CVE-2023-38831 & CVE-2023-40477 - WinRAR Zero-days
Introduction
CVE-2023-38831 identifies a file extension spoofing vulnerability in WinRAR, a popular Windows tool for compressing and decompressing files. This flaw allowed clever individuals to create ZIP or RAR files that appeared ordinary but were structured in a way that concealed malicious code. By exploiting this vulnerability, the seemingly harmless file extensions, such as .jpg or .txt, could be used to hide and execute harmful scripts. When an unsuspecting user opened one of these disguised files, the hidden code was triggered, leading to potential unauthorized activities on the user's computer.
The severity score of the CVE-2023-38831 is 7.8, which is categorized as HIGH according to the CVSS (Common Vulnerability Scoring System) Version 3.x.
What is WinRAR
WinRAR, a Windows-exclusive archive manager, is widely known for two of its main features: the ability to create and extract file archives in a multitude of compression formats, including RAR, ZIP, CAB, ARJ, LZH, TAR, GZ, TAR.GZ, BZ2, TAR.BZ2, UUE, JAR (Java Archive), ISO (ISO9660 - CD image), 7Z, XZ, and Z (Unix compress).
Affected Versions and Applications
Any version of WinRAR prior to 6.23 is impacted by the CVE-2023-38831 zero-day vulnerability. To address the issue, an updated WinRAR version (6.23) was launched on August 2, 2023.
Exploit Steps
The CVE-2023-38831 vulnerability is a file extension spoofing vulnerability that allows attackers to create malicious RAR or ZIP archives.
The exploit works as follows:
- Threat actors create malicious .RAR and .ZIP archives that display seemingly innocuous files, such as JPG (.jpg) images, text files (.txt), or PDF (.pdf) documents. This allows them to spoof file extensions and hide the launch of malicious scripts.
- The archives are distributed on cryptocurrency and stock trading forums, where malicious actors pretend to be enthusiasts sharing trading strategies. Forum posts contain links to specially crafted WinRAR ZIP or RAR archives that pretend to include shared trading strategies, consisting of PDFs, text files, and images.
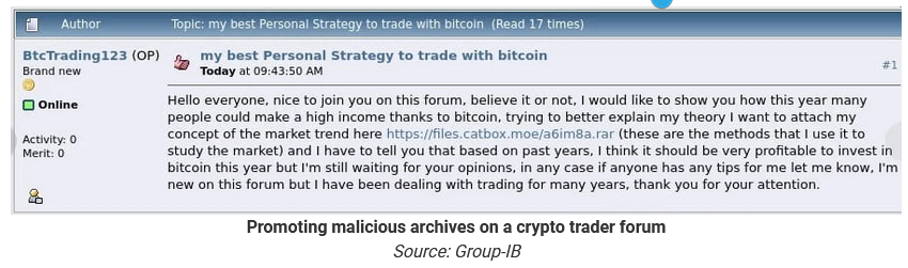
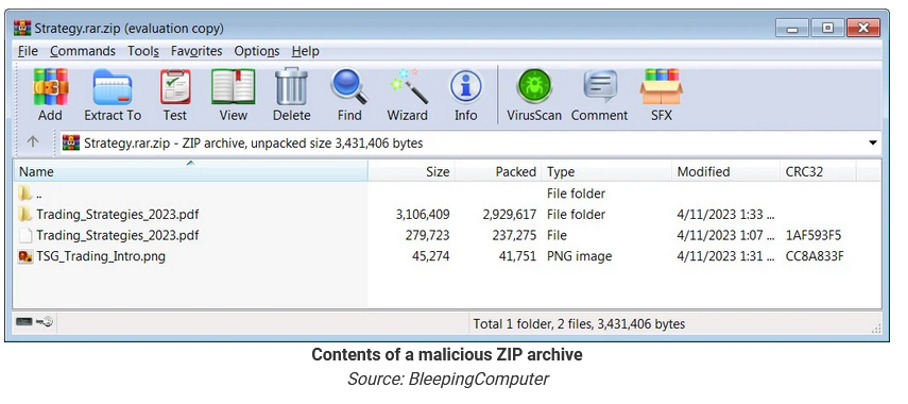
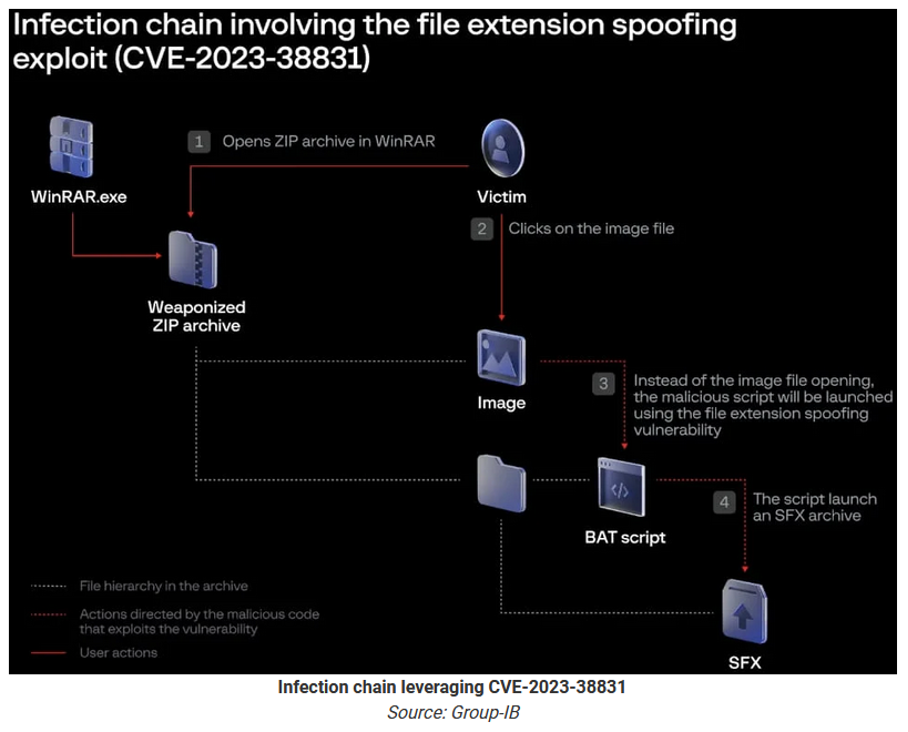
- When a user opens a decoy file within the archive with WinRAR, the flaw causes a script to be executed that installs malware on the device. If the user double-clicks on a seemingly harmless file, like a PDF, the CVE-2023-38831 vulnerability quietly launches a script to install malware, simultaneously loading the decoy document to avoid suspicion.
- The vulnerability is activated when malicious actors create special archive files (like ZIP or RAR files) that are slightly different from normal, safe files. This small change in the structure of the file confuses WinRAR's function called 'ShellExecute.' When WinRAR tries to open what looks like a regular file (the decoy), this confusion causes it to receive wrong instructions or parameters. As a result, instead of opening the expected file, WinRAR ends up executing a malicious script hidden within the archive.
