Cyber Briefing 08/2023
What to expect here in the future
We see an increasing demand for information on current CVEs, APTs, malware, etc.. The newsletter will be our way to satisfy this demand and focus on threats, which are relevant to our customers.
Windows Master Key
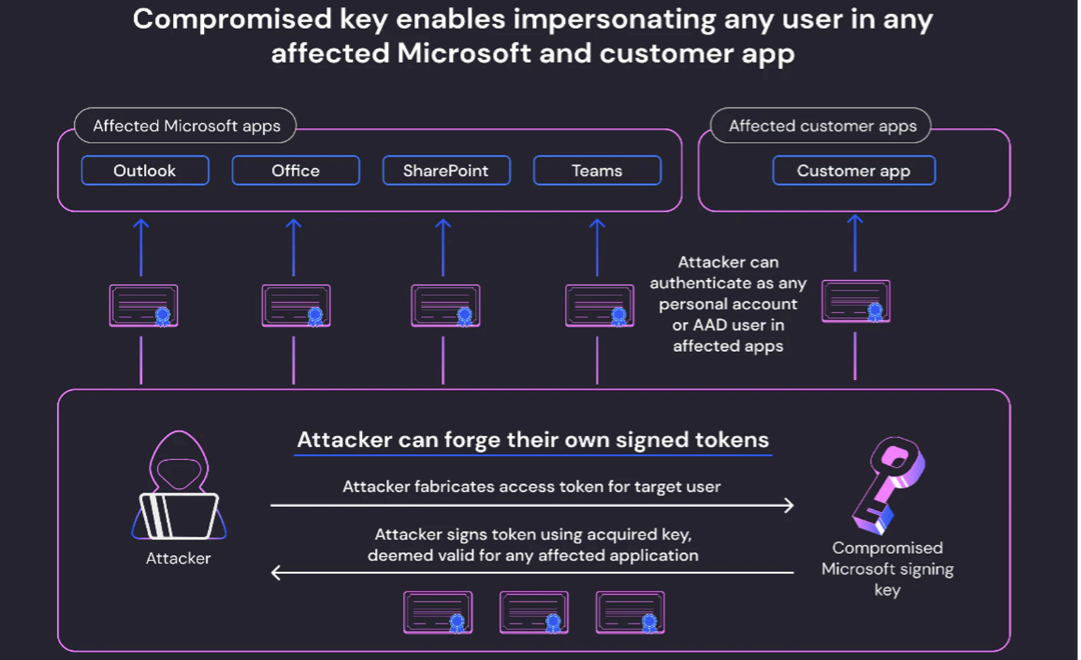
The threat actor Storm-0558 seemingly acquired a private encryption key (MSA key) and used it to forge access tokens for various Microsoft and customer apps.
Since the acquired signing key has already been invalidated by Microsoft, no immediate risk to customers remains.
To mitigate this vulnerability, Microsoft advises customers to install the Windows update that is dated on or after August 8, 2023. The resolution included in this update is enabled by default. No further action is required.
Since Microsoft is very sparse with information about affected customers, the true impact of this vulnerability is hard to determine.
Compromised Microsoft Key: More Impactful Than We Thought
Stolen Microsoft key offered widespread access to Microsoft cloud services
Analysis of Storm-0558 techniques for unauthorized email access
Microsoft mitigates China-based threat actor Storm-0558 targeting of customer email
KB5028407: How to manage the vulnerability associated with CVE-2023-32019 - Microsoft Support
CVE-2023-38408 - OpenSSH
The PKCS#11 feature in ssh-agent in OpenSSH before 9.3p2 has an insufficiently trustworthy search path, leading to remote code execution (RCE) if an agent is forwarded to an attacker-controlled system. This issue exists because of an incomplete fix for CVE-2016-10009. SSH-agent forwarding is still widely used, even though the manual page of the SSH-Agent (man ssh-agent) warns about this.
