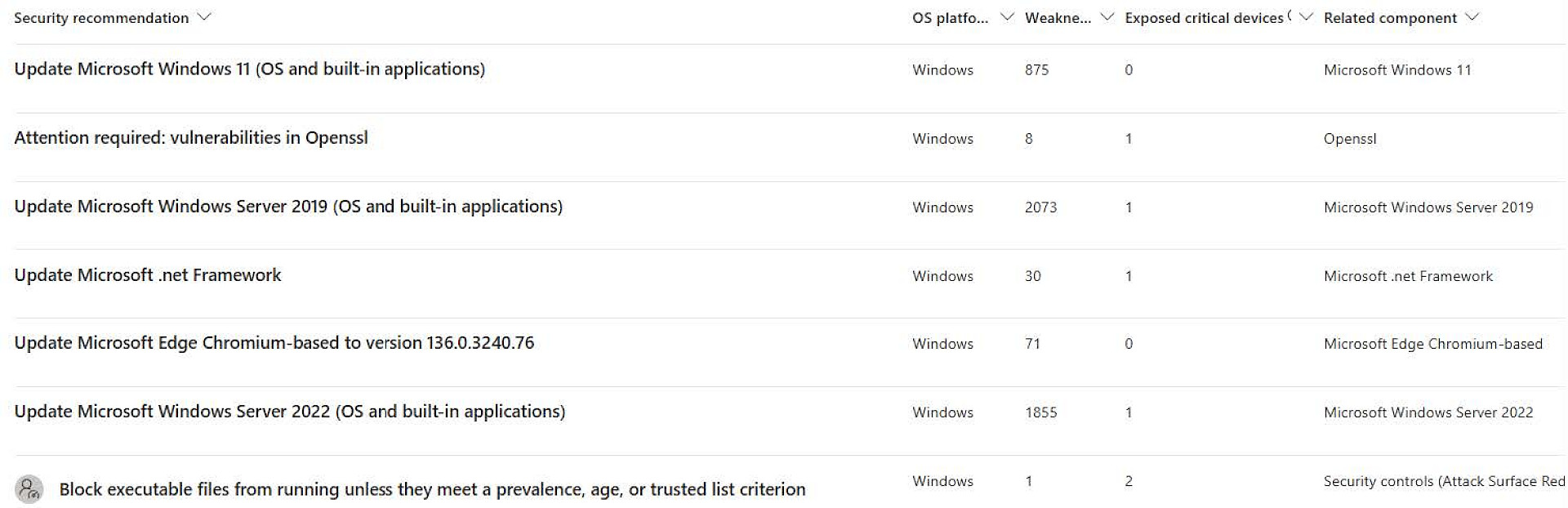
Step 2: Identify and evaluate weak points
Objective: To understand how Microsoft Defender detects and classifies vulnerabilities.
