Wiper-Malware (Part 5)
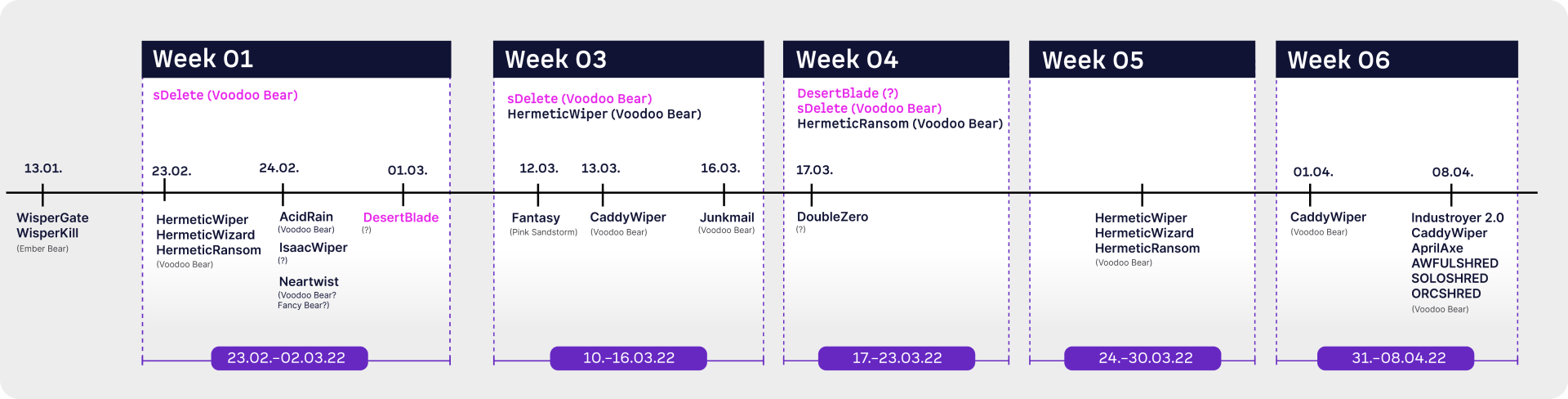
In addition to the Wiper, which I already introduced in Part 2 and Part 3, DesertBlade and sDelete aka secureDelete are also part of “Week 1” of the start of the Ukraine war. DesertBlade was used to attack a large Ukrainian broadcasting company, sDelete is a legitimate software that is used for unethical purposes.
DesertBlade
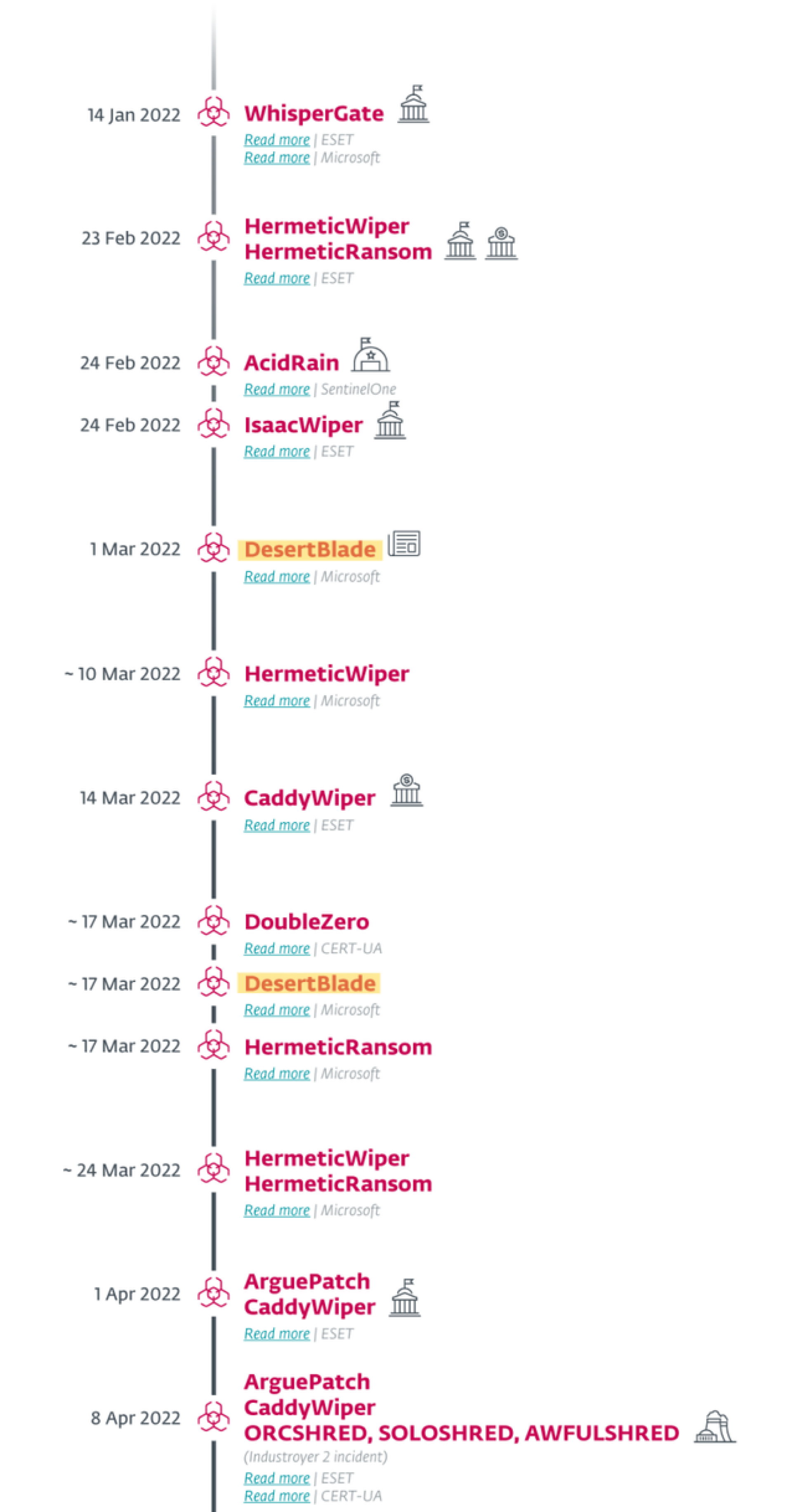
DesertBlade was used in the attack on a major Ukrainian broadcasting company and television station on March 1, 2022. On the same day, a missile attack was launched on a television tower in Kiev. Both attacks are presumably intended to demonstrate control. DesertBlade overwrites the files and then deletes them from all accessible drives and could be deployed via an Active Directory Group Policy Object (GPO). This indicates that the attacker was able to gain control of the network's Active Directory.
ESET points to another attack on March 17, 2022, which cannot be traced. However, Recorde Future also refers to a second attack in its report, but also to a lack of information about it. No further information on this wiper is available.
