Voodoo Bear (APT44 - Part 2)
Alias: ELECTRUM, Telebots, IRON VIKING, BlackEnergy (Group), Quedagh, Voodoo Bear, IRIDIUM, Seashell Blizzard, FROZENBARENTS
Part 1 has already gone into more detail about Voodoo Bear and the known attacks associated with it. In summary, it can be said that Voodoo Bear is part of the Russian government's ‘Ministry of Defence’ and is therefore state-sponsored. In addition, many different sectors are targeted by the group. These include Government, Military and Defence, Energy, Financial, Heavy Industry, High Tech and Telecom, Higher Education, News Media, NGOs, and Shipping and Rail.
The group's main motivations are espionage, influencing technical information and psychological manipulation.
Attacks such as Viasat 2022 or NotPetya are associated with Voodoo Bear.
In this part, I would like to take a closer look at and analyse the tactics, techniques and procedures (TTP) associated with the attacks from Part 1.
Tactics, Techniques, and Procedures
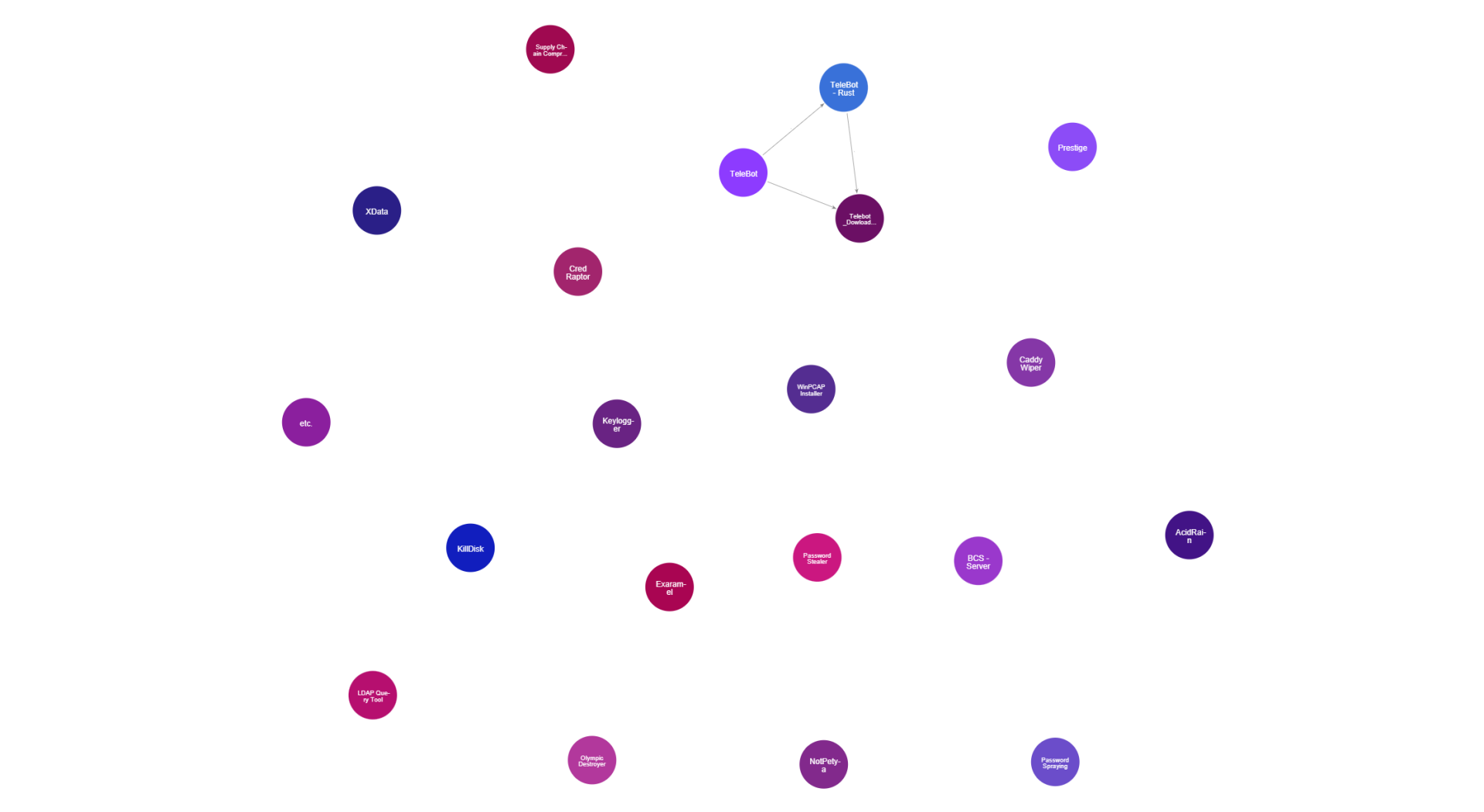
As can be seen in the MITRE ATT&CK framework above, Voodoo Bear uses many different techniques, tactics and procedures. The points marked in blue are general TTPs used by this hacker group, the points marked in red are TTPs that were recorded with associated campaigns and the points marked in pink are TTPs that could be assigned to campaigns and the group in general.
