Securing the Digital Frontier: Strategies Against the Rising Tide of Ransomware Threats
In the digital age, the threat landscape evolves with alarming speed, and ransomware groups are at the forefront of this change, wreaking havoc on businesses and individuals alike. 2023 has seen an unprecedented rise in ransomware attacks, with groups like LockBit, BlackCat, and Clop leading the charge. These entities have not only targeted a wide array of industries but have also demonstrated a chilling efficiency and sophistication in their operations.
The Evolving Threat Landscape
The ascendency of groups such as LockBit, AlpVM, and CLOP has been particularly notable, with these groups significantly outpacing others in terms of victimology. Industries such as healthcare, automotive, real estate, and legal have found themselves in the crosshairs, underscoring a shift towards sectors where the impact—and potential payouts—are greatest.
A staggering statistic from Malwarebytes reveals that in a single year, 1,900 ransomware attacks occurred within just four countries: the US, Germany, France, and the UK, with the US bearing a disproportionate share of this burden. The CL0P group, in particular, has made headlines for its use of zero-day vulnerabilities to launch attacks, highlighting a shift towards more aggressive, vulnerability-focused tactics.
The Top 5 Ransomware Groups of 2023: Tactics and Dangers Unveiled
In the shadowy world of cyber threats, certain ransomware groups have distinguished themselves through their prolific activities and sophisticated attacks. Here, we delve into the top 5 ransomware groups of 2023, exploring their modus operandi and the unique threats they pose.
1. LockBit
- Tactics: LockBit operates on a ransomware-as-a-service (RaaS) model, allowing affiliates to deploy the ransomware. They are known for their speed in encrypting files and have a self-spreading feature, which increases the infection rate within networks.
- Dangers: Their use of a double extortion scheme, where they threaten to publish stolen data unless a ransom is paid, combined with their swift encryption, makes them particularly dangerous. The launch of LockBit 3.0 has further enhanced their capabilities.
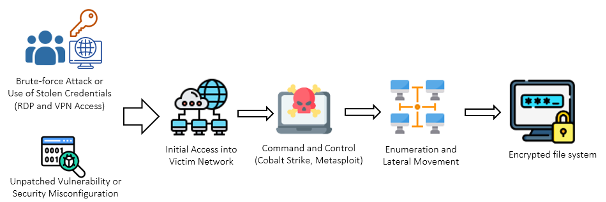
2. BlackCat/ALPHV
- Tactics: BlackCat, also known as ALPHV, is credited with being one of the first ransomware groups to be written in Rust, offering enhanced performance and evasion capabilities. They utilize sophisticated encryption methods and are known for their selective targeting of victims.