1. Click on the ‘Weaknesses’ tab.
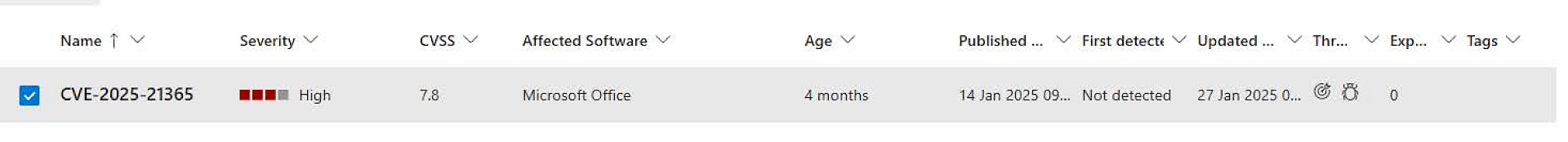
2. Search for CVEs with a high risk rating or a high CVSS (Common Vulnerability Scoring System) score.
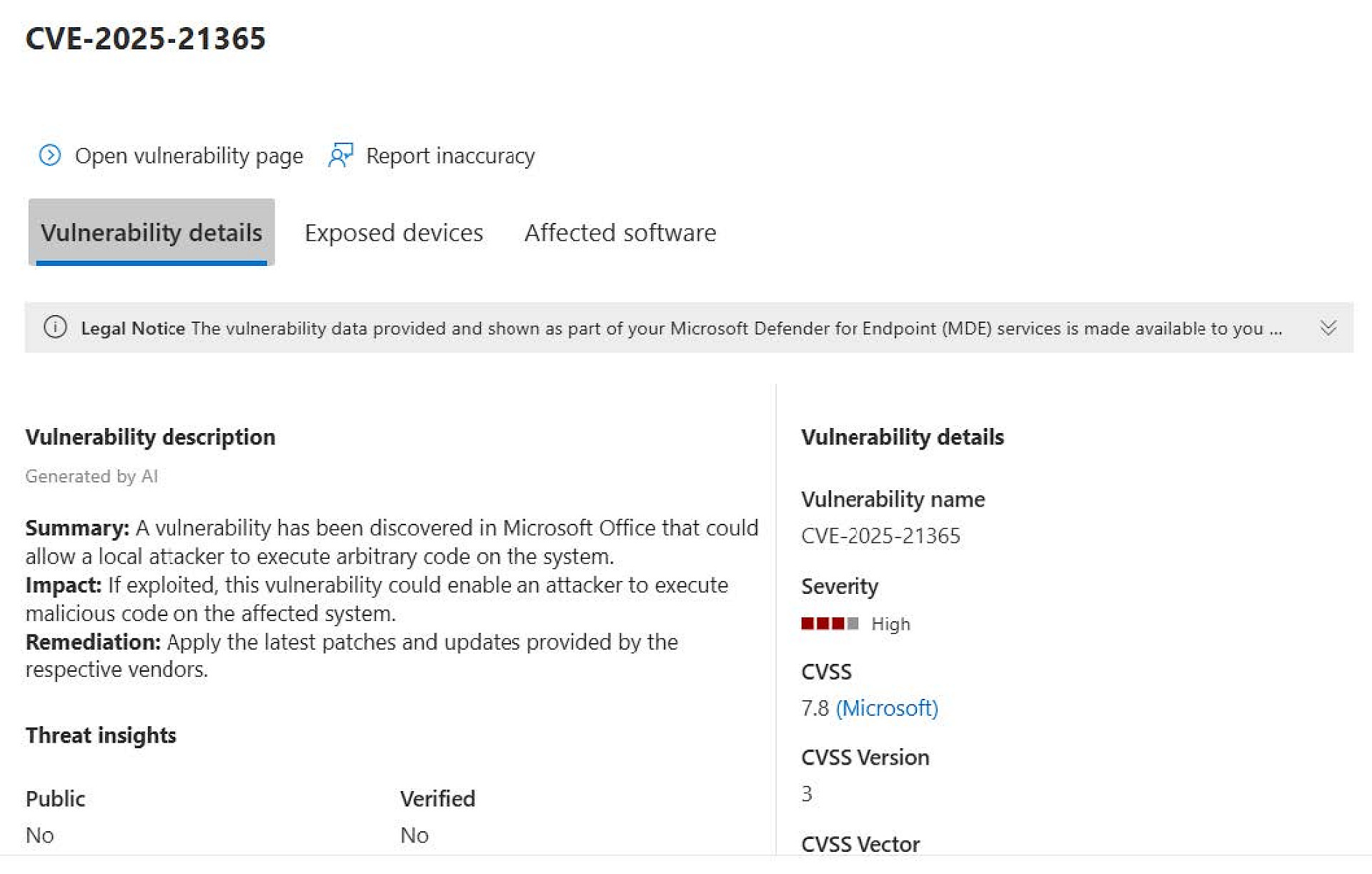
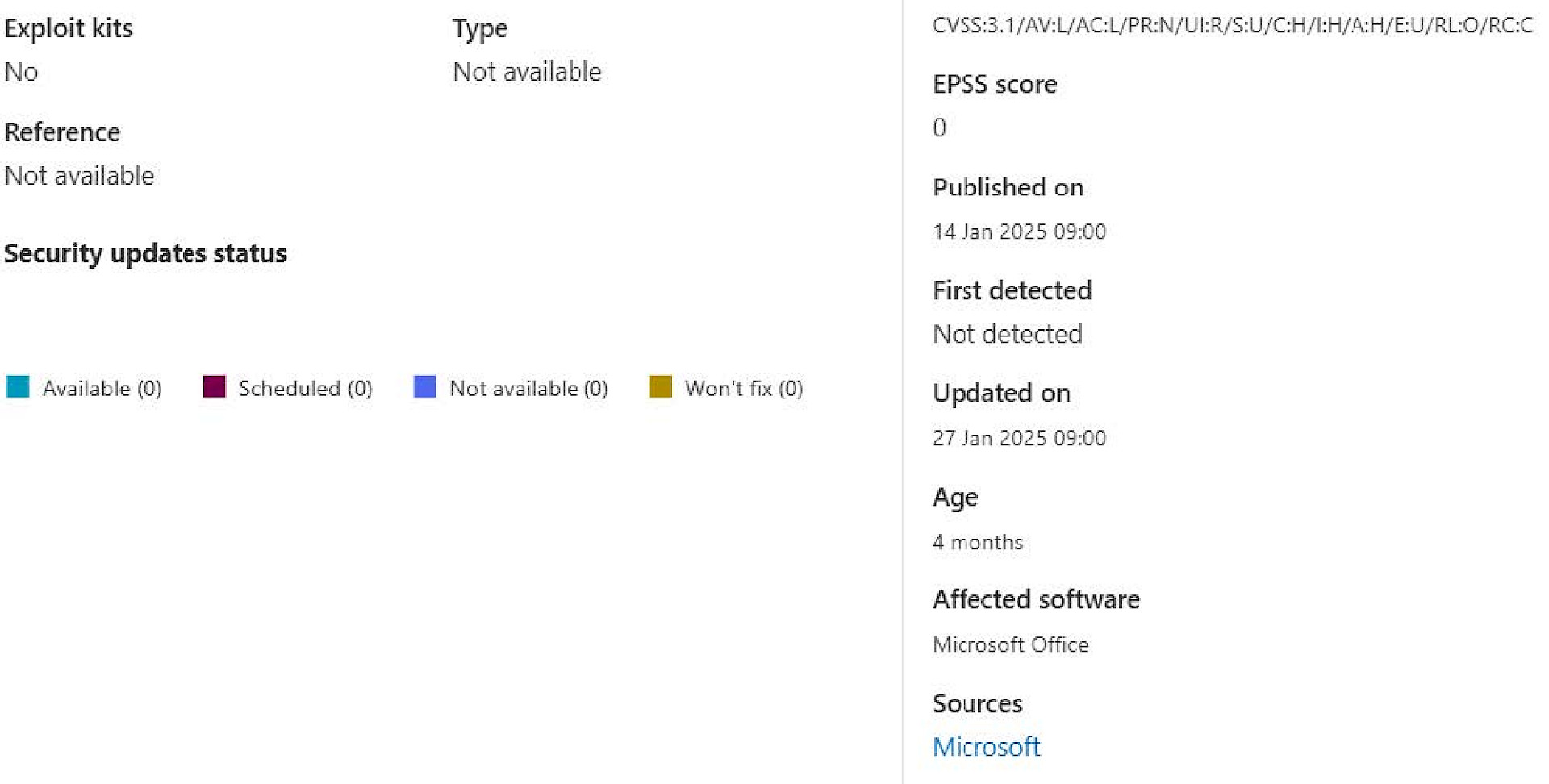
3. Check the details: Which devices are affected? Are there any known exploits?
To-Do: Choose a CVE suitable for your environment. Preferably one that has a high CVSS score or has been categorised as high in severity. Check which systems and which software are affected in the previously selected CVE. |
Step 3: Plan and implement measures
Objective: To systematically eliminate security gaps.
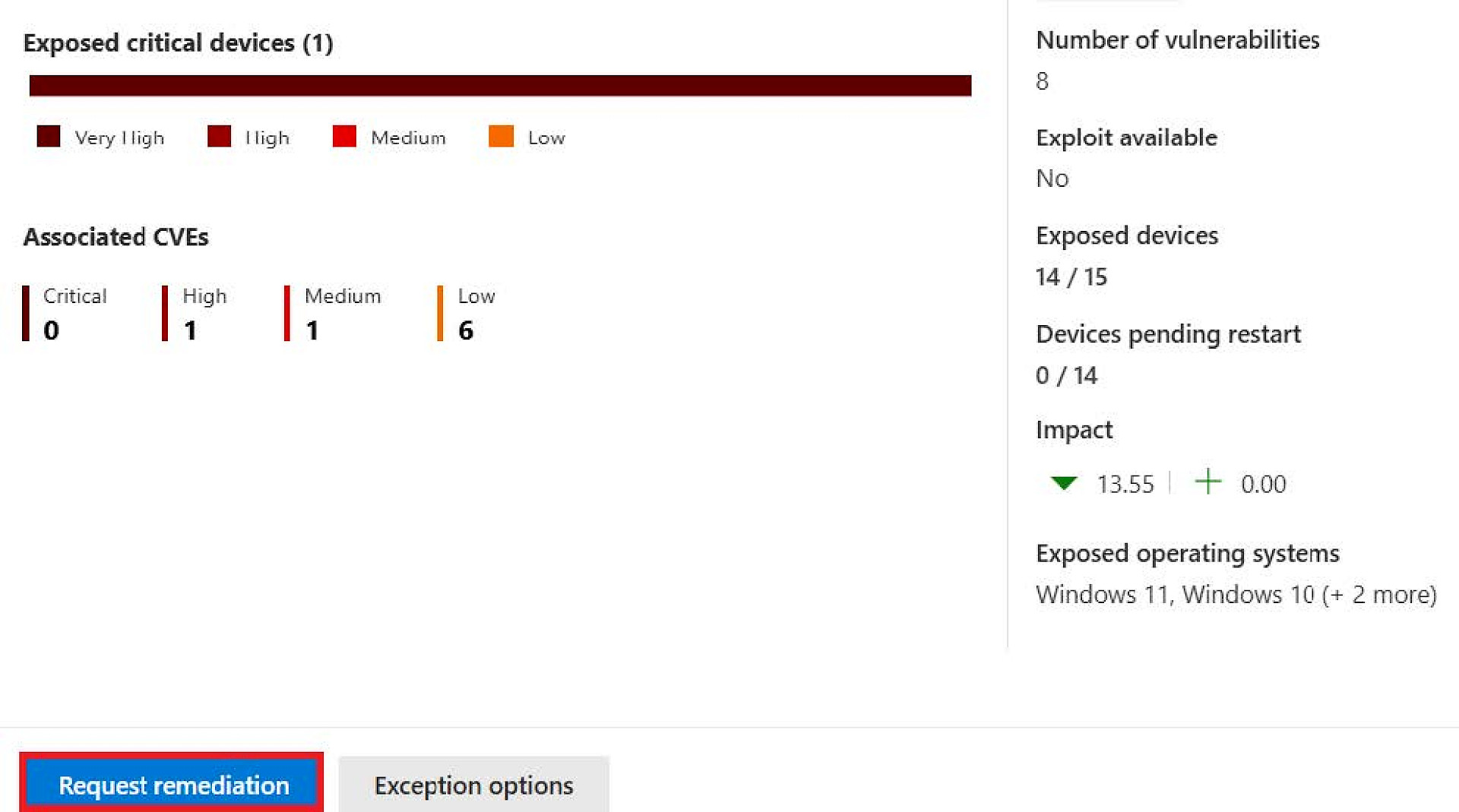