(man ssh-agent) 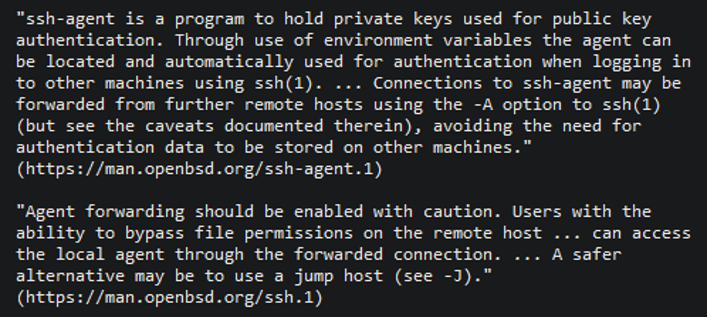
To mitigate this risk, users should update OpenSSH to the latest version (9.3p2 or greater).
If remote access is necessary: Configure a secure virtual private network (VPN) service and restrict it to the device.
CVE-2023-38408: Remote Code Execution in OpenSSH’s forwarded ssh-agent
Current Phishing related threats
Phishing is still one of the most relevant threats and often used for initial access, VirusTotal reports that attackers are constantly developing new ways to improve the ways to phish targets, that do not stay vigilant. Email attachments continue to be one of the most popular methods of malware delivery, but new types of file attachments, especially OneNote and ISO files have increased in popularity.
Another current trend of phishing stems from the name change of Twitter to X, which gave threat actors the chance to register new, similar sounding domains, which allows several different types of attacks, like credential harvesting and phishing attacks.
VirusTotal Malware Trends Report: Emerging Formats and Delivery Techniques
QwixxRAT
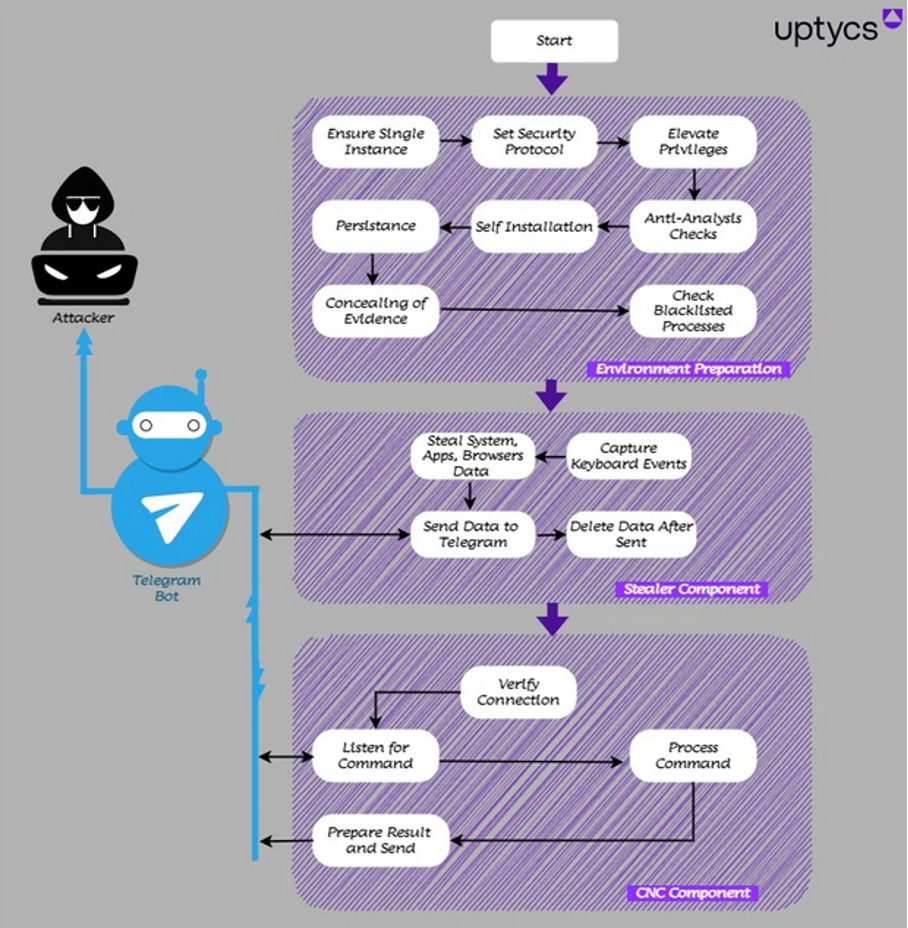
QwixxRAT, a new Windows remote access trojan (RAT), is being sold on Telegram and Discord platforms. Discovered by the Uptycs Threat Research team in early August 2023, this RAT can gather sensitive data and relay it to an attacker's Telegram bot.