- The script executes to launch a self-extracting (SFX) CAB archive, infecting the computer with various malware strains such as DarkMe, GuLoader, or Remcos RAT. These provide remote access and various control capabilities over infected devices, including arbitrary command execution, keylogging, screen capturing, file management, and reverse proxy capabilities.
- After infecting the devices, the cybercriminals withdraw money from broker accounts. The total amount of financial losses is still unknown.
Impact and Targets
The WinRAR vulnerability (CVE-2023-38831) poses a significant threat that extends far beyond the realm of cryptocurrency traders. While the exploitation of this file extension spoofing vulnerability has been observed in targeting cryptocurrency and stock trading forums, its potential impact is much broader.
Everyday computer users who rely on WinRAR for handling compressed files are at risk. The deceptive nature of the vulnerability, where malicious code is hidden behind seemingly harmless file extensions, means that anyone downloading and opening compressed files from various sources could inadvertently trigger harmful scripts.
Banks and other financial entities are also potential targets. The ability to execute hidden malicious code could lead to unauthorized access to financial accounts, illicit transactions and theft of sensitive financial information. The implications for both the institutions and their customers could be severe.
Companies across various industries that utilize WinRAR for file compression and extraction may find their sensitive or proprietary information at risk. Whether it's intellectual property, customer data or internal communications, exploitation of this vulnerability could lead to significant business disruptions and reputational damage.
In summary, while cryptocurrency traders have been specific targets, the danger posed by the WinRAR vulnerability is far-reaching. Its potential to conceal and execute malicious code within ordinary-looking files makes it a versatile and insidious threat that could affect a wide range of individuals and organizations across different sectors. The discovery of this vulnerability underscores the importance of vigilance, regular software updates, and a comprehensive understanding of the risks associated with even widely trusted tools like WinRAR.
Mitigations
- The zero-day was fixed in WinRAR version 6.23, released on August 2, 2023. Users of WinRAR are urged to upgrade to the latest version as soon as possible to eliminate the risk of file spoofing and other recently-disclosed attacks.
- Users should be cautious when opening files from unknown sources, especially those shared on trading forums or other public platforms.
- If you suspect you may have been targeted, monitor your trading accounts and devices for any suspicious activity.
- Employing robust security solutions that can detect and block malicious files can further reduce the risk of exploitation.
EvilNum Group
The EvilNum group has been active since at least 2018, with the primary goal to spy on targets and steal financial data. Some key details include:
Although DarkMe has been associated with financially motivated attacks by the EvilNum group, it's unclear who leveraged CVE-2023-38831 in the recent campaign.
The group may target traders to steal their crypto assets.
In 2019, a WinRAR vulnerability (CVE-2018-20250) was exploited by attackers to deliver persistent malware.