The TTPs include, for example, “Account Manipulation” (T1098), “Brute Force” (T1110) and “Windows Management Instrumentation” (T1047), all three of which were used in the “Ukraine Electric Power Attack”, the second largest public attack by Voodoo Bear, in December 2016, in which substations and Ukrainian power grids were attacked and disrupted. The attackers mainly used the malware “Industroyer” (S0604).
In the first “Ukraine Electric Power Attack” in 2015, TTPs such as “Phishing: Spearphishing Attachment” (T1566.001), “System Firmware” (T0857) and “Input Capture: Keylogging” (T1056.001), in which the malware “BlackEnergy” (S0089) and “KillDisk” (S0607) were used in particular.
In the last “Ukraine Electric Power Attack” from June 2022 to October 2022, TTPs such as “Data Destruction” (T1485), “Protocol Tunneling” (T1572), “Masquerading: Masquerade Task or Service” (T1036.004) and the malware CaddyWiper (S0693) were used.
AcidRain
Alias: -
AcidRain (S1125), the malware used in the attack on Viasat2022, is a wiper, a less common type of malware that destroys data in most cases.
SentinelLab notes that an AcidRain attack like Viasat's requires a BruteForce attempt, which indicates that Voodoo Bear was not aware of the specifics of the target system or that this binary should be reusable. This is also shown by the AcidRain variant AcidPour.
Once the attackers were in the system, the processes differ depending on whether the wiper is executed as root or not.
If AcidRain is executed as root, it first overwrites and deletes non-default files in the file system. Standard files are, for example, text or HTML files.
If the malware is not executed as root, thorough deletions of file systems and storage device files are carried out.
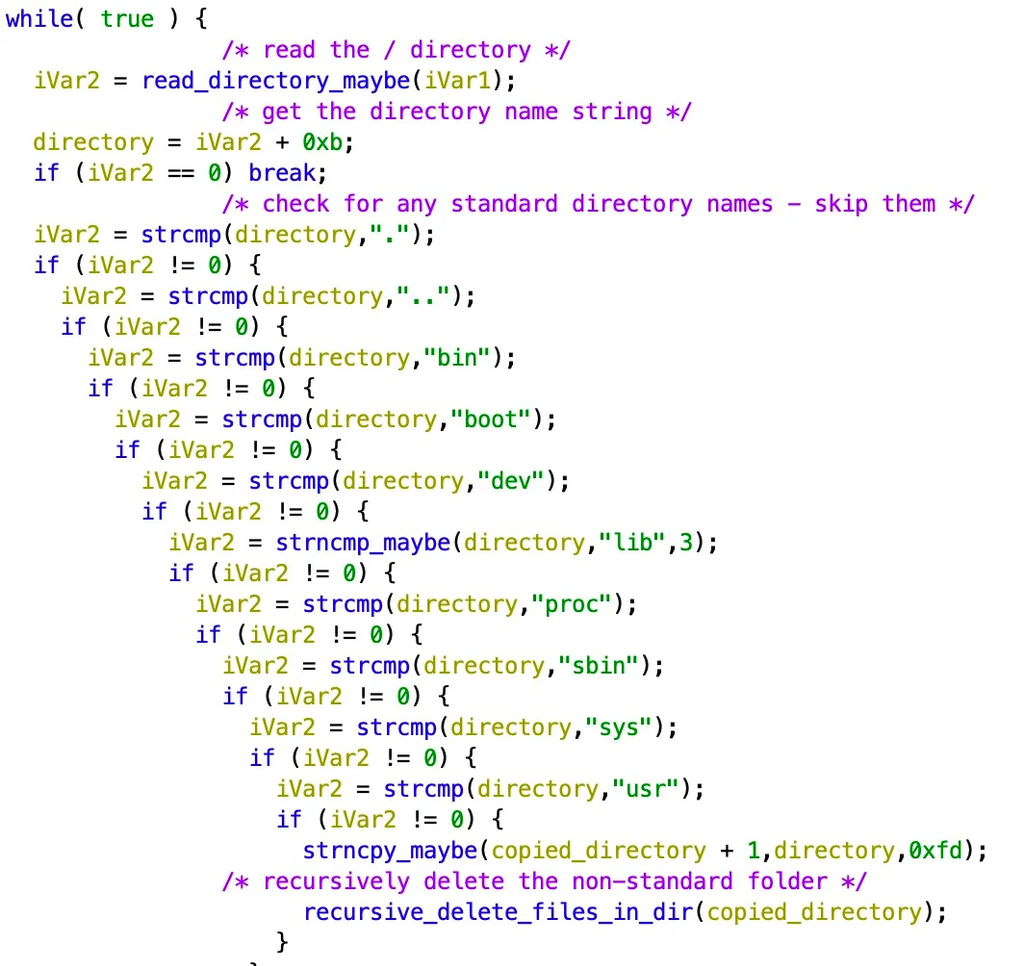
“Recursively delete files in nonstandard folders” (SentinelLAB, 2022, “AcidRain | A Modem Wiper Rains Down on Europe“) - https://www.sentinelone.com/labs/acidrain-a-modem-wiper-rains-down-on-europe/
The next step is to attempt to destroy data in storage device files such as /dev/mtdblock* or /dev/sd*. To do this, all possibilities such as /dev/sd0 to /dev/sd99 are tried, opened and overwritten with 0x40000 bytes or system calls such as MEMGETINFO, MEMUNLOCK, MEMERASE and MEMWRITEOOB are executed, all of which lead to the data being overwritten.