ESET Timeline - https://www.welivesecurity.com/2023/02/24/year-wiper-attacks-ukraine/
The Microsoft report “An overview of Russia's cyberattack activity in Ukraine” indicates that DesertBlade was also used again in Week 4 (March 17-23).
sDelete (alias secureDelete)
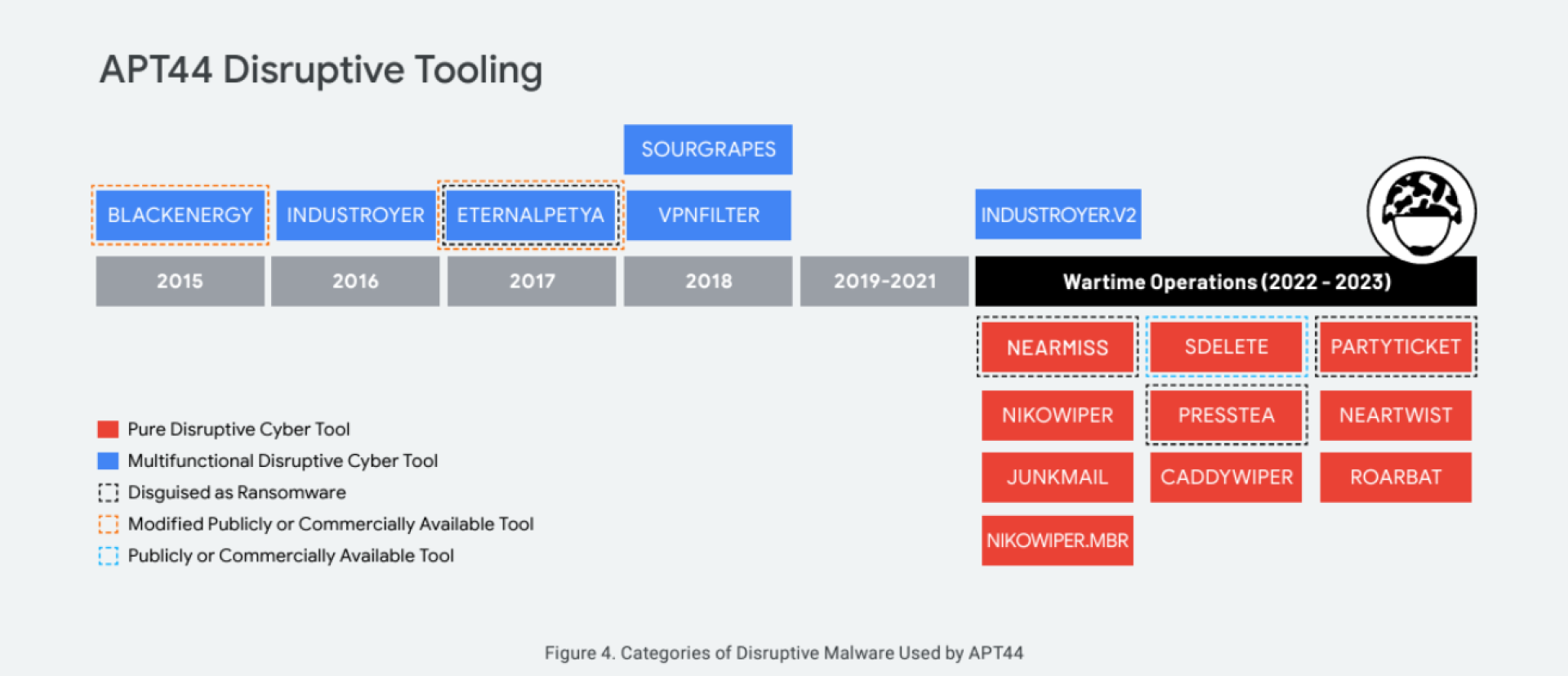
sDelete is a legitimate application that is used to delete file data. According to CERT-Europe and Mandiant, Voodoo Bear makes use of this feature.
https://services.google.com/fh/files/misc/apt44-unearthing-sandworm.pdf
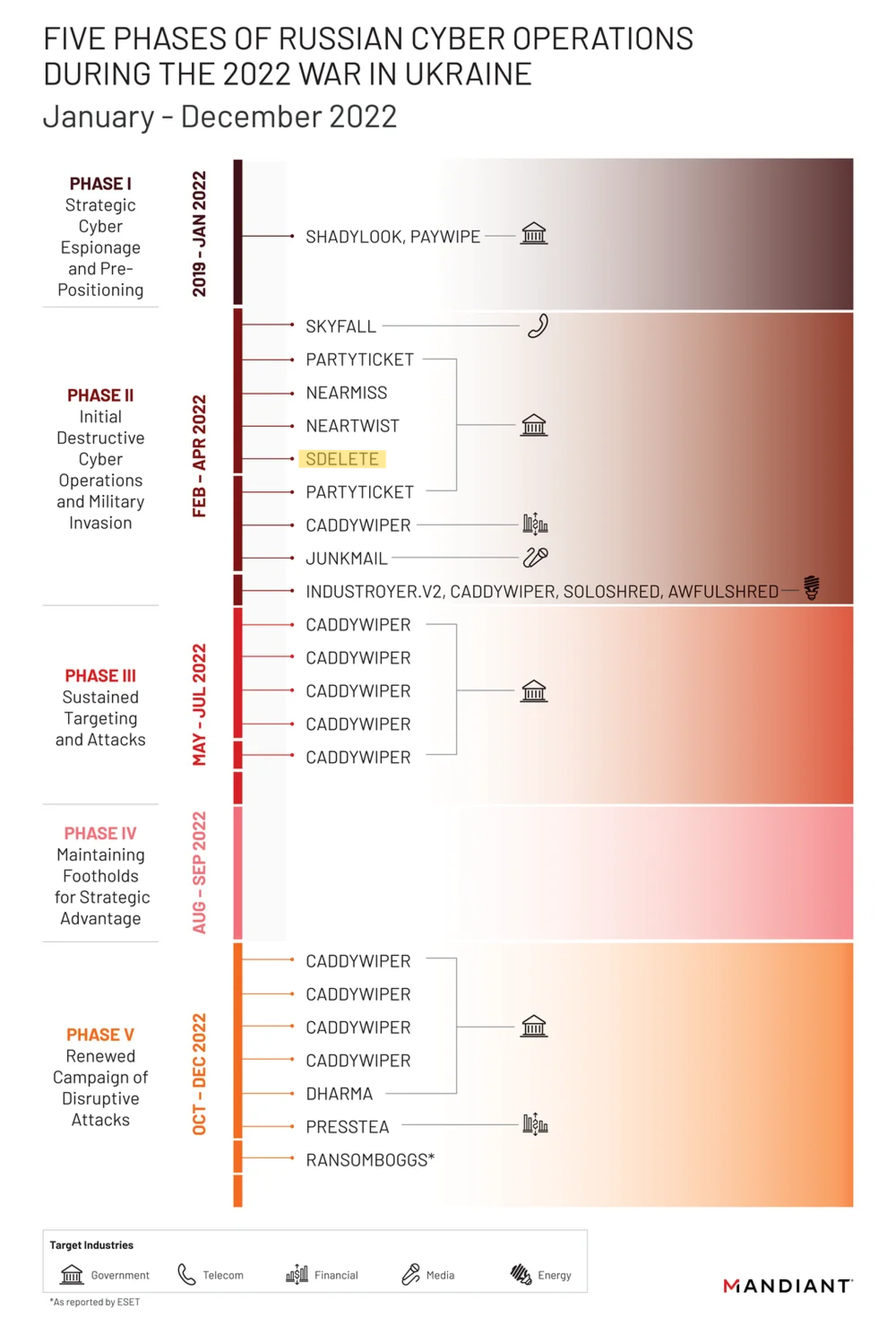
Mandiant uses the following graphic to indicate an attack in Phase II (February 2022 to April 2022) on an attack with sDelete, but no further information is available on this and, according to ESET, for example, it was not used until 2023.
As already mentioned, sDelete or secureDelete is a legitimate tool from Microsoft Sysinternals to legitimately delete file data based on the “Clearing and Sanitizing” standard DOD 5220.22-M of the US Department of Defense. The tool overwrites the data several times with random values before removing it from the file system.
