Windows Server 2025: Understanding and Mitigating the "BadSuccessor" dMSA Threat
When am I compromised?
You are only compromised if you are using a Windows domain controller that uses Windows Server 2025, because dMSA was introduced in Windows Server 2025.
How to mitigate
Before diving into the technical depths of BadSuccessor, we want to be crystal clear:
Restrict dMSA permissions now and implement targeted monitoring immediately.
1. Mitigation
• Only highly trusted administrators should have the right to:
• Create msDS-DelegatedManagedServiceAccount (dMSA) objects.
• Modify the attributes msDS-DelegatedMSAState and msDS-ManagedAccountPrecededByLink.
• Reassess Organizational Unit permissions and remove inherited rights where unnecessary.
• Use tools like Akamai’s discovery script to identify accounts with dangerous dMSA access.
_________________________________________________________________________________________
2. Monitoring
• Enable Directory Service Change auditing on domain controllers:
• Audit Directory Service Changes - Windows 10 | Microsoft Learn
• Configure a SACL to log creation of new msDS-DelegatedManagedServiceAccount objects
• Configure a SACL for modifications to the msDS-ManagedAccountPrecededByLink attribute
• Enable dMSA event logs:
• Open Event Viewer
• In the left pane, expand Applications and Services and navigate to Microsoft\Windows\
Security-Kerberos\Operational.
• Logging for this provider is disabled by default, to enable logging, right-click on Operational and select
Enable Log.
• Source: Setting up delegated Managed Service Accounts (dMSA) in Windows Server 2025|Microsoft Learn
• Specifically monitor for:
• Event ID 307: dMSA object creation
• Event ID 308: Modification of msDS-ManagedAccountPrecededByLink
• Event ID 309: Modification of msDS-DelegatedMSAState
• Event ID 5136: Modification of Active Directory object
• Proactive Alerting:
• Forward these logs to Microsoft Sentinel to enable real-time detection. Set up custom alerts that are triggered
immediately upon the specific attribute changes mentioned above. While the dMSA-specific Event IDs
provided by Microsoft (e.g., 307, 308, 309) are useful, proactive alerting is likely more critical for
defending against this exploit.
Introduction to the "BadSuccessor" Vulnerability
A newly identified, critical vulnerability named "BadSuccessor" affects Windows Server 2025 Domain Controllers. This vulnerability exploits a feature known as "delegated Managed Service Accounts" (dMSAs). It is noteworthy that dMSAs were originally designed to improve security, for example, by automating password management and resolving older issues with service accounts. The irony is that BadSuccessor turns this very mechanism, which was intended to increase security, into a significant attack vector. This underscores the need to continuously assess even new, security-oriented features for unforeseen vulnerabilities.
Potential Impact and Severity
The potential consequences of a successful attack are severe: attackers could gain complete control over the entire Active Directory domain, including domain administrator accounts. Such a loss of control can lead to catastrophic scenarios, such as widespread data theft, the manipulation of critical systems, or even a complete operational outage.
There is a discrepancy in the risk assessment. While Microsoft currently rates the vulnerability as "moderate" and is not providing an immediate patch, its discoverers at Akamai and other experts emphasize a significantly higher practical risk. This higher risk assessment is based on the ease of executing the attack once minimal preconditions—often inconspicuous permissions—are met. Given these differing assessments and the lack of an immediate patch, it is advisable to adopt a more cautious stance and take proactive measures that account for the higher risk assessment.
dMSA Exploitation
The Deceptive Simplicity of the Attack
Although dMSAs are conceptually beneficial, their specific mechanism for account migration and attribute linking has a flaw that is exploited by BadSuccessor. Attackers do not need to compromise the target account directly. Instead, they manipulate the dMSA object itself. Specifically, attackers "simulate" a migration by directly setting two attributes of a dMSA object: msDS-ManagedAccountPrecededByLink is set to the Distinguished Name (DN) of the target account, and msDS-DelegatedMSAState is set to the value 2 (migration completed). This "simulated migration" does not require any permissions on the superseded account; write permissions for the attributes of any dMSA are sufficient.