Finally, en fsync is executed, which ensures that all buffered data (data that is temporarily held in memory in order to be able to write to the hard disk more efficiently) is immediately written to the data carrier to ensure that all data has been overwritten. A reboot is then performed and the device is no longer functional.
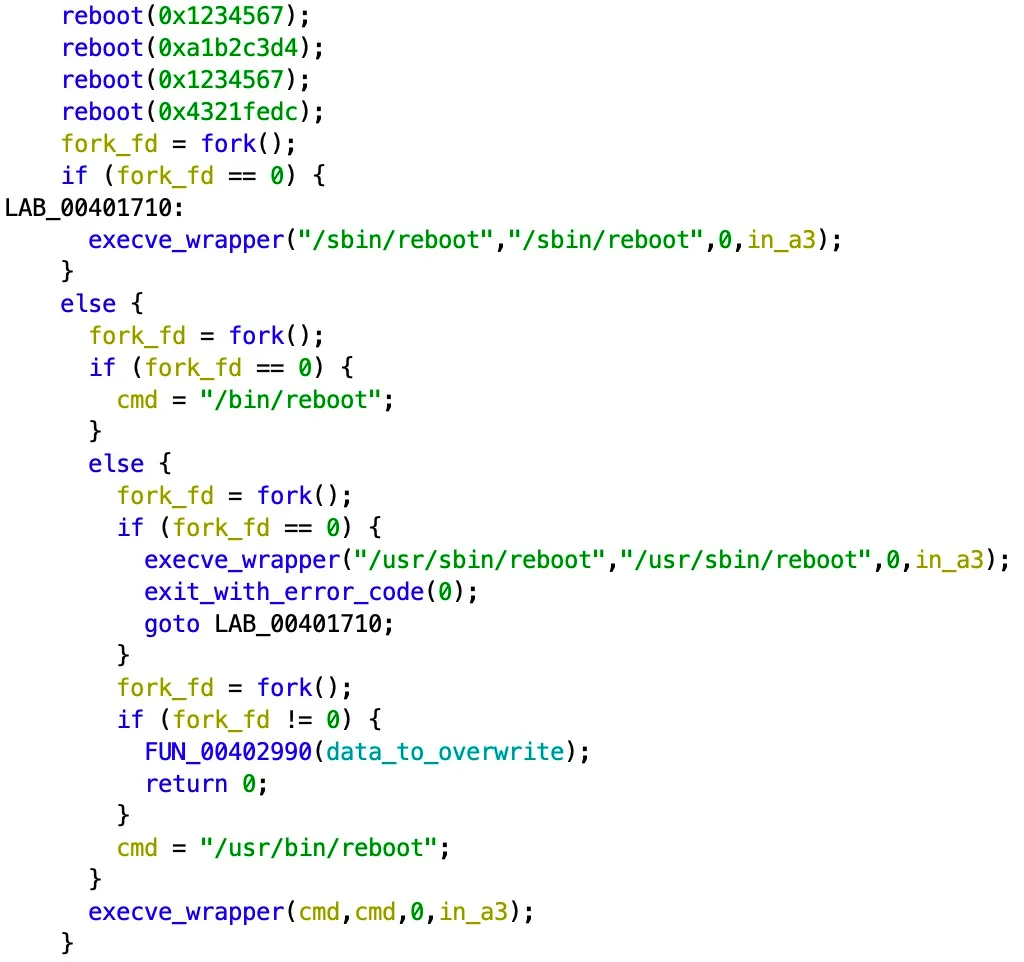
Several commands for a reboot - https://www.sentinelone.com/labs/acidrain-a-modem-wiper-rains-down-on-europe/
It is striking that AcidRain and a VPNFilter plug-in have some similarities.
VPNFilter is a modular malware that targets SOHO routers and QNAP storage devices and is generally classified by the FBI as APT28 and NSA and CISA as GRU.
This associated plugin is responsible for stealing credentials and monitoring Modbus SCADA protocols. In addition, it also has functionalities such as deleting and destroying devices and carrying out DDoS attacks. It is noticeable that AcidRain and the VPNFilter plug-in are binary files in MIPS-ELF, and a large part of the code appears to originate from a statically linked libc.

AcidRain on the left, VPNFilter on the right - https://www.sentinelone.com/labs/acidrain-a-modem-wiper-rains-down-on-europe/
It also appears that both share a compiler. This assumption is supported by identical entries in the header.