- Dangers: Their ability to customize attacks based on the victim’s environment and negotiate ransoms through their leak site adds a level of professionalism and persistence to their operations. Their targeting is often based on the victim's ability to pay, leading to significant financial demands.
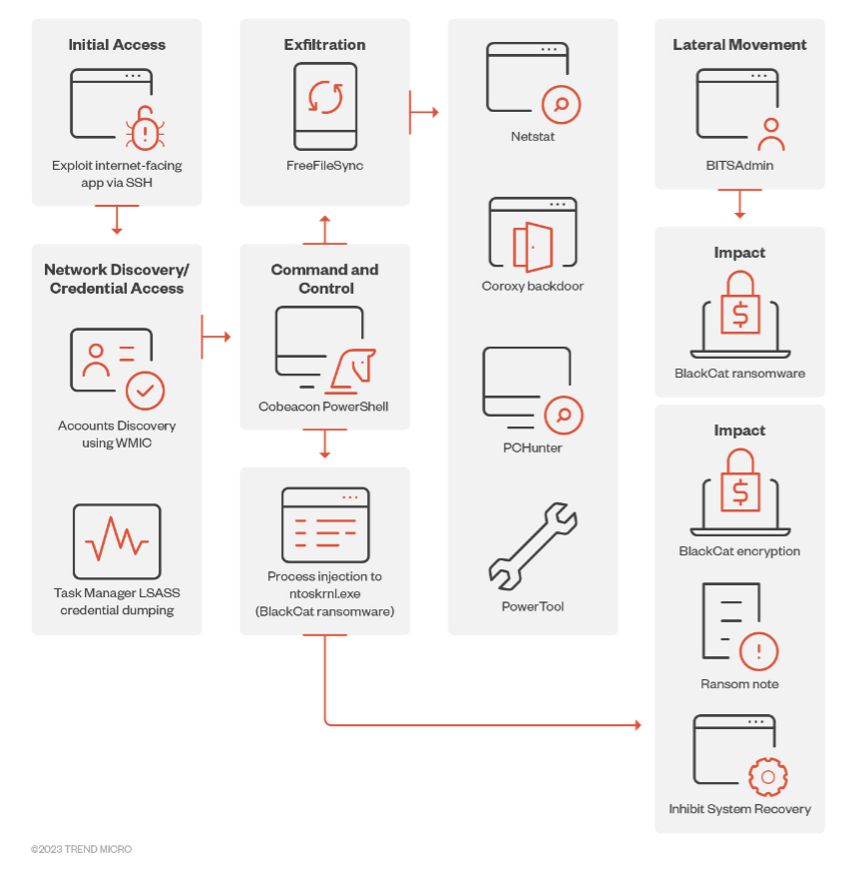
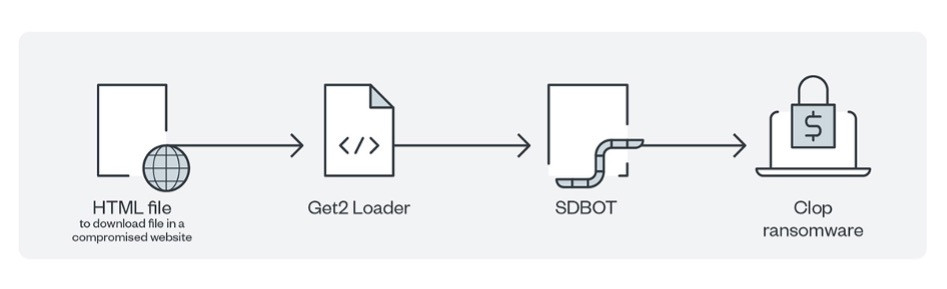
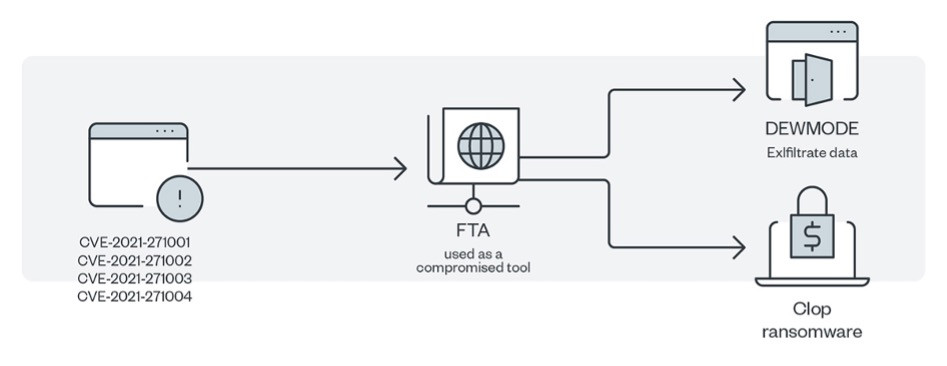
3. Clop
- Tactics: Clop focuses on exploiting vulnerabilities in software to gain access to networks. They have been associated with attacks on supply chain companies, aiming to compromise multiple victims through a single entry point.
- Dangers: The group is notorious for its "big game hunting" strategy, targeting large corporations for maximum ransom. Their use of zero-day vulnerabilities and focus on disabling security processes make their attacks particularly hard to detect and mitigate.
4. BianLian
- Tactics: BianLian stands out not only for its aggressive direct extortion tactics but also for its use of sophisticated encryption methods. Specifically, BianLian employs AES-256 encryption to lock the data of their victims. This level of encryption, known for its robustness and complexity, ensures that decrypting the affected files without the proper key is virtually impossible, thereby increasing the pressure on victims to comply with ransom demands.
- Dangers: The combination of direct communication with victims' stakeholders and the unyielding nature of AES-256 encryption substantially raises the stakes, impacting both the operational capabilities and reputational integrity of targeted organizations.
- Decryption Tool: In a significant stride towards mitigating the impact of BianLian, Avast has developed a decryption tool, offering a beacon of hope for recovery. This tool signifies the cybersecurity community's ongoing efforts to provide solutions for ransomware victims, enabling them to potentially recover their encrypted data without yielding to financial extortion.
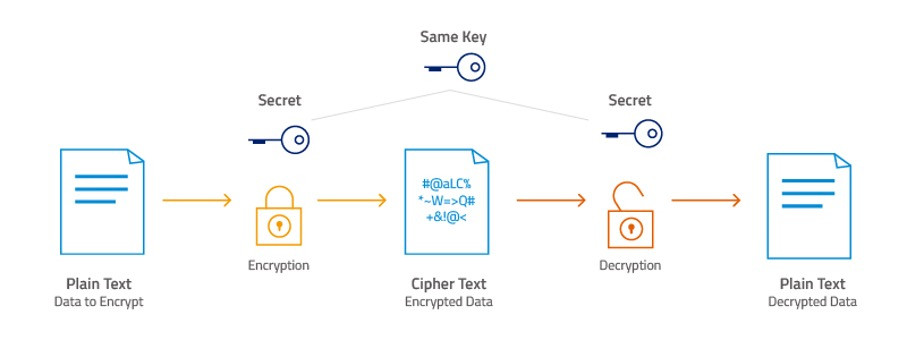
5. Play
- Tactics: Play ransomware is characterized by its use of sophisticated obfuscation techniques to evade detection and its aggressive encryption speed. They also leverage double extortion and have been observed targeting a wide range of sectors.