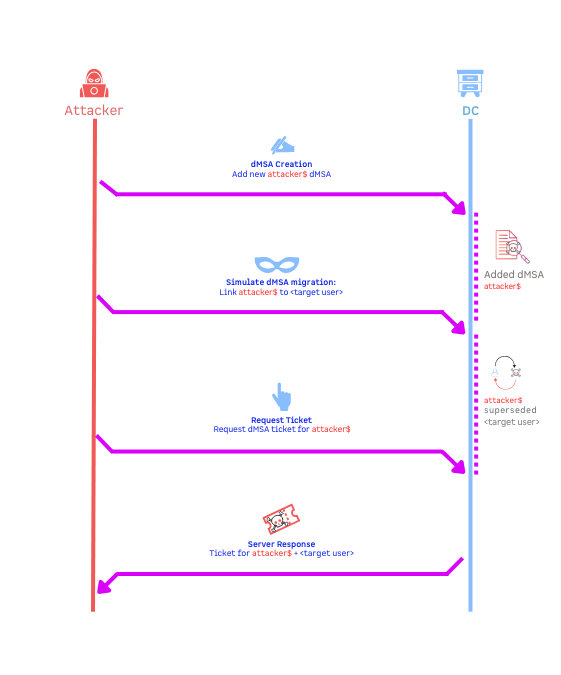
BadSuccessor: Abusing dMSA to Escalate Privileges in Active Directory
This attack is particularly insidious because it abuses legitimate Active Directory functions. It does not require typical suspicious activities like changes to group memberships or the direct escalation of existing account privileges, which are often monitored by traditional security systems. Consequently, organizations that rely solely on such conventional monitoring mechanisms could miss this type of attack. This highlights the need for specific monitoring measures focused on the creation and attribute modification of dMSAs.
The Low Barrier to Entry: Prerequisites for Attackers
Alarmingly, an attacker only needs seemingly minor permissions to execute the BadSuccessor attack: the ability to create new dMSA objects or modify specific attributes of existing dMSAs. Akamai research has shown that such permissions are often inadequately controlled and widespread. In 91% of the corporate networks studied, normal users who were not domain administrators already had the necessary rights to carry out this attack.
These permissions required for the attack, such as the right to create msDS-DelegatedManagedServiceAccount objects or to create all child objects in an Organizational Unit (OU), are often classified as harmless or low-risk and are therefore typically not subject to strict monitoring or hardening. This widespread misjudgment of the risk of minor AD permissions represents a systemic weakness that opens the door for attackers. A core component of the mitigation strategy must therefore be the reassessment and tightening of these "insignificant" permissions.
Current Status: No Official Patch As of the time of this notice (based on information from May 21, 2025), Microsoft has not released an official patch for this vulnerability, although there are plans to address the issue in the future. This means that companies cannot rely on a short-term fix from the vendor and must take immediate proactive measures to protect themselves. The recent release of a simple proof of concept makes this threat easily exploitable, and we anticipate a corresponding increase in attack frequency. For more information, please see the following information: GitHub - logangoins/SharpSuccessor: SharpSuccessor is a .NET Proof of Concept (POC) for fully weaponizing Yuval Gordon’s (@YuG0rd) BadSuccessor attack from Akamai.
Hunting Queries
let QueryPeriod = 1h;
let dMSARegKey = dynamic(["DelegatedMSAEnabled"]);
let dMSAMonitor =
SecurityEvent //or WindowsEvent
| where TimeGenerated > ago(QueryPeriod)
| where EventID == 307 or // dMSA Migration
EventID == 308 or // dMSA Permission Add
EventID == 309; // dMSA Key Fetch
DeviceRegistryEvents
| where TimeGenerated > ago(QueryPeriod)
| where ActionType == @"RegistryKeyCreated" or ActionType == @"RegistryValueSet"
| where RegistryKey has_any(dMSARegKey)
| union dMSAMonitorPurpose: Detect registry key events that are set by dMSA usage. Source: Hunting-Queries-Detection-Rules/Sentinel/BadSuccessor Detection.kql at main · SlimKQL/Hunting-Queries-Detection-Rules · GitHub
SecurityEvent //or WindowsEvent
| where EventID == 5136
| extend ParsedEventData = parse_json(EventData)
| extend AttributeLDAPDisplayName = tostring(ParsedEventData.AttributeLDAPDisplayName)
| where AttributeLDAPDisplayName has "ManagedAccountPrecededByLink"Purpose: Detect modifications to the msDS-ManagedAccountPrecededByLink attribute.
References
BadSuccessor: Abusing dMSA to Escalate Privileges in Active Directory
Setting up delegated Managed Service Accounts (dMSA) in Windows Server 2025
Hunting-Queries-Detection-Rules/Sentinel/BadSuccessor Detection.kql at main · SlimKQL/Hunting-Queries-Detection-Rules · GitHub
Akamai’s discovery script
Audit Directory Service Changes - Windows 10 | Microsoft Learn
GitHub - logangoins/SharpSuccessor: SharpSuccessor is a .NET Proof of Concept (POC) for fully weaponizing Yuval Gordon’s (@YuG0rd) BadSuccessor attack from Akamai.