“Section Headers Strings Tables for VPNFilter and AcidRain” (SentinelLAB, 2022, “AcidRain | A Modem Wiper Rains Down on Europe”) - https://www.sentinelone.com/labs/acidrain-a-modem-wiper-rains-down-on-europe/
| ID | Name | ||
| T1485 | Data Destruction | ||
| .001 | Disk Wipe: Disk Content Wipe | ||
| T1083 | File and Directory Discovery | ||
| T1529 | System Shutdown/Reboot | ||
Industroyer
Alias: CRASHOVERRIDE, Win32/Industroyer, Industroyer2
Industroyer (S0604), which was used in the attacks on the Ukrainian electricity power supply and is probably only used by Sandworm, is a specialized malware that was developed and used to disrupt industrial control systems (ICS). As the 2016 and 2022 attacks on the Ukrainian power supply show, there are two different versions.
The Industroyer or CrashOverride, which was used in 2016 and was able to manipulate several industrial communication protocols. One such protocol is IEC 101, a standard protocol that is used between control centers and remote devices (remote terminal units) and especially with older serial communication interfaces. Other protocols are IEC 104, OPC and IEC 61850. This type of industrial hacking leads to short-term power failures and a longer recovery time for the affected systems as a result of targeted manipulation.
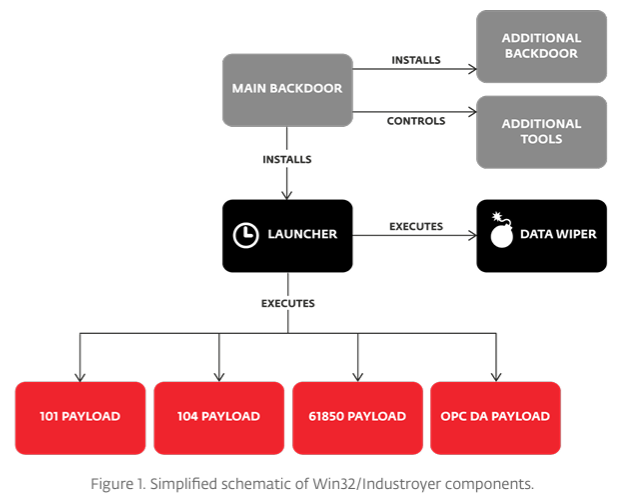
Attack Chain Industroyer - https://web-assets.esetstatic.com/wls/2017/06/Win32_Industroyer.pdf
Looking at the structure of Industroyer, it is noticeable that the main backdoor is the point from which everything starts. This main backdoor was the central entry point and disguises itself as a legitimate Windows service by using Windows APIs such as “StartServiceCtrlDispatcherW”. In addition to the Windows APIs, obfuscated string and control flow structures, such as cmp edx, 142F9F9Ah which leads to a jump to another in the code, are used to make analysis more difficult.
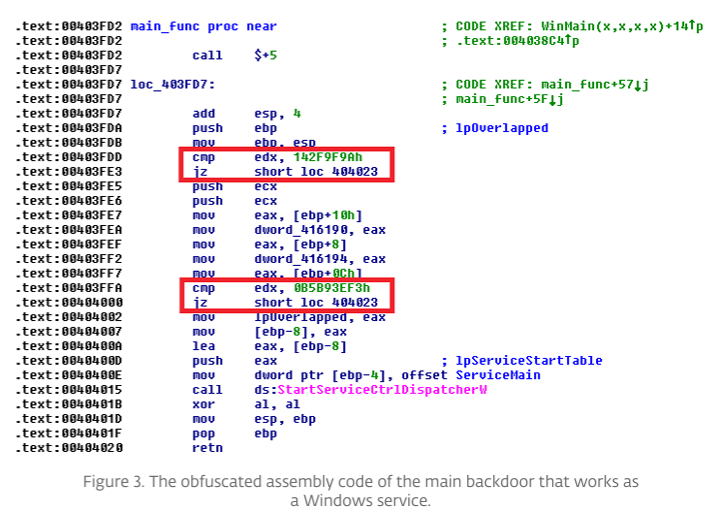
A jump to another Codeline - https://web-assets.esetstatic.com/wls/2017/06/Win32_Industroyer.pdf
The main backdoor also ensures command and control (C2).
Parallel to the main backdoor, an additional backdoor is installed, which serves as redundant access and the attackers therefore have another backdoor available even if the main backdoor is discovered.The additional tools can be used to add further modules that support specific tasks and thus serve as aids for the preparation, execution and follow-up of the attack.
The time-controlled launcher is a component that activates the data wiper and the payloads. The “GetLocalTime” command is used in the code to regularly check the local time. If the stored time is reached, the code continues.
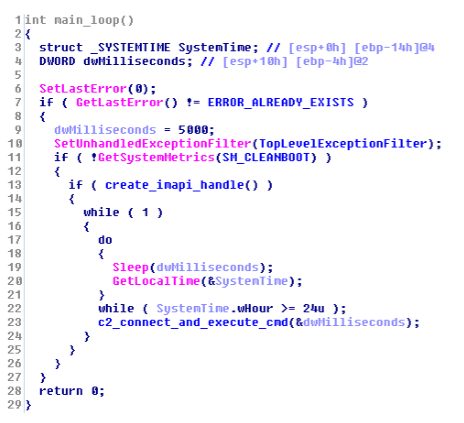
Time-controlled launcher - https://web-assets.esetstatic.com/wls/2017/06/Win32_Industroyer.pdf
Starting the payloads, which are tailored to the industrial communication protocols (IEC 101, ...), can now communicate directly with the devices and manipulate them.