- Dangers: Their broad targeting strategy and fast encryption capabilities increase the likelihood of successful attacks across various industries. The group's adaptability and the use of obfuscation techniques make Play ransomware a formidable threat to organizations worldwide.
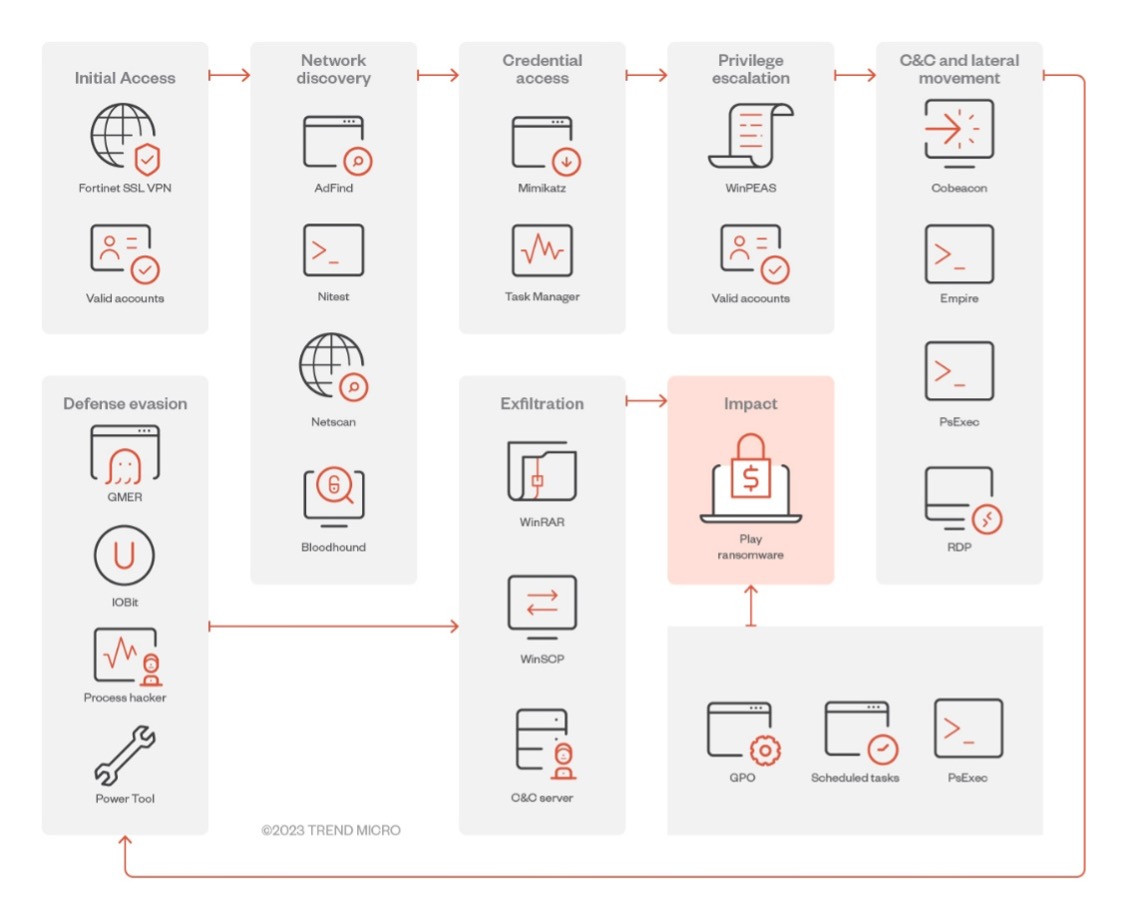
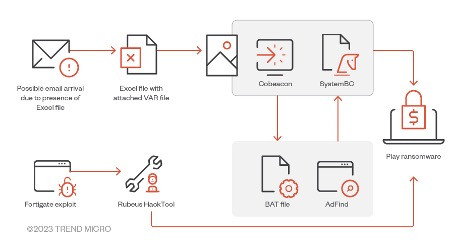
These groups have set themselves apart not just through the volume of their attacks but through their innovative tactics and ruthless extortion strategies. The evolution of their techniques highlights the need for constant vigilance and advanced cybersecurity measures to protect against these ever-evolving threats.