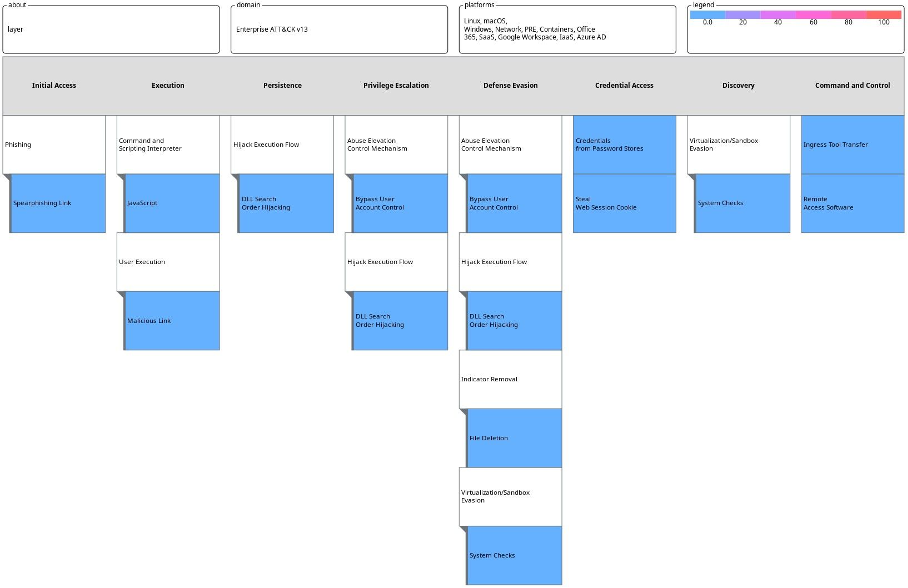
TTPs used by the group are as follows:
IoCs
Domains
• 87iavv[.]com
• tganngs9[.]com
• trssp05923[.]com
• 12jyyu06[.]com
• corialopolova[.]com
• mmnedgeggrrva[.]com
IP addresses
• 45.74.19[.]96
• 45.74.19[.]89
• 45.74.19[.]87
• 45.74.19[.]105
• 91.148.135[.]198
• 153.92.126[.]196
• 51.195.57[.]234
Registry path
• HKCU\Software\Microsoft\Windows\CurrentVersion\Run\RunDll
• HKCU\Software\Microsoft\Windows\CurrentVersion\Run\Logintech_000001
• HKCU\Software\Microsoft\Windows\CurrentVersion\Run\anatomicobiological
File path
• %APPDATA%\WinSoft\Cabinet.ocx
• %APPDATA%\Nvidia\Core.ocx
• %APPDATA%\RarDir\ClassFile.ocx
• %APPDATA%\DefaultDirectory\Cabinet.ocx
• %APPDATA%\NvidiaCore\Newest.dll
Files
• Trading_Strategy_2023.rar (763df8b2db7f2f2fa0c8adb8c1cc05ff15b59e6a9756cbe9fc4a1c12329b62af)
• Cryptocurrencies2023.rar
Cryptocurrencies2023_mpgh.net.rar
(0860e09e529fc6ccbbffebafedc27497fbbcaff57b5376fb4cc732c331d1f591)
• Screenshot_19_04_2023.rar (18129626041b90558607eec67616ba6d2b1ea28a280c7ba5b2bd30ebb1e2438b)
There are a couple more indicators, which can be found at the following website:
https://www.group-ib.com/blog/cve-2023-38831-winrar-zero-day/
Related Threats
CVE-2023-40477 Description:
Severity: CVSS score of 7.8
Impact: Remote Code Execution (RCE) on affected systems.
Technical Details:
The affected software is WinRAR, a utility used extensively on Windows systems for creating and extracting file archives. The vulnerability arises from improper validation procedures while the software processes recovery volumes. Specifically, the lack of proper validation of user-supplied data can result in unauthorized memory access beyond the end of an allocated buffer.
Exploitation:
Exploiting this vulnerability requires user interaction. Specifically, the target user must be lured into either visiting a malicious webpage or opening a booby-trapped archive file. Despite requiring user interaction, the flaw can be exploited remotely, enabling attackers to execute arbitrary code within the context of the current process.
Mitigation:
The vulnerability has been addressed in the latest WinRAR version 6.23, released on August 2, 2023. It is recommended that users manually update to this version as soon as possible, especially since WinRAR does not offer an auto-update feature.
References
https://thehackernews.com/2023/08/new-winrar-vulnerability-could-allow.html
https://thehackernews.com/2023/08/winrar-security-flaw-exploited-in-zero.html
https://www.helpnetsecurity.com/2023/08/21/cve-2023-40477/
https://www.group-ib.com/blog/cve-2023-38831-winrar-zero-day/
https://nvd.nist.gov/vuln/detail/CVE-2023-38831
https://techcrunch.com/2023/08/23/winrar-zero-day-funds-brokers/?guccounter=1