The data wiper, in this case KillDisk, is executed to render the system unusable after the attack. In this case, the wiper overwrites the data with random data.
Industroyer ID | Name | |
Endpoint Denial of Service: Application or System Exploitation | ||
Industroyer 2 (S1072), which was used in the Ukraine Electric Power Attack 2022, is a further development of Industroyer. In contrast to Industroyer, Industroyer 2 is primarily aimed at the IEC 104 protocol. This protocol is a further development of the IEC 101 protocol and transmits data via TCP/IP networks instead of serial connections.
This protocol sends periodic data and events to monitor the SCADA systems used to control the power grid. Other noticeable differences between Industroyer and Industroyer 2, apart from the protocol selection, are that Industroyer 2 is more modular and better disguised than its predecessor. In addition, the wiper CaddyWiper and not KillDisk was used in this case.
As with its predecessor, this version also includes a time-controlled launcher, which enables precise synchronization.When the specified time is reached, the IEC 104 payload is executed, which can open and close the circuit breakers directly. In addition, data packets are sent to RTUs to take control of the power distribution networks. The targeted sending of commands to RTUs to open or close circuit breakers in substations ultimately leads to power outages.
Now the data is overwritten using the Caddy Wiper, and logs and the master boot record are deleted to make recovery more difficult and cover traces.
Industroyer 2 ID | Name |
NotPetya
Alias: ExPetr, Diskcoder.C, GoldenEye, Petrwrap, Nyetya, Petya 2.0
NotPetya (S0368) is a wiper ransomware. It is responsible for a high number of cyberattacks in 2017. Initially, only Ukraine was affected, but it spread almost worldwide within a very short time. It is suspected that Ukraine was the targeted country, but that this wiper accidentally spread further, but this assumption cannot be proven, as it is only a guess.
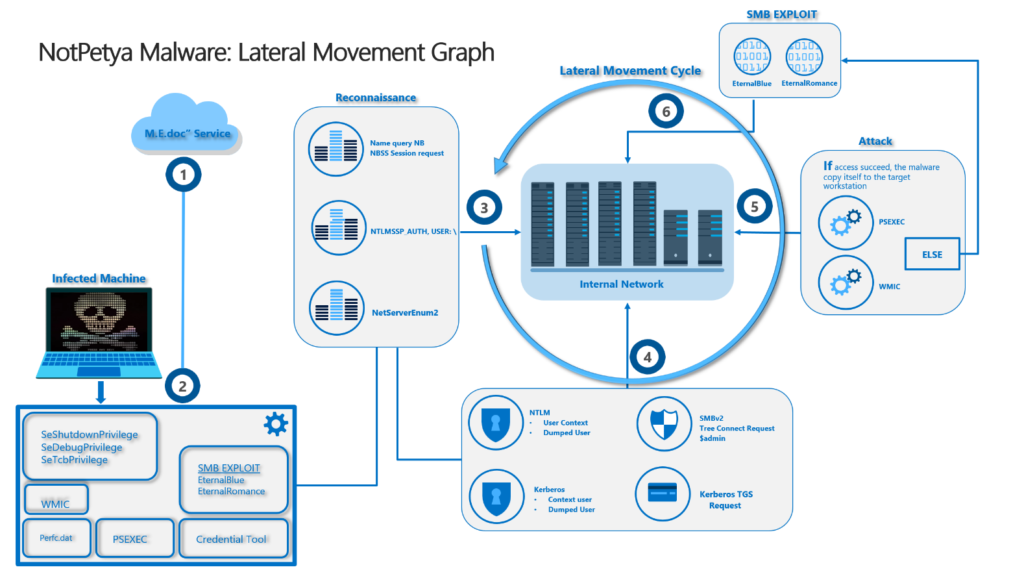
Attack Chain NotPetya - https://www.microsoft.com/en-us/security/blog/2017/10/03/advanced-threat-analytics-security-research-network-technical-analysis-notpetya/
Step 1:
Various analyses show that the attackers were able to gain access to the systems through the widely used Ukrainian accounting software MeDoc.
Step 2:
Now NotPetya uses high privileges like ...
The SeShutdownPrivilege privilege allows the malware to shut down and restart the system and is used by NotPetya to restart the system after the wiper process, which is a typical action of a wiper.
SeDebugPrivilege enables processes with high protection to be manipulated or debugged. With NotPetya, this privilege is used to attack critical processes and gain further authorizations.
SeTcbPrivilege is also known as “Act as part of the operating system” and makes it possible to change user contexts and thus gain system privileges.
Also, various Windows-based tools and exploits to run on the machine and prepare to migrate laterally. These tools and exploits are:
WMIC (Windows Management Instrumentation Command-Line) is used to execute administrative commands, inventory systems and perform malware operations and is used in NotPetya to remotely control and spread to other machines on the network.