1. Open a CVE and click on “Go to security recommendations”
2. In the following window, click on “Request remediation”.
3. Create a ticket in Defender and assign the task to you.
To-Do: Use your selected CVE and create a maintenance request. Then take measures to rectify the vulnerability, e.g. by patching the relevant software or configuring the appropriate settings. Then check whether and which devices are still affected by the vulnerability. |
Documentation is important! Record which measures were planned and implemented and when.
Step 4: Monitor & report
Objective: To be able to measure and demonstrate progress.
1. Take a look at the exposure score - it shows your current risk situation.
2. Use the dashboard reports for vulnerability development and monitoring.
3. Export data for audits or external compliance requirements.
To-Do: Created tickets can be viewed in Defender under Endpoints → Vulnerability management → Remediation |
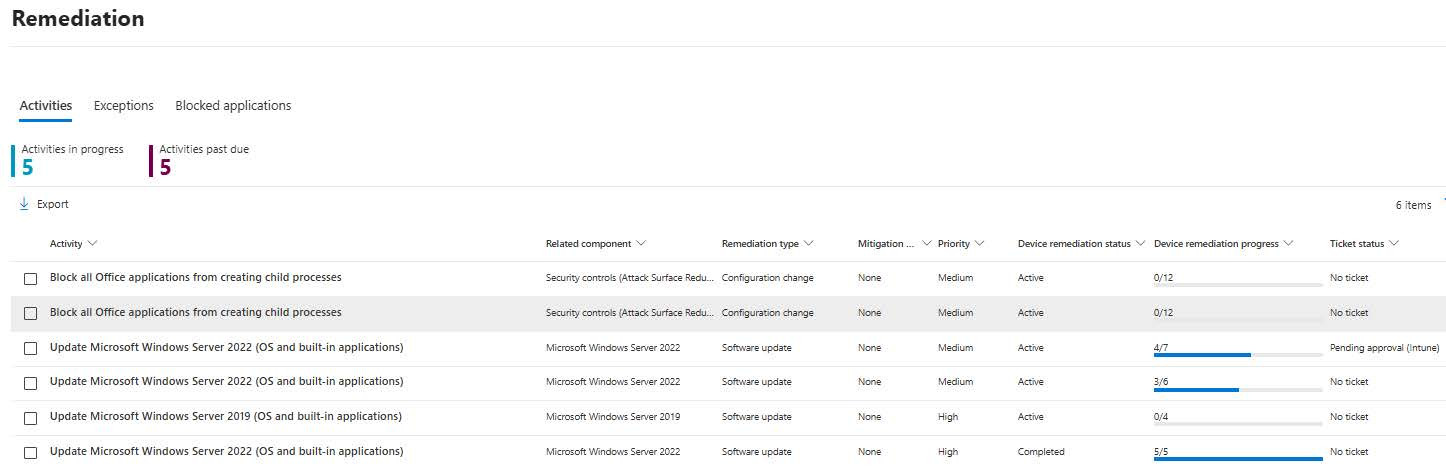
Check the status of your ticket here.
Result: react faster, protect better
This exercise not only provides technical expertise, but also a clear training effect: by going through the response flow in a structured way, internal processes are sharpened and cooperation between IT, security and management is improved. The result is a measurably faster response to new vulnerabilities - and therefore significantly better protection for the entire organisation.