Once installed on a victim's Windows machine, the RAT discreetly collects data, which is then sent to the attacker's Telegram bot, granting unauthorized access to the victim's information. The malware is designed to steal a wide array of data, including browser histories, credit card details, and keystrokes. It's available for purchase with both weekly and lifetime subscription options.
Beware of Knight Ransomware Masquerading as TripAdvisor Complaints
Knight ransomware is currently spreading via misleading spam emails that pose as TripAdvisor complaint notifications.
Originating from the rebranded Cyclop Ransomware-as-a-Service in late July 2023, these deceptive emails come with attachments labeled 'TripAdvisorComplaint.zip' or 'TripAdvisor-Complaint-[random].PDF.htm'.
Unwary users who open these attachments unknowingly activate the ransomware, leading to the encryption of their files with an added ".knight_l" extension. Subsequently, a ransom demand of $5,000 in Bitcoin appears, but due to the unpredictability of obtaining a decryption solution, experts recommend not paying.
Knight ransomware distributed in fake Tripadvisor complaint emails
Emergence of the INC Ransom Group: A New Threat on the Horizon
The INC Ransom group has recently emerged as a significant actor in the ransomware landscape. Gaining swift recognition, this group targets entities likely motivated to pay ransoms due to reputational concerns or the critical nature of their data, as evidenced by their public victim listings on a dedicated leak site. Their intricate attack sequence spans about a week, from initial access to the final file encryption phase. Integral to their strategy are steps like data collection, staging, and exfiltration, all preceding the ransomware deployment.
Given the rising threat, organizations are urged to heighten their vigilance and bolster cybersecurity defenses.
IoCs and MITRE Tactics can be seen at Investigating New INC Ransom Group Activity
Citrix
Citrix NetScaler, a key enterprise solution, has faced a significant breach, with nearly 2,000 instances compromised due to a critical security flaw
This vulnerability, termed as CVE-2023-3519, impacts NetScaler Application Delivery Controller (ADC) and Gateway servers, enabling unauthenticated remote code execution.
While many European countries have been affected, a majority of the compromised instances are in Germany. Citrix addressed this flaw last month, but many servers, even those patched, remain vulnerable, if remaining malware, webshells, or other means of unwanted access remain on the systems. It's crucial for administrators, especially in Germany, to both patch, inspect for potential breaches, and remove any remaining malicious entities.
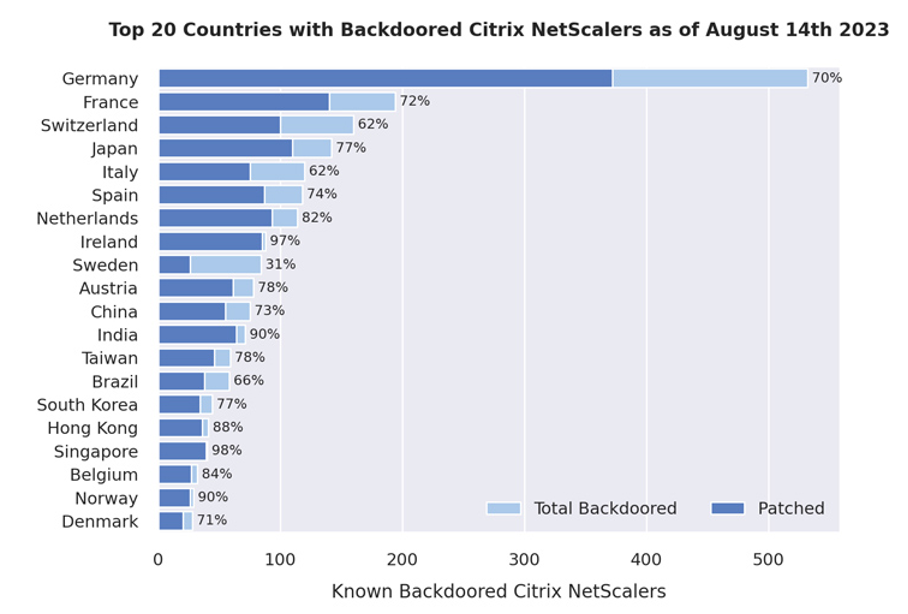
Nearly 2,000 Citrix NetScaler Instances Hacked via Critical Vulnerability