PSEXEC (remote administration tool), a legitimate remote administration tool from Microsoft is used to remotely install and execute the malware on other computers.
SMB exploits, including EternalBlue and EternalRomance, are vulnerabilities that are used to exploit and spread vulnerabilities in the SMB (Server Message Block) protocol. As a result, unpatched systems can be accessed and arbitrary code can be executed
Credential dumping, or mimikatz, is used to extract user information from the memory and thus exploit legitimate user rights and access other machines.
Another part of the second part is perfc[.]dat. This file contains most of the malicious code that is executed after infection. The name was chosen as a disguise and is intended to represent a legitimate Windows file. The file name suggests a connection to performance counter functions. Immediately after creation, the code from perfc[.]dat is loaded directly into memory and executed, preventing the malware from being detected by antivirus programs that rely on scanning files on the hard disk.
Step 3:
After the system has been infected and privileges have been obtained, the system is scanned and analyzed, and other potential targets are identified.
The item Name Query NB, NBSS Session Requests determines names and sessions of network hosts to find devices in the network
NTLSSP Auth USER and NetServerEnum2 are tools and functions that enumerate network shares and resources such as servers or workstations.
Step 4:
Next, information is obtained in order to extract user access data. For this purpose, a distinction is made between NTLM, SMBv2, Kerberos and Kerberos TGS Request.
NTLM (NT LAN Manager) is an authentication protocol developed by Microsoft to verify users and ensure access control in networks. It uses password hashes for authentication. NotPetya uses NTLM by extracting these hashes directly from the memory of the infected system using tools such as Mimikatz. These credentials allow the malware to perform pass-the-hash attacks, where it moves to other systems on the network without needing the actual password. By using the stolen NTLM data, NotPetya gains access to other machines, especially if the users have administrative privileges.
SMBv2 (Server Message Block Version 2) is a network protocol used in Windows systems for file and printer sharing and remote access services. It is an improved version of the older SMBv1 protocol that is more efficient and secure. NotPetya uses SMBv2 to access shared resources on the network and spread laterally. Using stolen credentials from NTLM hashes, the malware can send Tree Connect requests to other systems to gain access to shared folders or drives. If SMBv1 is disabled or patched, SMBv2 is often chosen if the network structure allows it.
Kerberos is a modern, secure authentication protocol that is used in Windows networks. It is based on a ticket-based system in which users or services receive so-called tickets from the Key Distribution Center (KDC) in order to access network resources. NotPetya uses stolen credentials to generate Kerberos tickets to gain access to additional resources. This happens in particular when the malware attacks systems that use Kerberos for authentication. With the captured tickets, it can impersonate a legitimate user and continue its spread.
A Kerberos TGS request (Ticket Granting Service Request) is a specific request within the Kerberos protocol in which a user or software requests access to a specific network device or service. NotPetya generates TGS requests by exploiting the user information it has already collected. These requests allow the malware to obtain access tickets for various services on the network. If the stolen credentials come from users with privileged rights, NotPetya can gain deep control over the network and move to critical resources.
By combining these protocols and techniques, from NTLM and SMBv2 to Kerberos and specific TGS requests, NotPetya is able to spread laterally across the network and efficiently abuse user credentials to spread the malware. This methodology allows the malware to quickly and unobtrusively gain control over a large number of systems in a network.
Step 5:
After NotPetya has gained credentials and privileged access to systems in the previous phases, the malware begins to transfer its payload to new targets and continue execution. This phase builds on the previous lateral movement techniques, but uses specific mechanisms to complete the infection.
If the malware successfully gains access to a target system, various techniques are used to copy and execute the malware. First, NotPetya uses the stolen credentials to gain access to administrative shares such as C$ or ADMIN$. The perfc.dat file, which contains the malicious code, is stored there.
To ensure the payload is executed, NotPetya relies on tools such as PSEXEC and WMIC. With PSEXEC, a legitimate remote execution tool, the malware executes its payload on the new target system. If PSEXEC is blocked or unavailable, the malware uses WMIC to execute commands remotely on the target system. These commands launch the malware and initiate the destruction process.
This step is crucial to spread the infection to other systems and increase the malware's network traffic. If a system is successfully infected, the malware returns to the previous stages to attack other systems on the network.
Step 6:
After successful distribution and execution on other systems in the network, NotPetya carries out the final attack, which renders the affected system unusable. The decisive step here is the encryption of the hard disk's master file table (MFT), which regulates the organization of the files on the data carrier.
The malware uses its high privileges to gain access to the hard disk. It specifically encrypts the MFT with a key that is not saved, resulting in the irrevocable loss of data. In contrast to conventional ransomware, the aim is not to extort money, but to destroy the data.
After encryption, SeShutdownPrivilege forces the system to restart. When it restarts, a ransom note appears, suggesting that the data can be restored by making a payment. However, this is not possible as the required decryption key is deliberately not available.
This final step completely disrupts the operation of the infected systems and causes significant damage, especially in networks that depend on many infected devices. The combination of irreversible encryption and the targeted destruction of systems makes it clear that NotPetya was not aiming for financial gain, but to cause maximum damage.