This prevents the file from being restored using forensic methods. However, sDelete acts differently when securely deleting compressed, encrypted and sparse Windows NT/2K files. NTFS files are stored in 16-cluster blocks and new storage areas are allocated when the content is changed. This prevents direct overwriting. In addition, SDelete uses the defragmentation API to find out which clusters belong to the file and overwrites them specifically.
Securely deleting free disk space is often made more difficult due to the remnants of deleted files, which is why a different approach must be taken here too. To do this, sDelete creates a file that occupies the entire memory space and overwrites it with random values. Next, a second file is created to overwrite remaining, hard-to-access memory areas. On NTFS drives, the free areas of the Master File Table (MFT) are also filled with small files and overwritten.
Finally, the file names of the files are renamed 26 times, with each character being replaced by a consecutive alphabetical character. However, SDelete cannot directly overwrite the names of deleted files in the free space of a directory, as this area is not reallocated.
As can be seen from sDelete, even legitimate tools that were originally provided for legitimate purposes can be exploited by threat actors for their own purposes. The DesertBlade case also shows that wiper malware is not only used for the purpose of pure destruction, but also presumably to distract from or emphasize another attack for the time being.
For further research
DesertBlade
• https://msrc.microsoft.com/blog/2022/02/analysis-resources-cyber-threat-activity-ukraine/
• https://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE4Vwwd
• https://malpedia.caad.fkie.fraunhofer.de/details/win.desertblade
• https://go.recordedfuture.com/hubfs/reports/mtp-2022-0512.pdf
• https://www.welivesecurity.com/2023/02/24/year-wiper-attacks-ukraine/
sDelete
• https://cert.gov.ua/article/3718487 - 17.01.2023
• www.nts.eu/app/uploads/2024/10/20240910_Cyber-Domaine-im-Militaer-scharwitzl-ExecutiveDaysAustria24-WEST.pdf
• https://learn.microsoft.com/en-us/sysinternals/downloads/sdelete
• https://cloud.google.com/blog/topics/threat-intelligence/sandworm-disrupts-power-ukraine-operational-technology/?hl=en
• https://cert.europa.eu/static/MEMO/2023/TLP-CLEAR-CERT-EU-1YUA-CyberOps.pdf