Countermeasures: Fortifying Defenses with Decryption Tools
In an era where digital threats loom larger by the day, understanding and combatting ransomware has become a critical battleground for cybersecurity. This blog post delves into the sophisticated mechanisms of modern ransomware groups, highlighting their tactics, the encryption technologies they wield, and the profound impacts on affected organizations. More importantly, it outlines a comprehensive blueprint for defense, emphasizing advanced detection systems, robust email security, stringent access controls, and the significance of continuous employee training. It also showcases the crucial role of decryption tools, such as Avast's solution for BianLian, in the recovery process, offering a glimmer of hope in the shadow of ransomware's menace.
- Introduction to Enhanced Defense Measures: Start with a compelling introduction that sets the stage for a deep dive into advanced cybersecurity measures, highlighting the ever-evolving nature of ransomware threats and the paramount importance of staying ahead with innovative defense strategies.
- Advanced Threat Detection Systems: Elaborate on the use of AI and machine learning in detecting patterns and behaviors typical of ransomware attacks, explaining how these technologies can preemptively flag and neutralize threats before they manifest.
- Robust Email Security Protocols: Detail the significance of sophisticated email security solutions in intercepting phishing attempts, with an emphasis on the role of sandboxing, URL rewriting, and attachment scanning in mitigating entry points for ransomware.
- Access Control and Network Segmentation: Discuss the criticality of implementing least privilege access controls combined with strategic network segmentation to limit the blast radius of potential ransomware attacks, thereby safeguarding critical assets.
- Patch Management Program: Stress the importance of a proactive patch management strategy, covering how regular updates serve as a critical barrier against exploits targeting known vulnerabilities.
- Endpoint Protection Platforms (EPP): Dive into the functionalities of modern EPPs, including ransomware rollbacks and behavioral blocking, to protect endpoints from being compromised.
- Employee Cybersecurity Training: Outline a continuous training program focused on equipping employees with the knowledge to identify and avoid ransomware threats, emphasizing the role of simulated phishing exercises and security awareness training.
- Utilization of Decryption Tools: Highlight specific examples, such as Avast’s decryption tool for BianLian, showcasing the importance of these tools in recovery efforts post-attack. Explain how decryption tools, when available, can serve as a lifeline, allowing for the recovery of encrypted files without paying the ransom.
For each of these points, it's recommended to integrate insights and recommendations based on the latest research and developments in the field of cybersecurity, as provided by authoritative sources like Trend Micro, the Australian Cyber Security Centre, Avast, and others. This enriched narrative not only informs but also empowers organizations to build and maintain resilient defenses against the scourge of ransomware.
Conclusion
The rise of ransomware groups in 2023 is a clear call to action for organizations worldwide. The need for comprehensive cybersecurity measures has never been greater, as the methods and targets of these groups continue to evolve. By understanding the threat landscape and implementing robust security practices, businesses can navigate these turbulent waters with greater confidence and security.
Sources
- ChatGPT 4.0
- https://www.nomoreransom.org/en/decryption-tools.html
- https://www.domaintools.com/resources/blog/the-most-prolific-ransomware-families-2023-edition/
- https://www.malwarebytes.com/blog/threat-intelligence/2023/08/global-ransomware-attacks-at-an-all-time-high-shows-latest-2023-state-of-ransomware-report
- https://www.trendmicro.com/vinfo/us/security/news/ransomware-by-the-numbers/lockbit-blackcat-and-clop-prevail-as-top-raas-groups-for-1h-2023
- https://www.rapid7.com/blog/post/2024/01/12/2023-ransomware-stats-a-look-back-to-plan-ahead/
- https://www.trendmicro.com/vinfo/us/security/news/ransomware-spotlight/ransomware-spotlight-play
- https://www.cyber.gov.au/about-us/advisories/2023-03-asdacsc-ransomware-profile-lockbit-3.0
- https://www.trendmicro.com/vinfo/us/security/news/ransomware-spotlight/ransomware-spotlight-blackcat
- https://www.trendmicro.com/vinfo/us/security/news/ransomware-spotlight/ransomware-spotlight-clop
- https://decoded.avast.io/threatresearch/decrypted-bianlian-ransomware/
- https://www.atpinc.com/blog/what-is-aes-256-encryption
- https://twitter.com/vxunderground/status/1759703708785365068?t=7BHPD7CVK0cVWVZryjMm6A
- https://twitter.com/bfv_bund/status/1759488623060173098?t=7BHPD7CVK0cVWVZryjMm6A
- https://twitter.com/vxunderground/status/1759708760929390879?t=7BHPD7CVK0cVWVZryjMm6A
- https://twitter.com/uk_daniel_card/status/1759685711974871484?t=7BHPD7CVK0cVWVZryjMm6A
- https://twitter.com/osintindustries/status/1759722450126864465?t=7BHPD7CVK0cVWVZryjMm6A