ID | Name | |
Voodoo Bear Part 3
Part 3 takes a closer look at hunting and queries in the area of the software mentioned. These contain Yara rules, which can be helpful in the course of AcidRain, NotPetya or Industroyer.
Similar hacker groups
In addition to Voodoo Bear, there are seven other Russian state-sponsored hacker groups.
Fancy Bear (APT28)
Alias: Fancy Bear, APT28, IRON TWILIGHT, SNAKEMACKEREL, Swallowtail, Group 74, Sednit, Sofacy, Pawn Storm, STRONTIUM, Tsar Team, Threat Group-4127, TG-4127, Forest Blizzard, FROZENLAKE
APT28 is also a constant threat alongside APT29, but unlike APT29 it is not subordinate to the Russian Foreign Intelligence Service (SVR), but to Russian military intelligence (GRU) or the Ministry of Defense. In addition to Ukraine and NATO, the group is also interested in Europe, South America, the Middle East and Central Asia.
There is also interest in various sectors such as government, military and defense, energy, finance, heavy industry, high-tech and telecommunications, higher education, news media, NGOs, and shipping and rail transport
Fancy Bear uses TTPs such as xTunnel, Mimikatz or Evil-Twin.
Cozy Bear (APT29)
Cozy Bear, primarily known as APT29, is believed to be under the control of the SVR.
There is also interest in various sectors such as biotechnology, consulting, education, financial services, government, healthcare, legal services, nonprofits, pharmaceuticals, technology, telecommunication, think tanks, travel, science/R&D
Voodoo Bear uses TTPs such as spearphishing attachments, Azure and M365 environment via Microsoft Graph API, password guessing and password spraying, exploit public-facing applications, FoggyWeb, GoldFinder, NativeZone and WellMess, RegDuke, PolyglotDuke, MiniDuke and FatDuke, SUNBURST, SUNSPOT and TEARDROP
Primitive Bear
Primitive Bear (aka Aqua Blizzard or Gamaredon) is also a Russian state-sponsored hacking group that has been linked to the Russian Federal Security Service (FSB). Just like Voodoo Bear, the main target is Ukraine, including government agencies, the military, non-governmental organizations, the judiciary, law enforcement agencies and non-profit organizations, as well as institutions related to Ukrainian affairs. This group also relied on espionage and exfiltration of sensitive data
Primitive Bear uses TTPs such as spear phishing emails, VBScripts, Ping, PowerPunch, Pterodo, QuietSieve, DinoTrain, DesertDown, DilongTrash, ObfuBerry and ObfuMerry
Venomous Bear
Venomous Bear is primarily known as Turla and, like Primitive Bear, is subordinate to the Russian Federal Security Service (FSB). According to Google, the group is primarily interested in Ukraine, NATO, Australia, South America, the Middle East and South-East Asia.
There is also interest in various sectors such as government, military and defense, higher education, news media and NGOs
Venomous Bear uses TTPs such as KOPILUWAK, QUIETCANARY, ANDROMEDA, Brute Force, Lateral Tool Transfer, Command and Scripting Interpreter: Python or Password Policy Discovery
Energetic Bear
Alias: TEMP.Isotope, DYMALLOY, Berserk Bear, TG-4192, Crouching Yeti, IRON LIBERTY, Energetic Bear, Ghost Blizzard, BROMINE, Dragonfly
Energetic is another Russian state-sponsored hacker group which, like Venomous and Primitive Bear, also belongs to the Federal Security Service of the Russian Federation (FSB). This group is active worldwide.
As the name suggests, the sector most likely to be affected is the energy sector. However, the sectors Chemicals, Communications Infrastructure, Consumer Retail: Hardline (Consumer Durables), Defense Industrial Base, Digital, Print and Broadcast Media, Education: Higher Education, Financial, Services, Healthcare & Public Health, Transportation Systems: Aviation are also affected
Energetic Bear uses tools such as Trojan.Karagany, Backdoor.Oldrea and CrackMapExec, and the techniques used include account manipulation, password cracking and supply chain compromise.
Ember Bear
Alias: Saint Bear, Lorec Bear, Bleeding Bear, DEV-0586, UNC2589, UAC-0056, Lorec53, Ember Bear
Just like Fancy Bear and Voodoo Bear, Ember Bear is probably part of the General Staff of the Armed Forces of the Russian Federation (GRU). In addition to Ukraine and Georgia, Western Europe and North America are also targets of the attacks.
The three sectors are mainly target ministries, pharmaceutical companies, and financial sector
According to MITRE, the tools that could be tracked are ATT&CK WhisperGate, Saint Bot, OutSteel, as well as techniques such as Software Packing, User Execution: Malicious File, Exploitation for Client Execution
Boulder Bear
Alias: -
Another hacker group that can be linked to the Russian state is Boulder Bear. There is virtually no information on this, except that it is possibly subordinate to the Federal Security Service of the Russian Federation (FSB).
Countries or sectors at risk, as well as TTPs, are unfortunately not known.
For further research
https://www.youtube.com/watch?v=QSVQR_7fAFQ
https://cloud.google.com/blog/topics/threat-intelligence/sandworm-disrupts-power-ukraine-operational-technology/?hl=en
https://services.google.com/fh/files/misc/apt44-unearthing-sandworm.pdf
https://cloud.google.com/blog/topics/threat-intelligence/apt44-unearthing-sandworm?hl=en
https://attack.mitre.org/groups/G0034/
https://security.microsoft.com/intel-profiles/cf1e406a16835d56cf614430aea3962d7ed99f01ee3d9ee3048078288e5201bb?tab=description&tid=50271394-6aac-43fb-bd75-a0b7f111fbea
https://safereach.com/en/blog/apt44-sandworm-threat-companies/
Attacks
https://www.wired.com/story/cyber-army-of-russia-reborn-sandworm-us-cyberattacks/
https://media.defense.gov/2020/May/28/2002306626/-1/-1/0/CSA Sandworm Actors Exploiting Vulnerability in Exim Transfer Agent 20200528.pdf
https://www.justice.gov/opa/press-release/file/1328521/download
https://www.justice.gov/opa/pr/six-russian-gru-officers-charged-connection-worldwide-deployment-destructive-malware-and
Viasat
https://open.spotify.com/episode/3ad56QrgnXLuyeHfwphzC3?si=UYK32FJHSEaVvvU8n4VMPw
https://news.viasat.com/blog/corporate/ka-sat-network-cyber-attack-overview
https://www.linkedin.com/in/zhora/?originalSubdomain=ua
https://therecord.media/second-cyber-official-detained-zhora
https://www.bbc.com/pidgin/world-60598588
https://www.groundcontrol.com/blog/how-satellite-iot-closes-the-gap-in-remote-wind-turbine-data-monitoring-challenges/
NotPetya
https://blog.talosintelligence.com/worldwide-ransomware-variant/
Ukraine Electric 2016
www.dragos.com/wp-content/uploads/CrashOverride-01.pdf
https://web-assets.esetstatic.com/wls/2017/06/Win32_Industroyer.pdf
https://www.cisa.gov/news-events/ics-alerts/ir-alert-h-16-056-01
CaddyWiper (2022)
https://www.cisa.gov/news-events/analysis-reports/ar22-115c
https://www.dragos.com/blog/new-details-electrum-ukraine-electric-sector-compromise-2022/
https://www.boozallen.com/content/dam/boozallen/documents/2016/09/ukraine-report-when-the-lights-went-out.pdf
https://www.virustotal.com/gui/file/a294620543334a721a2ae8eaaf9680a0786f4b9a216d75b55cfd28f39e9430ea
https://attack.mitre.org/software/S0693/
TTPs
Neo4J
AcidRain (Viasat)
https://www.sentinelone.com/labs/acidrain-a-modem-wiper-rains-down-on-europe/
https://www.sentinelone.com/labs/acidpour-new-embedded-wiper-variant-of-acidrain-appears-in-ukraine/
https://attack.mitre.org/software/S1125/
https://www.cyberproof.com/blog/recent-developments-in-russian-ukrainian-cyber-warfare
Industroyer
https://www.incibe.es/en/incibe-cert/blog/industroyer2-ampere-strikes-back
https://www.welivesecurity.com/2022/04/12/industroyer2-industroyer-reloaded/
https://cloud.google.com/blog/topics/threat-intelligence/industroyer-v2-old-malware-new-tricks?hl=en
https://attack.mitre.org/software/S0604/
https://www.cisa.gov/news-events/ics-alerts/ics-alert-17-206-01
https://web-assets.esetstatic.com/wls/2017/06/Win32_Industroyer.pdf
https://www.dragos.com/wp-content/uploads/CrashOverride-01.pdf
https://attack.mitre.org/software/S0604/
https://attack.mitre.org/software/S1072/
NotPetya
https://attack.mitre.org/software/S0368/
https://www.secureworks.com/blog/notpetya-campaign-what-we-know-about-the-latest-global-ransomware-attack
https://www.cloudflare.com/learning/security/ransomware/petya-notpetya-ransomware/
https://www.cisa.gov/news-events/alerts/2017/07/01/petya-ransomware
https://analyze.intezer.com/files/027cc450ef5f8c5f653329641ec1fed91f694e0d229928963b30f6b0d7d3a745
https://www.virustotal.com/gui/file/027cc450ef5f8c5f653329641ec1fed91f694e0d229928963b30f6b0d7d3a745/relations
https://www.microsoft.com/en-us/security/blog/2017/10/03/advanced-threat-analytics-security-research-network-technical-analysis-notpetya/
Hunting
Acid Rain
https://github.com/RustyNoob-619/100-Days-of-YARA-2024/blob/main/Day80.yar
https://www.virustotal.com/gui/file/6a8824048417abe156a16455b8e29170f8347312894fde2aabe644c4995d7728/detection
Industroyer
https://github.com/intezer/yara-rules/blob/master/RussianAPT.yar
NotPetya
https://gist.github.com/vulnersCom/65fe44d27d29d7a5de4c176baba45759